Create a XACML Policy using a Policy Template¶
This section guides you through using and editing the XACML policy templates available in WSO2 Identity Server to write your own policy.
- Start WSO2 Identity Server and log in to the management console.
-
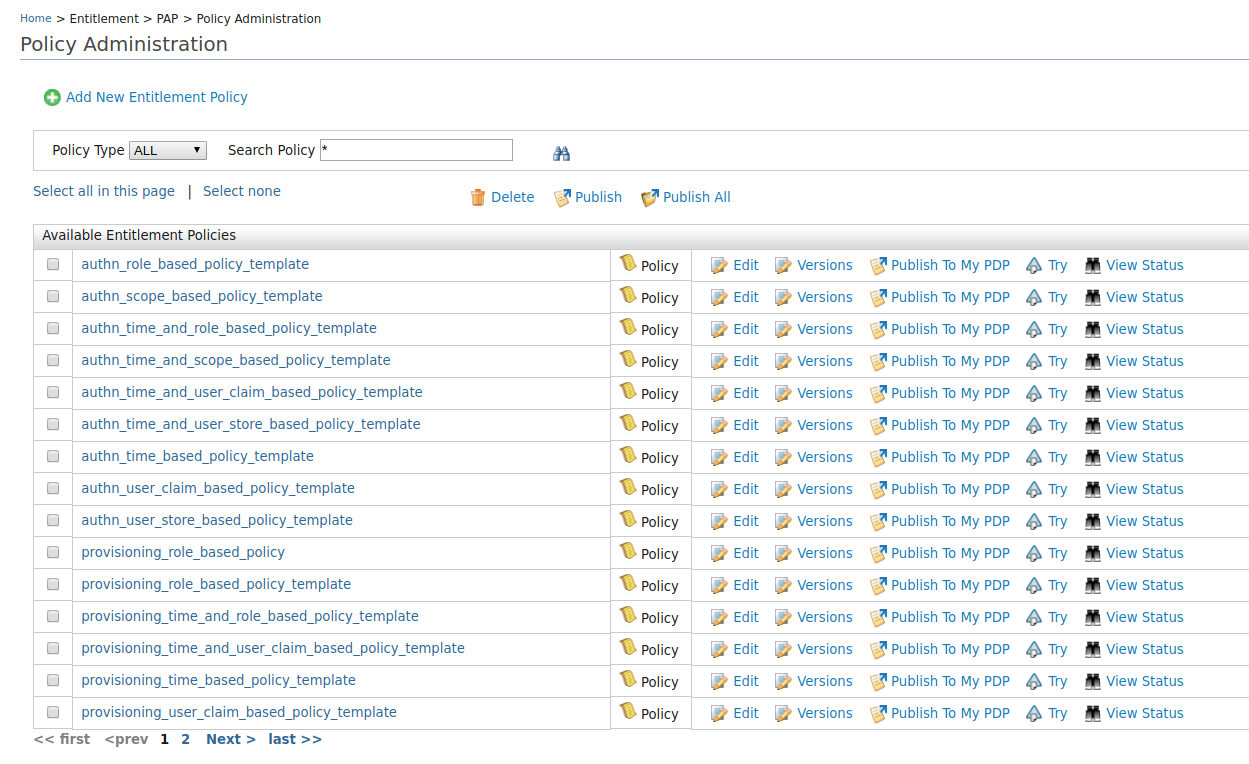
Click on Policy Administration under the Entitlement>PAP section on the Main tab.
-
You will see the following list of available policy templates.
