API authorization for organizations¶
WSO2 Identity Server allows organizations to authorize user access to an application's API resources based on the API permissions, roles, and groups assigned to the users. See API authorization for more information.
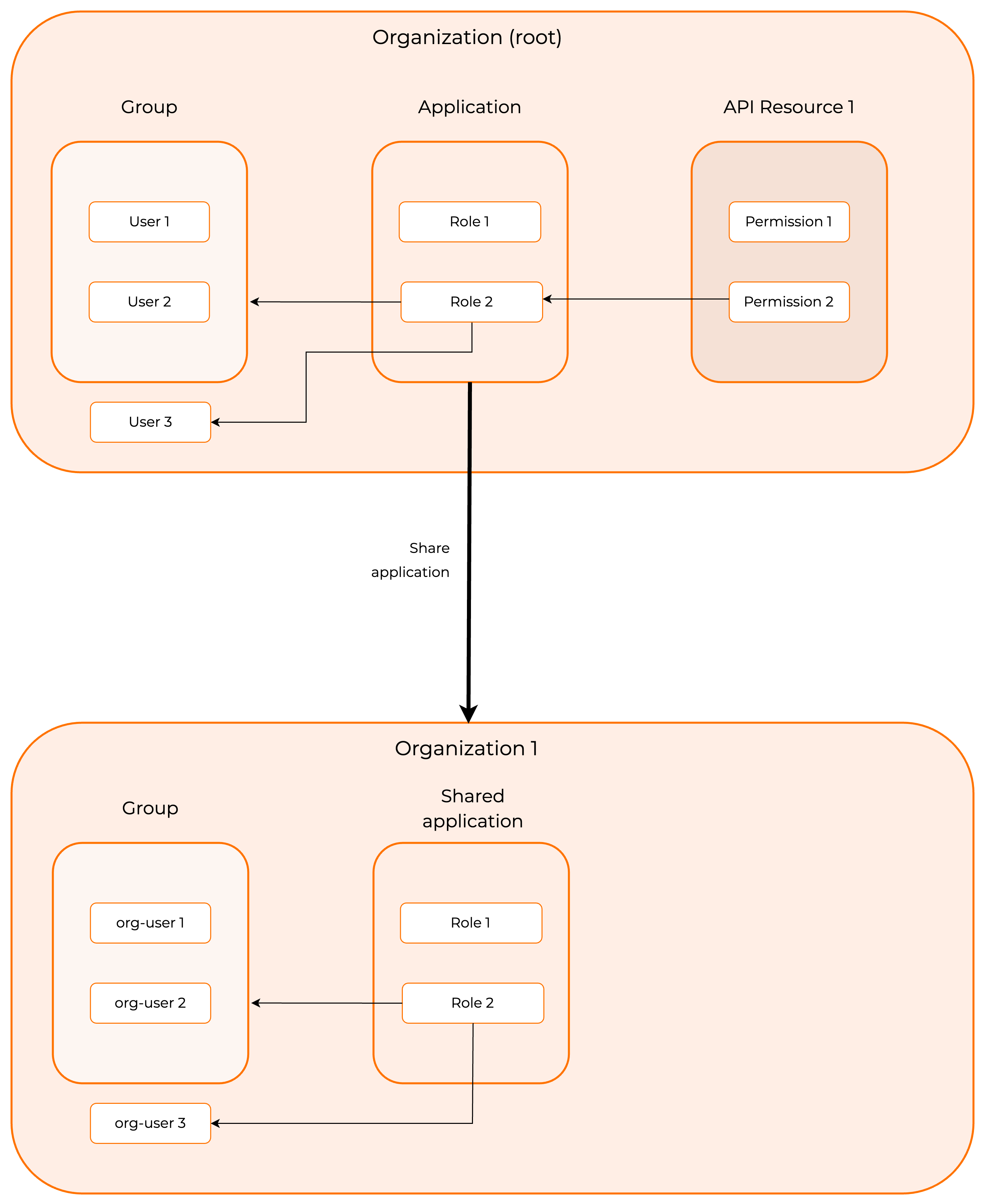
API resources are created and authorized for applications on the organization (root). If the application consuming the API resources is shared with the organization, all application-specific configurations of API resources are inherited by the organization.
Prerequisites¶
You need to configure your API resources on the organization (root)
- Register an API resource
- Authorize the API resource to an app
- Create roles and associate to application
Organizations have the roles associated with their shared applications. Shared roles of organizations inherit the permission assignment to the role from the organization (root).
Roles of an organization
The shared roles in organizations will inherit the permission to role assignments from the organization (root). Users and group assignment to the roles should be done separately for the organization, as the organization does not inherit the users or groups from the organization (root).
Organization administrators cannot create new roles, modify name or permissions of the shared roles, or delete the shared roles, but you can assign these roles to your organization users and groups.
Assign organization users to roles¶
To assign roles to users of the organization:
- On the WSO2 Identity Server Console, switch to the organization.
- Go to User Management > Roles.
- Select the role you wish to assign to a user and click Edit.
- Go to Users and click Assign Users.
- Select the user who should be assigned to the selected role.
- Click Update to complete the role to user assignment.
Assign organization groups to roles¶
Organizations maintain the following types of groups, and you can assign your application roles to any of these groups.
- Groups - A collection of organization users.
- Federated IdP Groups - These groups are federated from connections on the organization. For example, groups federated from the Google connection.
Assign user groups to roles¶
To assign roles to user groups of the organization:
- On the WSO2 Identity Server Console, switch to the organization.
