Configure SMS OTP for two-factor authentication¶
This page guides you through configuring two-factor authentication for a web application using SMS OTP as the second factor.
Set up SMS OTP provider¶
-
Download the certificate of the SMS provider.
Example
If you wish to have NEXMO as your SMS provider:
- Go to the SMS provider's website, https://www.nexmo.com.
- Click on the security padlock next to the URL, and export the certificate.
-
Navigate to the
<IS_HOME>/repository/resources/securitydirectory and import the downloaded certificate into the WSO2 IS client keystore.keytool -importcert -file <CERTIFICATE_FILE_PATH> -keystore client-truststore.jks -alias "Nexmo" -
You are prompted to enter the keystore password. The default
client-truststore.jkspassword iswso2carbon.
Enable SMS OTP for an SP¶
Prerequisites¶
- You need to set up the sample application.
- You need to configure local claims for the application:
- On the management console, go to the application you created and click Edit
- Expand Claim configuration.
- Select
http://wso2.org/claims/mobileas the Subject Claim URI. - Click Update to save the configurations.
- You need to update the User Profile of the users with a mobile number to which the user will receive the OTP.
- You need to register an Identity Provider named
smsOTP. - Set up the SMS OTP provider (example: Vonage, Clickatell, Plivo, Bulksms, Twillio).
Configure the SMS OTP authenticator¶
To configure the SMS OTP authenticator:
- On the management console, go to Identity Providers > List.
- Click on Edit corresponding to the
smsOTPidentity provider. - Expand Federated Authenticators > SMS OTP Configuration.
- Enable the SMS OTP authenticator by selecting the Enable option provided.
-
Enter SMS URL, HTTP Method, HTTP Headers and HTTP Payload according to the SMS service provider you are using.
Info
-
The above parameters depend on the service provider that you use.
-
If the text message and the phone number are passed as parameters in any field, include them as $ctx.num and $ctx.msg respectively.
-
Optionally, enter the HTTP Response Code the SMS service provider sends when the API is successfully called. If this value is unknown, leave it blank, and the connector checks if the response is
200,201, or202.
Configure Vonage
If you have configured Vonage as your SMS provider, add the following details when configuring the SMS provider on IS.
SMS URL https://rest.nexmo.com/sms/json?api_key=<API_KEY>&api_secret=<API_SECRET>&from=NEXMO&to=$ctx.num&text=$ctx.msgHTTP Method POSTHTTP Response Code 200Configure Clickatell
If you have configured Clickatell as your SMS provider, add the following details when configuring the SMS provider on IS.
SMS URL https://api.clickatell.com/rest/messageHTTP Method POSTHTTP Header X-Version: 1,Authorization: bearer ,Accept: application/json,Content-Type: application/jsonHTTP Payload {"text":" $ctx.msg ","to":[" $ctx.num "]}HTTP Response Code 202Configure Plivo
If you have configured Plivo as your SMS provider, add the following details when configuring the SMS provider on IS.
SMS URL https://api.plivo.com/v1/Account/{auth_id}/Message/HTTP Method POSTHTTP Header Authorization: Basic ********,Content-Type: application/jsonHTTP Payload {"src":"+94*********","dst":"ctx.num","text":"ctx.msg"}HTTP Response Code 202Configure Bulksms
If you have configured Bulksms as your SMS provider, add the following details when configuring the SMS provider on IS.
SMS URL https://bulksms.vsms.net/eapi/submission/send_sms/2/2.0?username=<username>&password=<password>&message=$ctx.msg&msisdn=$ctx.numHTTP Method POSTHTTP Header Content-Type: application/x-www-form-urlencodedHTTP Response Code 200Configure Twillio
If you have configured Twillio as your SMS provider, add the following details when configuring the SMS provider on IS.
SMS URL https://api.twilio.com/2010-04-01/Accounts/<AccountSID>/SMS/Messages.jsonHTTP Method POSTHTTP Header Authorization: Basic base64{AccountSID:AuthToken}HTTP Payload Body=$ctx.msg&To=$ctx.num&From=urlencode{FROM_NUM} -
-
Click Update to save the configurations.
Configure SMS OTP as the second factor¶
To configure SMS OTP as the second authentication factor:
-
On the management console, go to Main > Identity > Service Providers > List.
-
Click Edit on the
saml2-web-app-pickup-dispatch.comservice provider. -
Expand the Local and Outbound Authentication Configuration section and click Advanced Configuration.
-
You will be redirected to Advanced Configuration.
-
Click + Add Authentication Step twice to add two authentication steps.
-
Select the following authentication methods from the relevant dropdowns and click + Add Authenticator.
Authentication step Local Authenticator Federated Authenticator First step Username & PasswordN/A Second step N/A smsOTP -
Click Update to save the configurations.
Try it out¶
-
Access the following sample Pickup Dispatch application URL:
http://localhost.com:8080/saml2-web-app-pickup-dispatch.com -
Click Login and enter admin's credentials.
-
You will now be prompted to enter an SMS OTP code. The SMS OTP will be sent to the mobile number configured on the user's profile.
