Registering a service provider¶
You can connect your application with Identity Server and control how users log into your app. This guide provides instructions on how to add and configure a service provider to Identity Server through the management console.
For more information on how the service provider fits into the WSO2 IS architecture, see Architecture.
Register a service provider¶
To add a new service provider on WSO2 Identity Server:
-
On WSO2 IS Management Console, go to Main > Identity > Service Providers > Add.
-
Select Manual Configuration, and enter the following details:
Field Description Service Provider Name A name for your service provider. This field is required to register an SP. Description A short description of the service provider Management Application Select this checkbox if the application is used to access the management APIs. 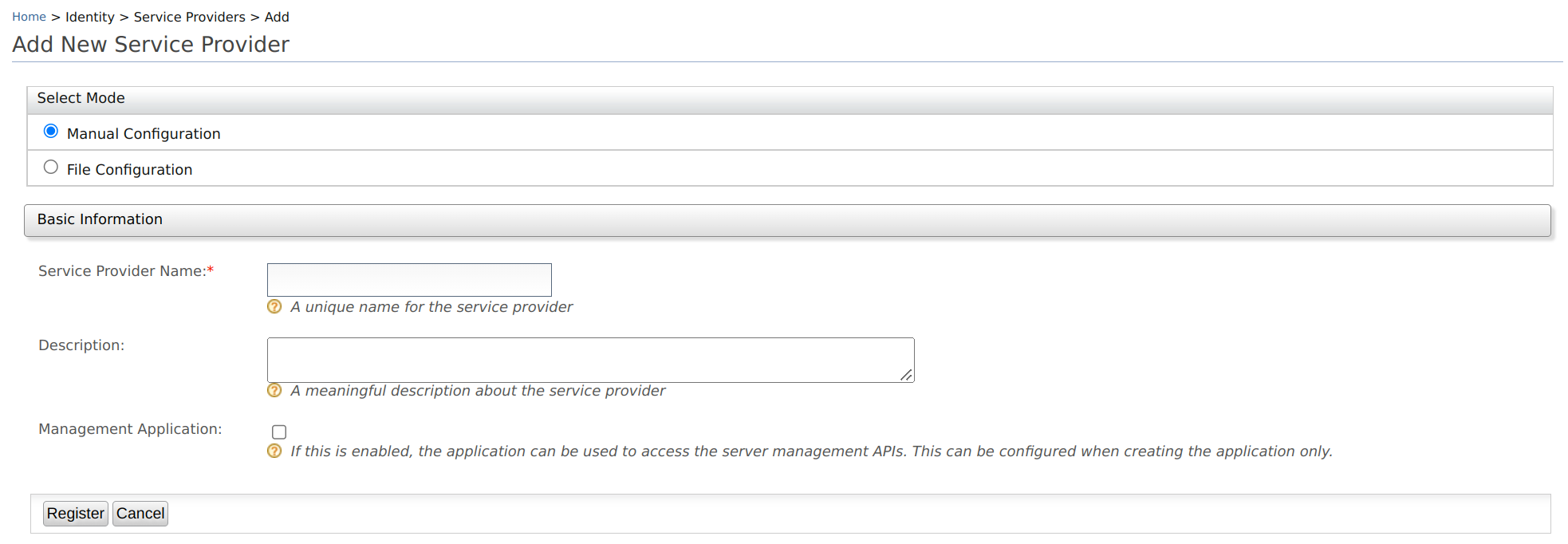
Modify validation for service provider name
The default javascript regex used to validate the service provider name is
^[a-zA-Z0-9\\s.+_-]*$. You can modify this regex by adding the following configuration to thedeployment.tomlfile.``` java [service_provider] sp_name_java_script_regex = '<required_javascript_regex>' ``` -
Click Register to complete the registration.
Info
You can also import a service provider using the File configuration option.
Import a service provider¶
To import a service provider:
- On WSO2 IS Management Console, go to Main > Identity > Service Providers > Add.
- Select File Configuration, and upload the .XML file.
