Manage User Sessions and Logout¶
This page guides you through managing user sessions and logout for OpenID Connect applications with WSO2 Identity Server.
Register a service provider¶
To register your application as a service provider in the WSO2 Identity Server:
-
Log in to the WSO2 Identity Server Management Console using administrator credentials.
-
Go to Main > Identity > Service Providers > Add.
-
Enter a Service Provider Name. Optionally, enter a Description.
-
Click Register.
Make the following changes to the created service provider.
-
Expand Inbound Authentication Configuration > OAuth/OpenID Connect Configuration and click Configure.
-
Enter the Callback Url.
Note
The Callback Url is the exact location in the service provider's application to which an access token will be sent. This URL should be the URL of the page that the user is redirected to after successful authentication.
-
Click Add. Note the OAuth Client Key and OAuth Client Secret that appear.
Configure to sign the ID token with the user's tenant domain¶
-
Expand the Local & Outbound Authentication Configuration section and select Use tenant domain in local subject identifier to sign the ID token with the user's tenant domain.
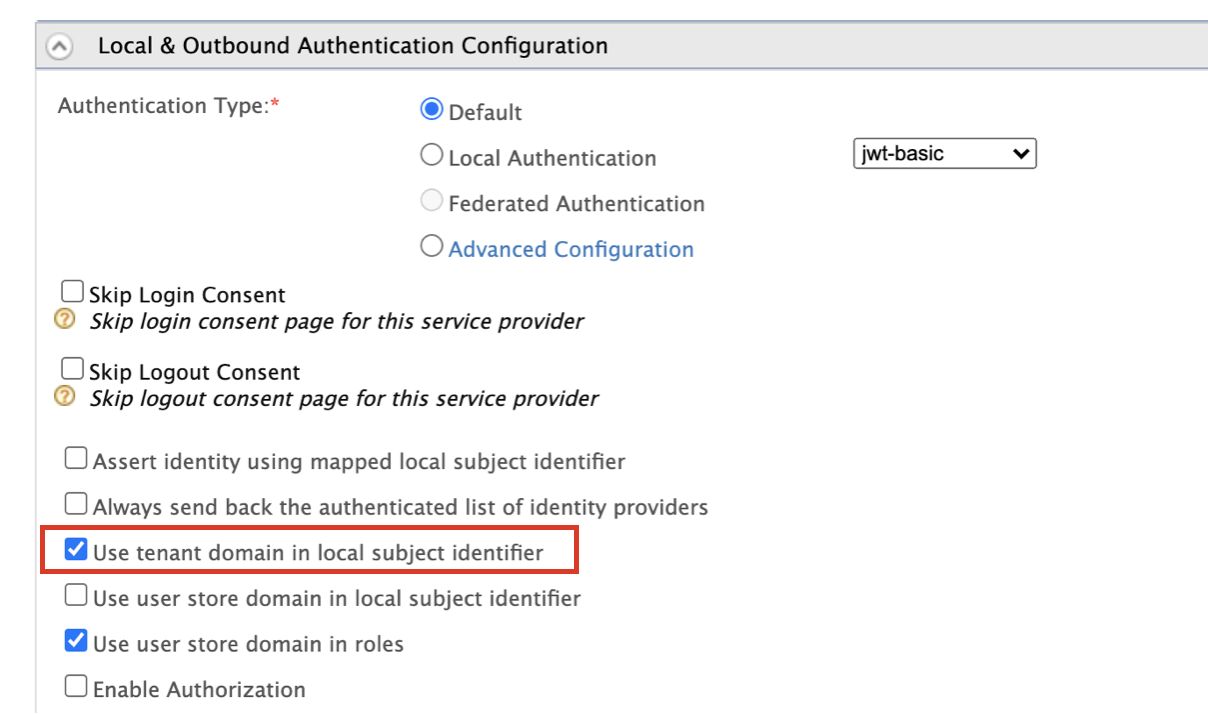
-
Click Update to save the changes.