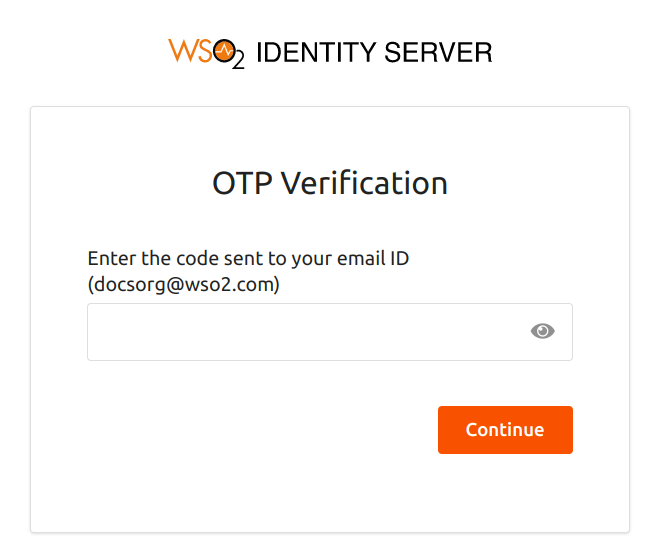
-
Enter the SMS OTP received and click Continue.
You will now be logged into the application successfully.
Additional configurations¶
Allow users to disable SMS OTP¶
To allow users to disable SMS OTP:
- On the management console, go to **Claims > List**and select
http://wso2.org/claims. - Click on Edit corresponding to the Disable SMSOTP claim
- Select the Supported By Default checkbox to enable the Disable SMSOTP claim.
- Click Update to save your changes.
Verify if Disable SMSOTP is enabled for users
To verify whether the option is available for the users
-
Go to the user profile of any user and check whether the Disable SMSOTP option is available.
-
To disable SMS OTP in the user profile, enter True in the Disable SMSOTP field and click Update.
Configure backup codes¶
Optionally, you can configure backup codes to be used when SMS OTP is disabled.
To configure backup SMS OTP codes:
-
On the management console, go to Main > Identity > Claims > Add.
-
Click Add Local Claim, and enter the following details:
Field name Value Claim URI http://wso2.org/claims/otpbackupcodesDisplay Name backupotpDescription Backup codes for SMS OTP Mapped Attribute postalcodeSupported by Default Selected 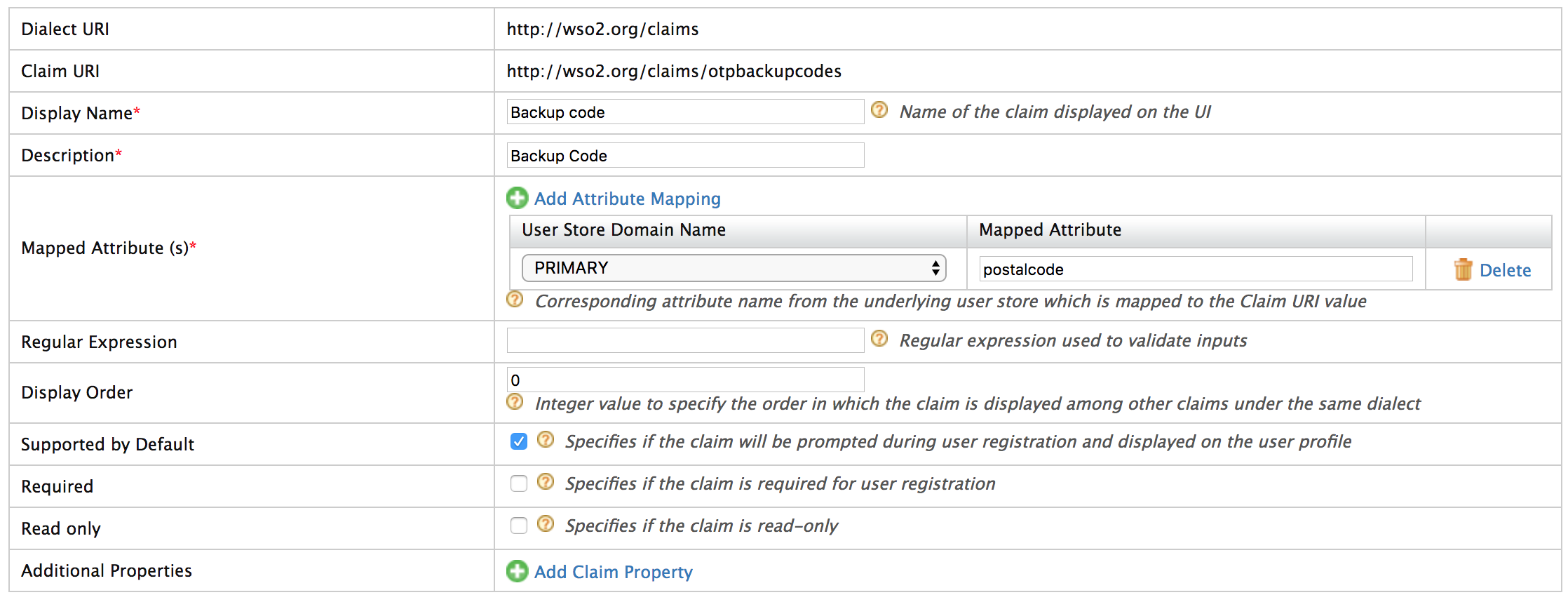
-
Click Add to add the new local claim.
Add backup codes for users
A backup code can have any number of digits, and you can define many backup codes as comma-separated values. For Example, 10300,21390
-
On the Management Console, go to Identity > Users and Roles > List > Users.
-
Select the user you want to add backup codes for and click User Profile.
-
Add the backup codes so that the user can disable SMS OTP by selecting Disable SMS OTP if required.