Configuring SMS OTP¶
The SMSOTP authenticator allows you to authenticate user via SMS through WSO2 IS.
Info
For information on MFA concepts, see About MFA.
This document explains how to configure the SMS OTP connector with WSO2 Identity Server.
Let's get started!
Enable SMSOTP¶
Add the following configurations to <IS_HOME>/repository/conf/deployment.toml file to enable SMSOTP
for WSO2 Identity Server.
[authentication.authenticator.sms_otp]
name ="SMSOTP"
enable=true
[authentication.authenticator.sms_otp.parameters]
SMSOTPAuthenticationEndpointURL= "/smsotpauthenticationendpoint/smsotp.jsp"
SMSOTPAuthenticationEndpointErrorPage= "/smsotpauthenticationendpoint/smsotpError.jsp"
MobileNumberRegPage = "/smsotpauthenticationendpoint/mobile.jsp"
RetryEnable = true
ResendEnable = true
BackupCode = true
SMSOTPEnableByUserClaim = true
usecase = "local"
secondaryUserstore = "primary"
SMSOTPMandatory = false
SendOtpToFederatedMobile = false
federatedMobileAttributeKey = "mobile"
CaptureAndUpdateMobileNumber = true
SendOTPDirectlyToMobile = false
redirectToMultiOptionPageOnFailure = false
TokenExpiryTime = 12| Value | Description |
|---|---|
| name | Define the authenticator as SMSOTP. |
| enable | Enable or disable the authenticator. |
| SMSOTPAuthenticationEndpointURL | Authentication endpoint URL of the authenticator. |
| SMSOTPAuthenticationEndpointErrorPage | Error page that will be displayed in an authentication failure. |
| MobileNumberRegPage | Range of usable mobile numbers to send SMSs. |
| RetryEnable | Define whether to retry or not. |
| ResendEnable | Define whether to enable resending the SMSOTP or not in case a user enters an incorrect code. |
| BackupCode | Define whether to use a backup code instead of the actual SMS code or not. |
| usecase | This parameter defines how the username will be retrieved and this has to be configured if the previous authenticator is not a Local Authenticator (eg: Basic Auth). You can configure the following possible values:
|
| secondaryUserstore |
You can define multiple user stores per tenant as comma separated values. Example: secondaryUserstore = "jdbc, abc, xyz"
TipThe user store configurations are maintained per tenant:
|
| SMSOTPMandatory | If the value is true, the second step will be enabled by the admin. The user cannot be
authenticated without SMS OTP authentication. This parameter is used for both super tenant
and tenant in the configuration. The value can be true or false. |
| SendOtpToFederatedMobile |
When the When the When the |
| federatedMobileAttributeKey | This parameter identifies the mobile attribute of the federated authenticator (e.g. Foursquare). Set this parameter if SendOtpToFederatedMobile is set to true. Example: http://wso2.org/foursquare/claims/phone_number |
| SMSOTPEnableByUserClaim | Disable the 'SMS OTP disabling by user' functionality. The value can be either true or
false. If the value is set to true, the user can enable and disable the
SMS OTP according to what the admin selects in SMSOTPMandatory parameter value. |
| CaptureAndUpdateMobileNumber | When SMSOTPMandatory is set to true and the user forgets to
update the mobile number in a specific user profile where this property is set to
true, the user can update a mobile claim with value during the authentication time
and use that mobile number to send OTP.