Note
Alternatively, to sign the ID token with the service provider's
tenant domain, open the deployment.toml file
found in the <IS_HOME>/repository/conf folder and
set the following property to true.
[oauth.oidc.id_token]
sign_with_sp_key=trueKeep the user session live¶
In WSO2 Identity Server, you can use an authorization endpoint to increase the session idle time.
To do this, add an iframe to the service provider application which sends a prompt=none call to the OAuth2 authorization endpoint after each iteration of n minutes and refreshes the user session at the server-end. A sample iframe is shown below.
<iframe id="refresh_iframe" src="#" style="width:0;height:0;border:0; border:none;"></iframe><script>setInterval(function(){document.getElementById('refresh_iframe').src
="https://localhost:9443/oauth2/authorize prompt=none&scope=openid&response_type=code&redirect_uri=http%3A%2F%2Flocalhost%3A8080%2Fplayground2%2Fprompt-none callback.jsp&client_id=7x72byIYC40dlCuu6bovOTdK2MMa";},300000);</script>Try it¶
Set up the sample¶
-
Download Apache Tomcat 8.x from here and install. Tomcat server installation location will be referred as
<TOMCAT_HOME>later in this guide. -
It is recommended that you use a hostname that is not
localhostto avoid browser errors. Modify the/etc/hostsentry in your machine to reflect this. Note thatwso2is.localis used in this documentation as an example, but you must modify this when configuring the authenticators or connectors with this sample application. -
Download the sample from GitHub.
-
Navigate to WSO2 Identity Server Samples.
-
Download the
playground2.warfile from the latest release assets.
-
Deploy the sample¶
Deploy this sample web app on a web container.
-
Copy the
playground2.warfile from the latest release assets folder into the<TOMCAT_HOME>/apache-tomcat-<version>/webappsfolder. -
Start the Tomcat server.
Note
To check the sample application, navigate to
http://<TOMCAT_HOST>:<TOMCAT_PORT>/playground2/oauth2.jspon your browser.For example,
http://wso2is.local:8080/playground2/oauth2.jsp -
Update the
param-valueparameter in theWEB-INF/web.xmlfile with the server URL of WSO2 Identity Server if required.Make sure to enter the port the application is running on, in the URL. If you have started the Identity Server with a port offset, then the respective port needs to be configured here.
<init-param> <description>serverUrl</description> <param-name>serverUrl</param-name> <param-value>https://localhost:9443/services/</param-value> </init-param>Note
Note that
localhostis the server that hosts WSO2 Identity Server and9443is the default SSL port of it. Since playground application is accessing the admin serviceOAuth2TokenValidationService, you should have the correct serverUrl, username, and password. -
Update
param-valueparameter with credentials of an admin user if required.<init-param> <description>userName</description> <param-name>userName</param-name> <param-value>admin</param-value> </init-param> <init-param> <description>password</description> <param-name>password</param-name> <param-value>admin</param-value> </init-param> -
Restart Apache Tomcat and access
http://wso2is.local:8080/playground2/.By default Tomcat runs on port 8080. If you have configured it to run on a different port make sure to update the URL and then access the playground application.
Log out¶
-
Enter the following values and click Authorize.
- Authorization Grant Type: Authorization Code (with this sample you can only test OIDC for the Authorization Code flow)
- Client Id: Enter the client ID (OAuth Client Key under Registering the relying Application, step 4) of the registered playground2 application
- Scope:
openid - Callback URL:
http://wso2is.local:8080/playground2/oauth2client - Authorize Endpoint:
https://localhost:9443/oauth2/authorize - Logout Endpoint:
https://localhost:9443/oidc/logout - Session Iframe Endpoint:
https://localhost:9443/oidc/checksession?client_id=<clientID of playground2 application>
-
Log in with the user credentials and click Approve Always at the consent page.
In order to enable single logout (SLO) you must use the Approve Always option. If this is not done, the passive request will not work, and without passive requests, the SLO protocol will not work. Do this to avoid errors during execution.
-
Once it is successfully authenticated, the OpenIDConnect Provider(OP) will redirect back to the client application with the authorization code and the session state. You can see this in the logs of the console, as seen below.