Template Name Description authn_role_based_policy_template This policy template provides the abilitity to authorize users to a given service provider (defined by the SP_NAMEplaceholder) in the authentication flow based on the roles of the user (defined byROLE_1andROLE_2placeholders). Users who have at least one of the given roles are permitted to log in and any others are denied.authn_scope_based_policy_template This template policy provides the ability to authorize users to a given service provider (defined by SP_NAMEplaceholder) in the authentication flow based on the OAuth scope(s) (SCOPE1, SCOPE2). Users who are authenticated with the given scopes are allowed and any other users are denied.authn_time_and_role_based_policy_template This policy template provides the ability to authorize users to a given service provider (defined by SP_NAMEplaceholder) in the authentication flow based on the roles of the user (defined byROLE_1andROLE_2) and the time of the day (e.g., between 09:00:00 to 17:00:00). Users who have at least one of the given roles are permitted to login within the given time. Any other requests will be denied.authn_time_and_scope_based_policy_template This template policy provides the ability to authorize users to a given service provider (defined by SP_NAMEplaceholder) in the authentication flow based on the oauth scope(s) (SCOPE1orSCOPE2) and the time of the day (e.g., between 09:00:00 to 17:00:00). Users who are logging in between the given time and who grant the given scopes are permitted to login and any other user will be denied.authn_time_and_user_claim_based_policy_template This template policy provides the ability to authorize users to a given service provider (defined by SP_NAMEplaceholder) in the authentication flow based on the claim values of the user (CLAIM_URI_1=CLAIM_VALUE_1andCLAIM_URI_2=CLAIM_VALUE_2) and the time of the day (e.g., between 09:00:00 to 17:00:00). Users with the given claim values and who are logged in within the given time range are permitted and any other users will be denied.authn_time_based_policy_template This template policy provides the ability to authorize users to a given service provider(defined by SP_NAMEplaceholder) in the authentication flow based on the login time. Any authentication attempt outside the specified time range (09:00:00 to 17:00:00) will be denied.provisioning_role_based_policy_template This template policy provides the ability to authorize provisioning requests initiated from a given service provider (defined by SP_NAMEplaceholder) to a given identity provider (defined byIDP_NAMEplaceholder) in the outbound provisioning flow based on the roles of the user (ROLE_1, ROLE_2). Provisioning attempts to the users with given role(s) are permitted and all others will be denied.provisioning_time_and_role_based_policy_template This template policy provides the ability to authorize provisioning requests initiated from a given service provider (defined by SP_NAMEplaceholder) to a given identity provider (defined byIDP_NAMEplaceholder) in the outbound provisioning flow based on the roles of the user (ROLE_1, ROLE_2) and time of the day (e.g., between 09:00:00 to 17:00:00). Provisioning attempts to the users with given role(s) between the given time are permitted and all others will be denied.provisioning_time_and_user_claim_based_policy_template This template policy provides the ability to authorize provisioning requests initiated from a given service provider (defined by SP_NAMEplaceholder) to a given identity provider(defined byIDP_NAMEplaceholder) in the outbound provisioning flow based on the claim values of the user (CLAIM_URI_1=CLAIM_VALUE_1andCLAIM_URI_2=CLAIM_VALUE_2) and time of the day (e.g., between 09:00:00 to 17:00:00). Provisioning attempts to the users with the given claim values between the given time are permitted and all others will be denied.provisioning_time_based_policy_template This template policy provides the ability to authorize provisioning requests initiated from a given service provider (defined by SP_NAMEplaceholder) to a given identity provider(defined byIDP_NAMEplaceholder) in the outbound provisioning flow based on the requested time. Any provisioning attempt outside the specified time range(09:00:00 to 17:00:00) will be denied.provisioning_user_claim_based_policy_template This template policy provides ability to authorize provisioning requests initiated from a given service provider (defined by SP_NAMEplaceholder) to a given identity provider (defined byIDP_NAMEplaceholder) in the outbound provisioning flow based on the claim values of the user (CLAIM_URI_1=CLAIM_VALUE_1andCLAIM_URI_2=CLAIM_VALUE_2). Users with the given claim values are permitted and any other users will be denied. -
Click the corresponding Edit button of the policy template that you want to use.
- Edit the Policy ID with a name relevant to your policy.
- Edit the placeholders with the relevant values and click Save
Policy.
You can see the policy you just created on the policy list (the original template policy will remain unchanged for later use). - Click on the Publish to My PDP link corresponding to the new
policy.

-
On the UI that appears, leave the default selected values as they are and click Publish.
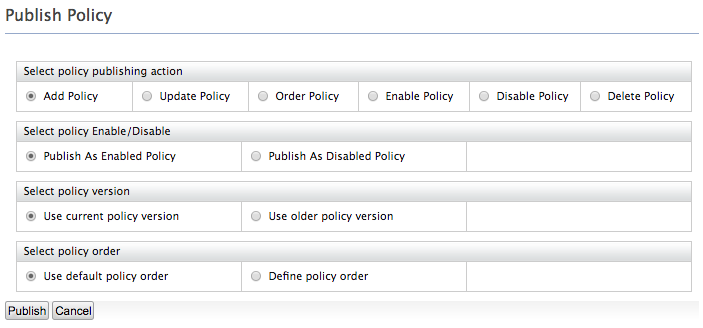
Note
For more information on Publishing a XACML policy, click here.
-
Click on Policy View under the Entitlement>PDP section on the Main tab of the management console.
- To ensure that the policy has been published successfully, check if
the policy is listed.