Concurrent-session-based adaptive authentication¶
This page guides you through setting up active user session limiting for a sample application based on a particular criterion.
Scenario¶
Consider a scenario where you want a user with an administrator role that cannot have more than three active concurrent session at a time. If there are three active user sessions, you can either terminate a session or deny authentication for a user.
Prerequisites¶
- See the general prerequisites for all adaptive authenticaiton scenarios.
- You need to set up the sample application.
Configure concurrent-session-based authentication¶
To configure concurrent-session-based authentication:
-
On the management console, go to Main > Identity > Service Providers > List.
-
Click Edit on the
saml2-web-app-pickup-dispatch.comservice provider. -
Expand the Local and Outbound Authentication Configuration section and click Advanced Configuration.
-
You will be redirected to Advanced Configuration, expand Script Based Conditional Authentication.
-
In the Templates section, click on the
+corresponding to Concurrent-Session-Management template.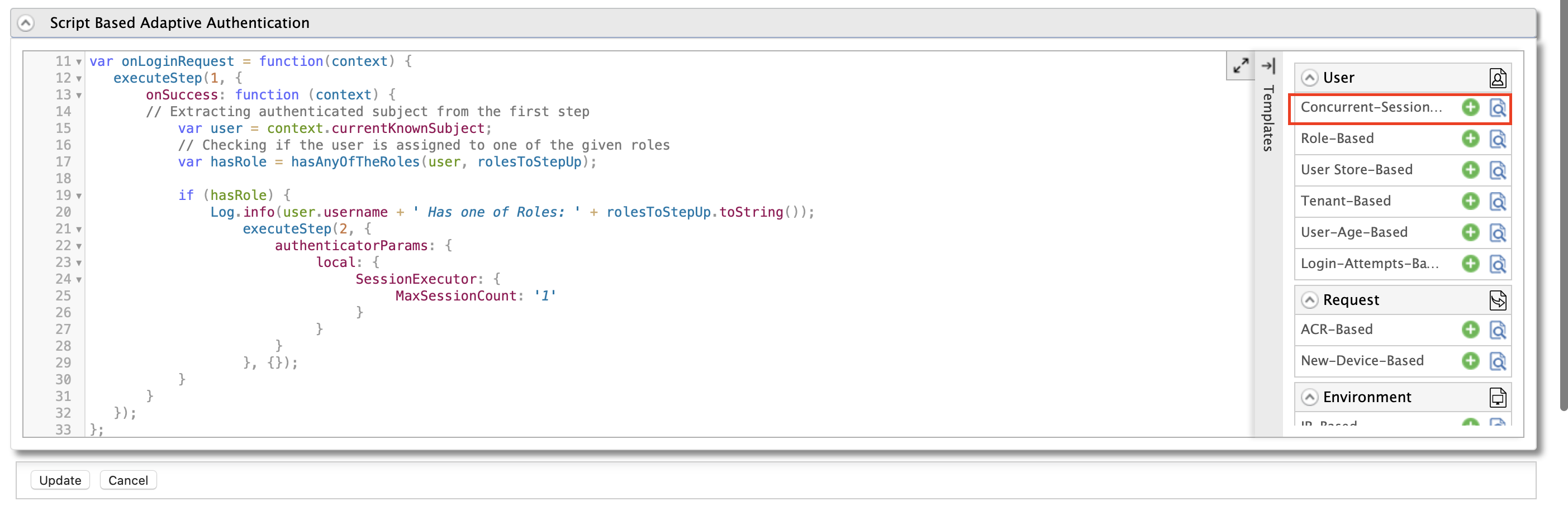
-
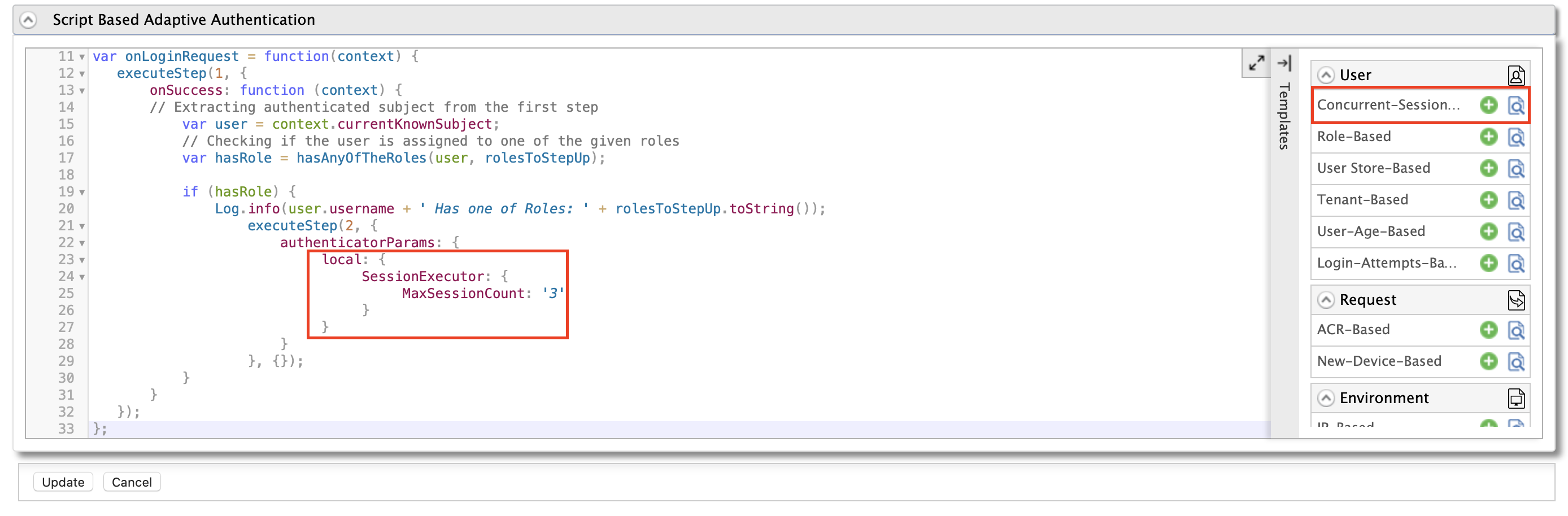
Click Ok to add the authentication script. Update the value of the
MaxSessionCountvariable to3.Note
- The authentication script defines a conditional step that executes the session handling prompt only if the user belongs to an
adminormanagerrole. Here you can specify the value of theMaxSessionCountvariable to indicate the maximum number of sessions allowed. The default value is 1. For this demo, we use3as theMaxSessionCountvalue.