-
Enter the following values and click Get Access Token to receive the ID token and access token.
- Callback URL:
http://wso2is.local:8080/playground2/oauth2client - Access Token Endpoint:
https://localhost:9443/oauth2/token - Client Secret: Enter the client secret of playground2 application
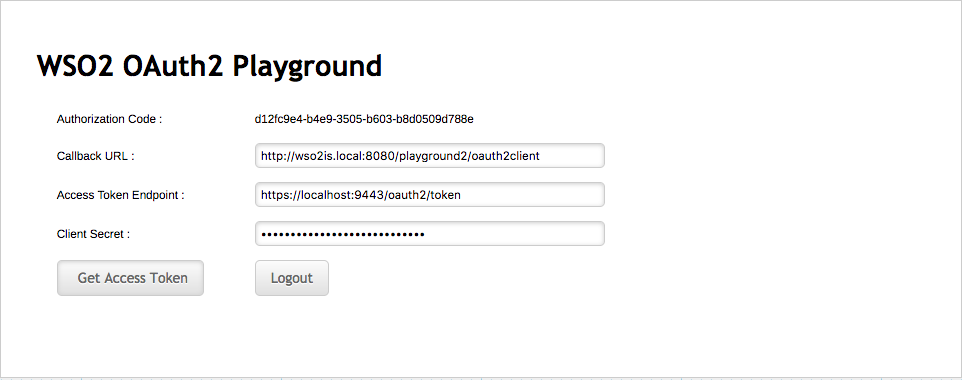
- Callback URL:
-
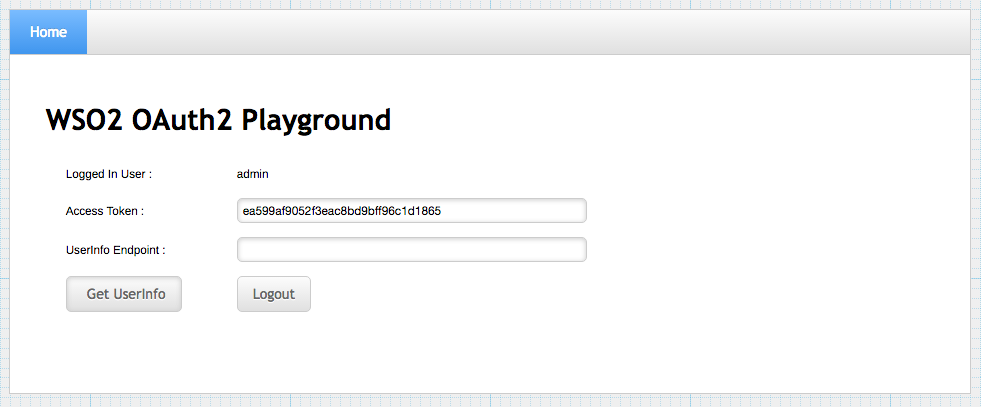
You will receive the access token. You can also enter the UserInfo Endpoint as
https://localhost:9443/oauth2/userinfoto use the received access token to obtain user claims if needed.
-
Access the following URL on a separate window of the browser, and click on Import Photos:
http://wso2is.local:8080/playground2/Note
For this scenario we need two relying party applications. To do this, make a copy of the playground2.war file that was generated when you set up the sample webapp, and rename it as playground3.war in the same location. Repeat the above steps for the playground3 application.
-
Repeat steps 2-6 to invoke the playground3 application. Make sure to change the Callback URL, Client Id and Client secret corresponding to playground3 application when you follow the steps.
Tip
Step 3 will not be prompted to you as there is already a valid session and WSO2 Identity Server will apply SSO for the second application.
-
Once you receive the authorization code for the playground3 app, open the browser console of the playground2 app. You will see that the RP iframe of playground2 has initiated a passive authentication request as the session state changed. Since the response has been received, the app will update it’s session state value and keep polling the OP iframe again.