This update functionality will happen in the first login only. For the next logins, the
updated mobile number will be used. |
| SendOTPDirectlyToMobile | When SMSOTPMandatory is set to true and the user does not exist
in the user store and if the admin sets SendOTPDirectlyToMobile to true
, the user can enter the mobile number in authentication time in a mobile number
request page; the OTP will be directly sent to that mobile number. |
| redirectToMultiOptionPageOnFailure | During a failed attempt enable redirect to the Multi Option Page where the user can select the authentication mechanism. |
| TokenExpiryTime | SMS OTP does not have a default validity period. Therefore, you must explicitly configure it by adding the TokenExpiryTime parameter. The value provided for the parameter is considered in seconds. |
Note
The SMS provider is the entity that is used to send the SMS. The SMSOTP connector has been configured such that it can be used with most types of SMS APIs. Some use the GET method with the client secret and API Key encoded in the URL (e.g., Nexmo), while some may use the POST method when sending the values in the headers and the message and telephone number in the payload (e.g., Clickatell). This could change significantly between different SMS providers. The configuration of the connector in the identity provider would also change based on this.
Configuring the identity provider¶
Now you have to configure WSO2 Identity Server by adding a new identity provider.
-
Download the certificate of the SMS provider by going to the SMS providers website on your browser, and clicking the HTTPS trust icon on the address bar.
Example
If you wish to have NEXMO as your SMS provider, navigate to https://www.nexmo.com, and click the padlock next to the URL on Chrome and download the certificate.
-
Navigate to the
<IS_HOME>/repository/resources/securitydirectory via the terminal and import the downloaded certificate into the WSO2 IS client keystore.keytool -importcert -file <CERTIFICATE_FILE_PATH> -keystore client-truststore.jks -alias "Nexmo" -
You are prompted to enter the keystore password. The default
client-truststore.jkspassword iswso2carbon. -
Log into the management console as an administrator.
-
Navigate to Main tab -> Identity -> Identity Providers -> Add.
-
Give a suitable name (e.g., SMSOTP) as the Identity Provider Name.
-
Go to the SMS OTP Configuration under Federated Authenticators.
-
Select both check-boxes to Enable SMSOTP Authenticator and to make it the Default.
-
Enter the SMS URL, the HTTP Method used (e.g., GET or POST), and the headers and payload if the API uses any.
Info
-
If the text message and the phone number are passed as parameters in any field, include them as
$ctx.numand$ctx.msgrespectively. -
Optionally, enter the HTTP response code the SMS service provider sends when the API is successfully called. Nexmo API and Bulksms API sends 200 as the code, while Clickatell and Plivo send 202. If this value is unknown, leave it blank and the connector checks if the response is 200, 201 or 202.
Click here to configure Nexmo as the service provider.
Follow the steps given below if Nexmo is used as the SMS provider:
- Go to https://dashboard.nexmo.com/sign-up and sign up.
- Once you successfully register, the API key and secret
are displayed. Copy and save them as you need them for the next
step.
Example:
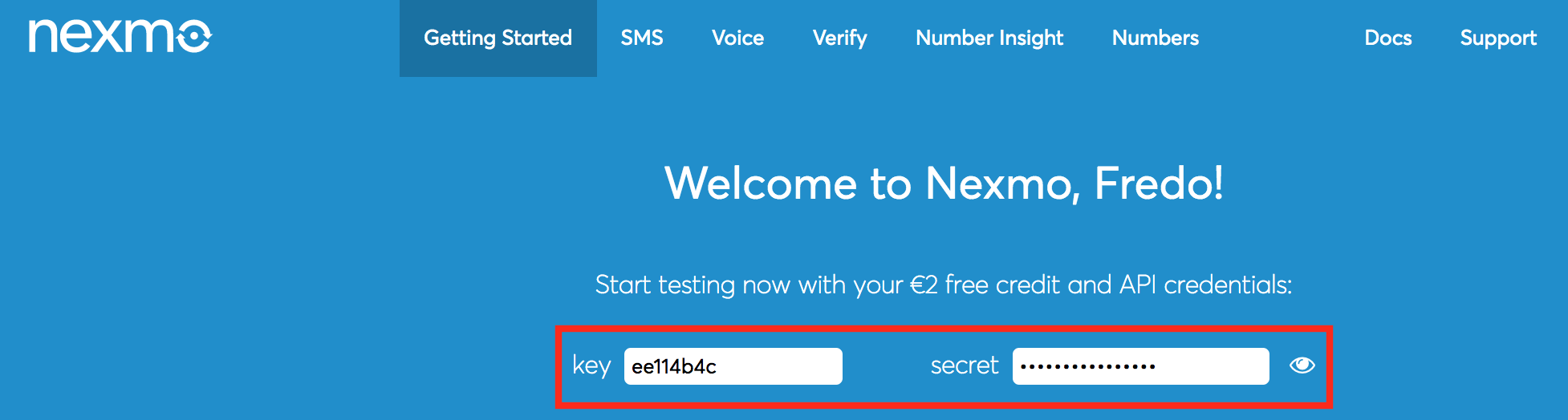
- The Nexmo API requires the parameters to be encoded in the URL,
so the SMS URL would be as follows.