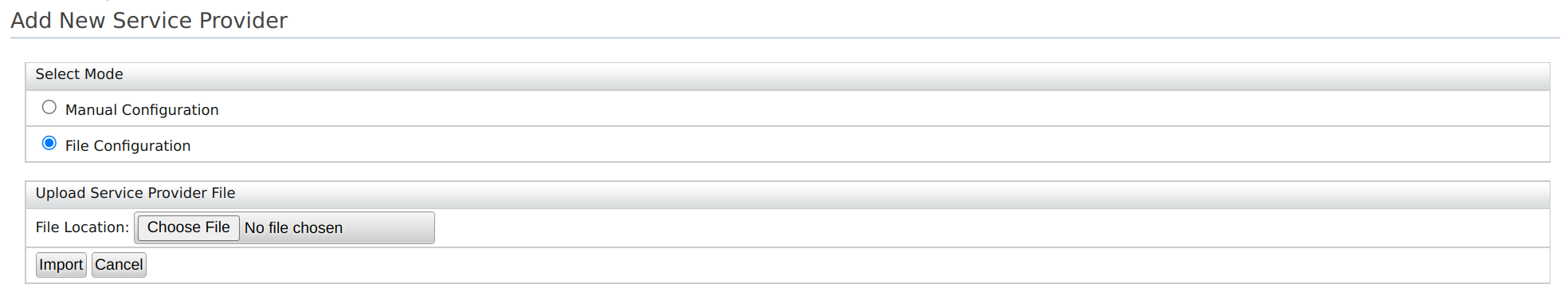
- Click Import to add the service provider using the XML file.
Service provider configurations¶
You can find the basic configurations of a service provider under Service Providers section of the selected application.
| Field | Description |
|---|---|
| Select SP Certificate Type | A certificate is used to validate requests from the SP. You can either Use SP JWKS endpoint or Upload SP certificate. |
| JWKS URI | If you have selected Use SP JWKS endpoint in the above field, this field will appear. You need to add the JWKS endpoint URI in this field. |
| Application Certificate | If you have selected Upload SP certificate in the above field, paste the public certificate into the given text area or upload the certificate file in PEM format. Learn more about public certificates for service providers. |
| SaaS Application | Enable this to allow users to allow tenants to log in to the application. Disabling this allows only users of the current tenant (the tenant you use to configure the SP) to login into the application. |
| Discoverable Application | Enable this to make the application discoverable to users. |
| Access URL | Access URL for the Service Provider. |
| Logo URL | Add a link to the logo for your application here. |
| Logout Return URL or regex | The URL that the users will be redirected to during a direct IdP logout |
| Management Application | The selection you made for Management Application during the application creation will be shown here. This cannot be updated. WSO2 Identity Server exposes all the management capabilities as REST APIs. These APIs are protected by OAuth2 access tokens and other API authentication mechanisms. The applications that are marked as management applications can only be used to access these management APIs in the OAuth2 flow. This can only be configured when creating the application. |
Public certificates for service providers¶
A certificate is used to validate the signatures of the signed requests received from the application (service provider) to WSO2 IS.
Usage of the certificate
The certificate is used in the following scenarios:
- To validate the signature of the SAML2 authentication requests and the SAML2 logout requests sent by the service provider during SAML SSO flows.
-
When passing OIDC authentication request parameters the certificate is used to:
- Encrypt the
id_tokensent to the service provider in the OIDC Authentication Response. - Validate the signed
RequestObjectsent in the OAuth2/OIDC Authorization Request.
- Encrypt the
Obtain the PEM encoded certificate
WSO2 IS expects the certificate to be in PEM format.
To obtain the PEM content of a certificate in a JKS file:
-
Export the certificate from the key store using the following command.
keytool -export -keystore <keystore-path> -alias <alias-of-the-certificate> -file <path-of-the-expected-certificate-file>Example:
keytool -export -keystore wso2carbon.jks -alias wso2carbon -file wso2carbon.crt -
The exported certificate will be in binary format. Convert this binary encoded certificate to a PEM-coded certificate using the following command.
Example:openssl x509 -inform der -in <path-of-binary-certificate> -out <path-of-expected-pem-content>openssl x509 -inform der -in wso2carbon.crt -out wso2carbon.pem
What happens if you don't add the certificate
If the Application Certificate field is left blank, as WSO2 IS is backward compatible and follows the previous implementation to locate the certificates in the key store.
-
For a SAML SSO flow, the certificate alias mentioned in SAML inbound authentication configuration will be used when the certificate is not updated via the management console.
-
For an OIDC request object signature validation, the certificate will be retrieved from the default key store, an alias to the consumer key of the auth application.
Related Topics
See the following topics to configure different applications as service providers in Identity Server.