- Go to User Management > Roles.
- Select the role you wish to assign to a group and click Edit.
- Go to Groups and click Assign Groups.
- Select the group which should be assigned to the selected role.
- Click Update to complete the role to group assignment.
Assign federated IdP groups to roles¶
To assign roles to federated IdP Groups:
Before you begin
To get started,
- You should register, configure, and create groups for a connection in your organization.
- You should add this connection to the sign-in flow of the application to which the roles are associated.
- On the WSO2 Identity Server Console, switch to the organization.
- Go to User Management > Roles.
- Select the role you wish to assign to a group and click Edit.
- Select the federated IdP from which you select groups.
- Select the group which should be assigned to the selected role.
- Click Update to complete the role to group assignment.
Try it out¶
Follow the steps given below to try out the RBAC flow:
Note
Note that we are using WSO2 Identity Server's B2B Guardio insurance application for this scenario.
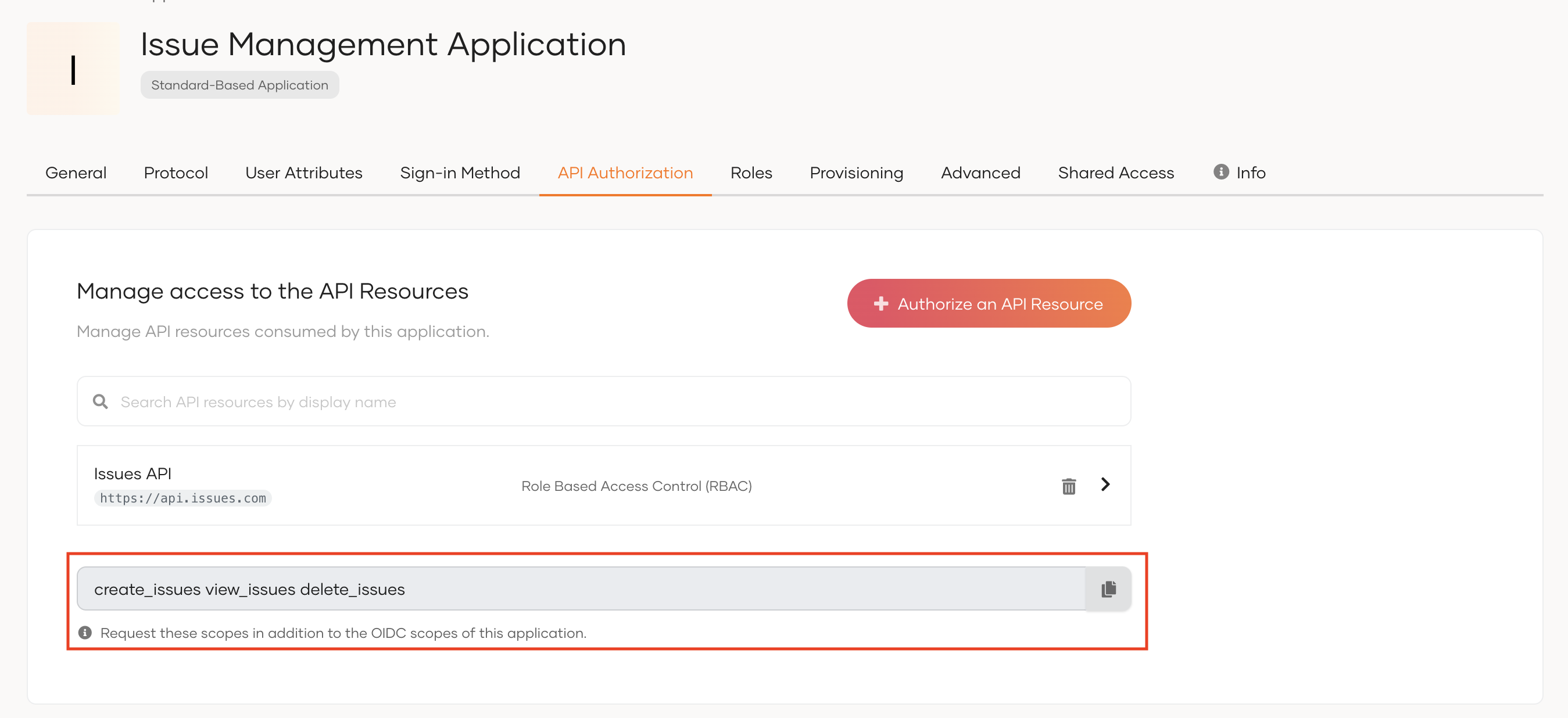
To request scopes for the user:
- Add the new scopes to the
APIScopeparameter of theconfig.jsfile of the sample application. You need to request these new scopes in addition to the OIDC scopes of your application.
To get the scopes:
- On the WSO2 Identity Server Console, log in to the organization(root).
- Go to Applications and select your application.
-
Copy the scopes listed at the end of the API Authorization section
Tip
When you add scopes to the configuration file, add them as comma-separated values.
-
Access the application URL.
-
Try to log in as a user with a group and permission to access the API resource.
If you have disabled
Skip login consentin your application's settings, upon successful login, you will see the permission (scopes) allowed for the user on the user consent page. Click Allow. You will now be redirected to the application. -
You will be able to see the assigned permissions on the
allowedScopesparameter of the authentication response.
If you are switching organizations
If the user switches the organization to another organization, the scopes will be updated according to the roles assigned to the user in the switched organization.