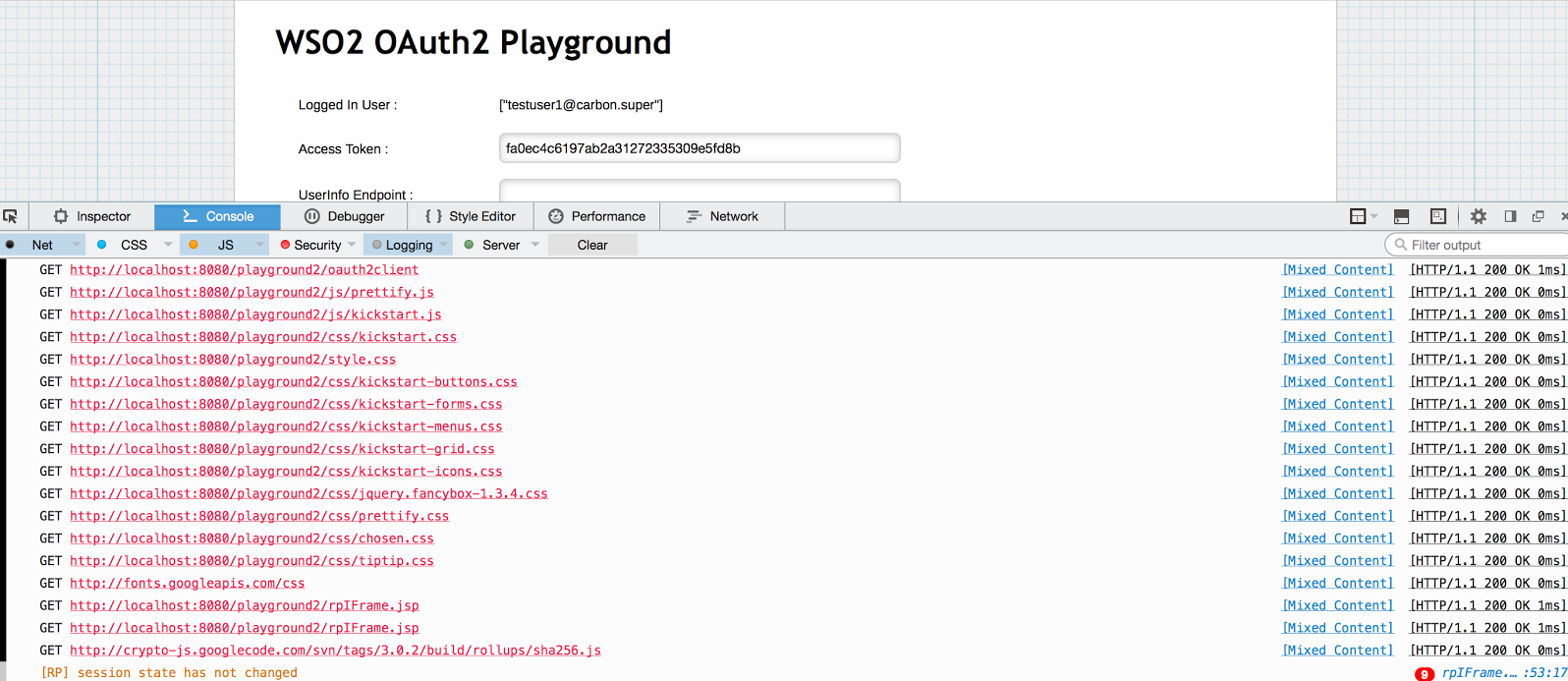
-
Go back to the browser window of the playground3 app, and click Logout. Click Approve when prompted for consent.
-
Go back to the browser window of the playground2 app. You will see that the home page has loaded. If you check the console logs, you will note that the the playground2 app’s RP iframe has initiated a passive authentication request and has received an error since the end user session has ended. This means the app has successfully handled this as a single logout scenario.
Redirect to a logout URL after RP-initiated logout
You can specify a logout URL so that the application redirects to a particular page after the RP sends the OpenID Connect logout request. For more information on how to configure the redirect logout, see OpenID Connect Logout URL Redirection.