Password validation¶
Customize password validation rules to enhance the security of user accounts in WSO2 Identity Server.
Configuration instructions¶
To configure password validation rules, follow the steps below:
- On the WSO2 Identity Server Console, go to Login & Registration > Login Security > Password Validation.
- Adjust the settings according to your security requirements.
- Click Update to save the changes.
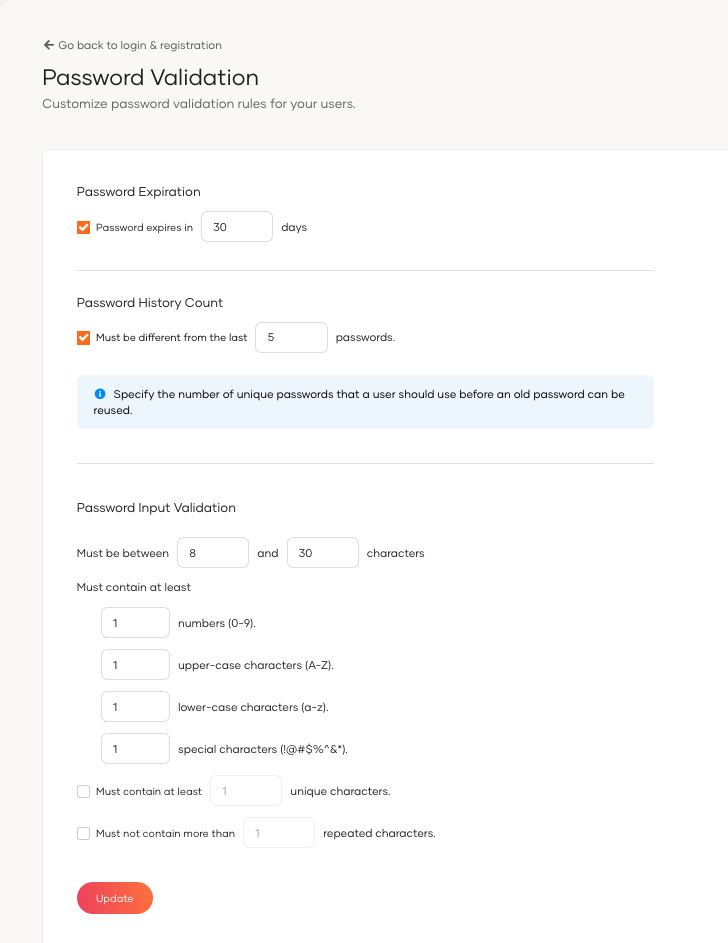
Parameters¶
| Parameter | Description |
|---|---|
Password Expiration |
Defines the number of days after which a password must be changed. |
Password History Count |
Specifies the number of unique new passwords a user must use before an old password can be reused. |
Password Input Validation |
Sets requirements for password complexity, including length and character types. |