Kerberos Grant¶
Kerberos is a security protocol that has built-in support to various operating systems and open source distributions (e.g., Ubuntu, Windows, RedHat, Open Solaris, etc). Additionally, a majority of browsers support some Kerberos functions as well. As WSO2 Identity Server (WSO2 IS) uses the OAuth 2.0 protocol, the Kerberos-OAuth2 grant type allows organizations to exchange a Kerberos ticket for an OAuth 2.0 token. This allows organizations to re-use their existing Kerberos infrastructure and adopt OAuth 2.0.
Kerberos-OAuth2 grant flow¶
The following section describes the flow involved in exchanging a Kerberos ticket for an OAuth2 token.
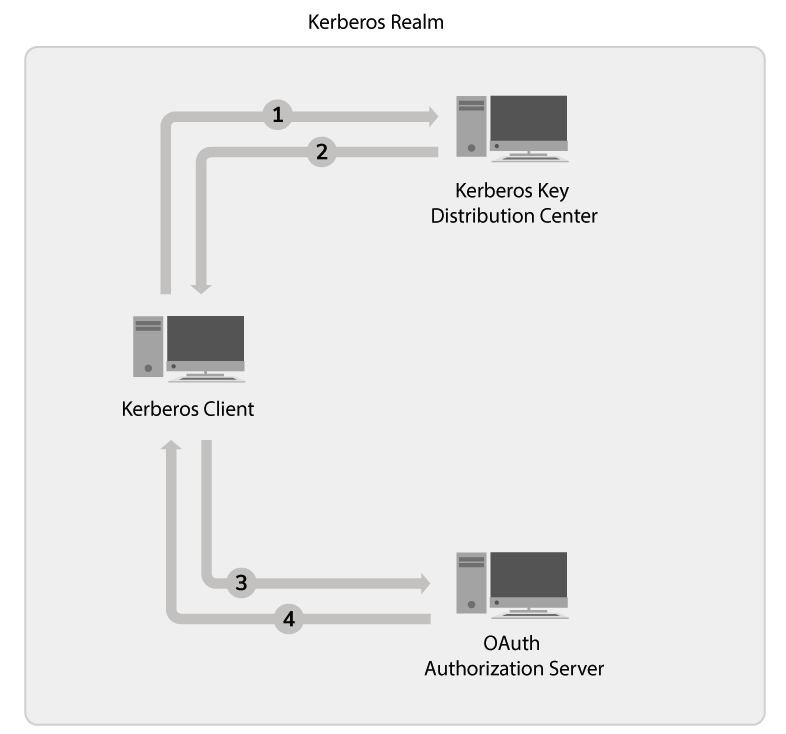
- The Kerberos client requests the Kerberos Service Ticket from the
Kerberos Key Distribution Center (KDC) to invoke the service.
The Kerberos Key Distribution Center can be any Kerberos Server. - The Kerberos Key Distribution Center sends a response with the
Kerberos Service Ticket.
If the client and the requested service is valid, the Key Distribution Center (KDC) sends a Kerberos ticket encrypted with the service owners private key. The API handles the exchanging of the Ticket Granting Ticket (TGT), Service Granting Ticket (SGT), and all other low level Kerberos details. -
The Kerberos client requests the OAuth2 token.
The message format of the OAuth2 token request should be as follows:
You can use one of the following two cURL commands to request for the OAuth2 token.
Request 1
curl -v -X POST -H "Authorization: Basic <Base64Encoded(CLIENT_ID:CLIENT_SECRET)>" -k -d "grant_type=kerberos&kerberos_realm=<KERBEROS_REALM>&kerberos_token=<KERBEROS_TOKEN>" -H "Content-Type:application/x-www-form-urlencoded" <TOKEN_ENDPOINT>
Request 2
curl -u <CLIENT_ID>:<CLIENT_SECRET> -k -d "grant_type=kerberos&kerberos_realm=<KERBEROS_REALM>&kerberos_token=<KERBEROS_TOKEN>" -H "Content-Type:application/x-www-form-urlencoded" <TOKEN_ENDPOINT>
Response
POST /oauth2/token HTTP/1.1 Host: idp.example.com:9443 Content-Type: application/x-www-form-urlencoded Authorization: Basic MW91TDJmTzZTeGxmRDJMRHcxMjVjVG8wdlFrYTp1VUV0bTg5dFk2UVp1WlVtcVpmTDkyQkRGZUFh grant_type=kerberos&kerberos_realm=example.com&kerberos_token=YII1… -
The Kerberos client receives the OAuth2 token.
-
The Kerberos Grant validates the received token with the provided identity provider (IdP) credentials and if it is a valid token, it issues an OAuth2 token to the client.
Example:
{ "access_token":"636ce45f-c7f6-3a95-907f-d1f8aca28403", "refresh_token":"831271d9-16ba-3bad-af18-b9f6592a8677", "scope":"my_scope", "token_type":"Bearer", "expires_in":521 }