Forced Password Reset¶
The WSO2 Identity Server allows authorized administrative persons to trigger a password reset for a given user account. This may be required for the following situations:
-
The user forgets the credentials and makes a request to the administrator for a password reset.
-
Credentials may get exposed to outsiders. Hence, the user needs to reset the password and lock the account, till then so that no one else can log in.
In such situations, the user has the option of contacting the admin and based on the validity of the request, the admin can force a password reset for the user account. Once it is initiated, at the point of login, the Username & Password authenticator processes the login request and prompts the corresponding dialogs or error messages based on account status.
Prerequisites¶
Create a user
-
Log in to the WSO2 Identity Server Management Console (
https://<IS_HOST>:<PORT>/carbon) using administrator credentials (admin:admin). -
Navigate to Main > Identity > Users and Roles > Add.
-
Click Add New User and create a new user by providing a username and a password.
-
Click Finish.
-
In the next view, click User Profile of the newly created user.
-
Update the user profile with a valid email address and other information.
Configure the email adapter to send emails
Note
This step is not required for Offline Password Reset.
-
Navigate to the
<IS_HOME>/repository/conf/deployment.tomlfile and uncomment the[output_adapter.email]configuration block.[output_adapter.email] from_address= "[email protected]" username= "[email protected]" password= "xxxx" hostname= "smtp.office365.com" port= 587Info
- If you use a Gmail account as the email OTP sender, you must create an App Password. After you get an App Password from Google, update the
password. - If your password contains special characters (example:
<,>,&), you will run into errors when running the server. To avoid errors, update thepasswordparameter as follows:password= "<![CDATA[xxxx]]>"
- If you use a Gmail account as the email OTP sender, you must create an App Password. After you get an App Password from Google, update the
-
Update the sample values with your email adapter configurations.
Info
Refer configure email sending module for the complete list of email adapter configurations.
-
Save the configurations and restart the server.
Tip
The email template used to send this email notification is the AdminForcedPasswordReset template for password recovery via recovery email, and the AdminForcedPasswordResetWithOTP template for password recovery via OTP (one-time password).
You can edit and customize the email template. For more information on how to do this, see see Customize Automated Emails.
Configure forced password reset feature¶
-
Log in to the WSO2 Identity Server Management Console (
https://<IS_HOST>:<PORT>/carbon) using administrator credentials (admin:admin). -
Navigate to Main > Identity > Identity Providers and click on Resident.
-
Expand the Account Management tab.
-
Expand the Password Reset tab. You will see the following options for forced password reset:
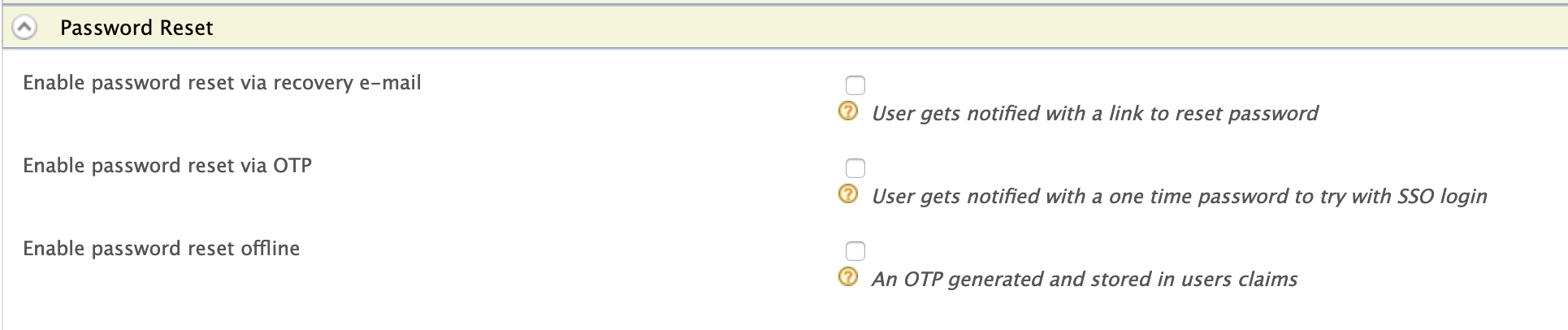
Password Reset via Recovery Email¶
Enabling this option will send an email to the user with the corresponding information.
Tip
The email template for this option is AdminForcedPasswordReset.
Follow the steps below to see how this works.
-
Select Enable password reset via recovery e-mail from the three options listed, and click Update.
Tip
If you wish to enable this feature for all tenants by default, add the following configuration to the
<IS_HOME>/repository/conf/deployment.tomlfile and restart the server.[identity_mgt.password_reset_by_admin] enable_emailed_link_based_reset= true -
Once the option is selected, admin users can force a password reset flow by updating the
http://wso2.org/claims/identity/adminForcedPasswordResetclaim to true for the relevant users. To do this, follow the steps explained later in this page under Invoke Admin Force Password Reset. -
Attempt to log in to the My Account (
https://<HOST>:<PORT>/myaccount) application as the user you created above. The login attempt will fail and a password reset will be prompted in the form of an error message saying "Login failed! Please recheck the username and password and try again". -
Log in to the email account you provided in user profile of the created user. You will see a new email with a password reset request.