Note
You can configure the
MaxSessionCountvariable via thedeployment.tomlfile in the<IS_HOME>/repository/conf/directory as well. Priority will be given to the configuration in the adaptive authentication script. To configure theMaxSessionCountvariable through thedeployment.tomlfile, append the following configuration with the intended value forMaxSessionCount.authentication.authenticator.session_handler.parameters.max_session_count = “3” - The authentication script defines a conditional step that executes the session handling prompt only if the user belongs to an
-
Click Add Authentication Step.
-
Select Active Sessions Limit from the dropdown under Local Authenticators and click Add Authenticator.
-
Click Update to save your configurations.
Try it out¶
-
Access the sample PickUp application using the following URL:
http://localhost.com:8080/saml2-web-app-pickup-dispatch.com -
Click Login and enter admin/admin credentials.
-
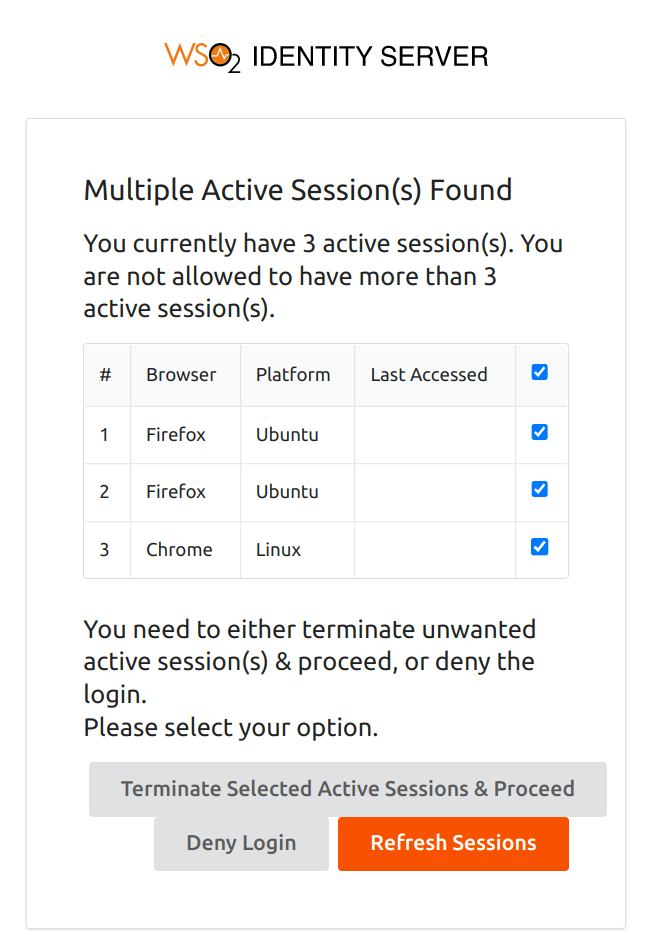
Log in to the same application as admin with three different web browsers, e.g., Firefox, Safari, and Opera.
-
You can terminate one or more active sessions or deny the login.
Tip
- If you select and terminate the active sessions exceeding the maximum limit, you will be navigated to the application home page. Otherwise, you will be re-prompted until the minimum required number of sessions are terminated.
- You can use the Refresh Sessions button to re-check active user sessions.
-
If you deny the login, an authentication error screen appears.