-
Follow the link provided in the email to reset the password. You can now log in to the My Account (
https://<HOST>:<PORT>/myaccount) application successfully using the new password.
Password Reset via OTP¶
Enabling this option will send an email to the user with a one time password that the user can use to log in once to the account after which, the user will be prompted to set a new password.
Tip
The email template for this option is AdminForcedPasswordResetWithOTP.
-
Select Enable password reset via OTP from the three options listed, and click Update.
-
Once the option is selected, admin users can force a password reset flow by updating the
http://wso2.org/claims/identity/adminForcedPasswordResetclaim to true for the relevant users. To do this, follow the steps explained later in this page under Invoke Admin Force Password Reset. -
Attempt to log in to the My Account (
https://<HOST>:<PORT>/myaccount) application as the user you created above. The login attempt will fail and a password reset will be prompted in the form of an error message saying "Login failed! Please recheck the username and password and try again". -
Log in to the email account you provided in user profile of the created user. You will see a new email with an OTP (one time password) provided to log in to the account.
-
Use the OTP provided in the email to log in as the user you created above. You will be redirected to the password reset UI where you are prompted to set a new password. Enter the relevant details to set a new password.
-
You can now log in to the My Account (
https://<HOST>:<PORT>/myaccount) application successfully as the user you created using the new password.
Offline Password Reset¶
-
Select Enable Password Reset Offline from the three options listed, and click Update.
-
Click on List under Claims found in the Main > Identity tab and select http://wso2.org/claims.
-
Select the One Time Password claim, click Edit and select the Supported by Default checkbox. Click Update to save changes.
-
Navigate to Users and Roles > List > Users and check the user profile of the user you created above. You will see that the value for the One Time Password field is empty.
-
Next, admin users can force a password reset flow by updating the
http://wso2.org/claims/identity/adminForcedPasswordResetclaim to true for the relevant users. To do this, follow the steps explained later in this page under Invoke Admin Force Password Reset. -
Attempt to log in to the My Account (
https://<HOST>:<PORT>/myaccount) application as the user you created above. The log in attempt will fail. -
Log in again to the Management Console (
https://<IS_HOST>:<PORT>/carbon) as the admin user and check user profile of the user you created above. You will see that there is now a code value in the One Time Password field. -
Copy the code and use it as the password of the user you created above to log in to the the My Account (
https://<HOST>:<PORT>/myaccount) application. -
You will be redirected to the password reset UI where you are prompted to set a new password. Enter the relevant details to set a new password.
-
You can now log in to the My Account (
https://<HOST>:<PORT>/myaccount) application successfully as the user you created above using the new password.
Invoke Admin Force Password Reset¶
Use the following SCIM 2.0 REST API request to trigger a password reset.
Set the forcePasswordReset attribute under the urn:ietf:params:scim:schemas:extension:enterprise:2.0:User schema as
true in the SCIM 2.0 user create request.
PATCH https://<host>:<port>/scim2/Users/<users-scim-id>
{"schemas":
["urn:ietf:params:scim:api:messages:2.0:PatchOp","urn:ietf:params:scim:schemas:extension:enterprise:2.0:User"],
"Operations": [
{"op": "add",
"value": {"urn:ietf:params:scim:schemas:extension:enterprise:2.0:User": {"forcePasswordReset": true}
}}]
}A sample curl command is given below:
curl -v -k --user admin:admin -X PATCH -d '{"schemas":["urn:ietf:params:scim:api:messages:2.0:PatchOp","urn:ietf:params:scim:schemas:extension:enterprise:2.0:User"], "Operations": [ {"op": "add","value": {"urn:ietf:params:scim:schemas:extension:enterprise:2.0:User": {"forcePasswordReset": true}}}]}' --header "Content-Type:application/json" https://localhost:9443/scim2/Users/c02857fd-2a51-427f-bf25-a9f76b85659dChange password¶
If you are a user with admin privileges, you can change your own password or reset another user's password using the management console as explained below.
To change a user's password:
- Log in to the management console of your product.
- On the Main tab, click List under Users and Roles.
- To change your own password, click Change My Password, enter your current password and new password, and click Change.
- If you are an admin user and need to change another user's password
(such as if they have forgotten their current password and need you
to reset it), do the following:
- Click Users.
- Find the user's account on the Users screen and click Change Password in the Actions column.
- Enter a new temporary password and click Change.
- Inform the user of their new temporary password and instruct them to log in and change it as soon as possible.
Related topics
See Configuring Claims for more information on how to store the claim values in the user store.