SMS URL https://rest.nexmo.com/sms/json?api_key=&api_secret=&from=NEXMO&to=$ctx.num&text=$ctx.msgHTTP Method POST
Click here to configure Clickatell as the service provider.
Follow the steps given below if Clickatell is used as the SMS provider:
- Go to https://www.clickatell.com/sign-up/ and create an account.
-
The Auth token is provided when you register with Clickatell.
-
Clickatell uses a POST method with headers and the text message and phone number are sent as the payload. So the fields would be as follows.
SMS URL https://api.clickatell.com/rest/messageHTTP Method POSTHTTP Headers X-Version: 1,Authorization: bearer,Accept: application/json,Content-Type: application/json HTTP Payload {"text":" $ctx.msg ","to":[" $ctx.num "]}
Click here to configure Plivo as the service provider.
Follow the steps given below if Plivo is used as the SMS provider:
- Sign up for a free Plivo trial account .
-
Phone numbers must be verified at the Sandbox Numbers page (add at least two numbers and verify them).
-
The Plivo API is authenticated with Basic Auth using your
AUTH IDandAUTH TOKEN, Your PlivoAUTH IDandAUTH TOKENcan be found when you log in to your dashboard. - Plivo uses a POST method with headers, and the text message and
phone number are sent as the payload. So the fields would be as
follows.
SMS URL https://api.plivo.com/v1/Account/{auth_id}/Message/HTTP Method POSTHTTP Headers Authorization: Basic ********,Content-Type: application/jsonHTTP Payload {"src":"+94*********","dst":"ctx.num","text":"ctx.msg"}
Click here to configure Bulksms as the service provider.
Follow the steps given below if Bulksms is used as the SMS provider:
- Go to https://www2.bulksms.com/login.mc and create an account.
- While registering the account, verify your mobile number and
click Claim to get free credit.
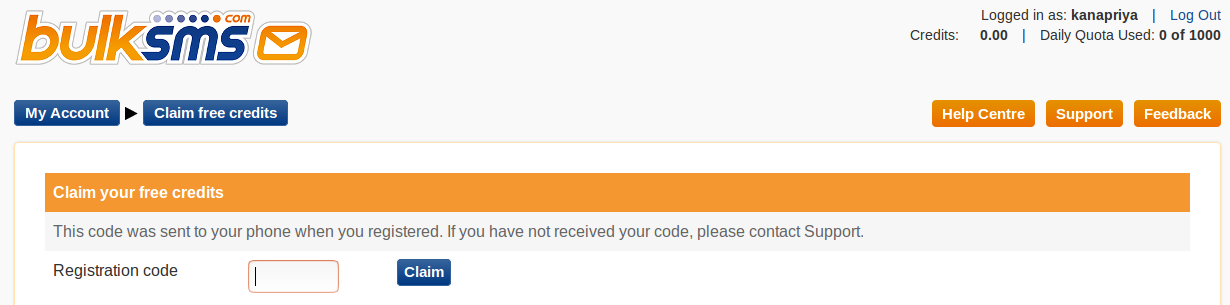
Bulksms API authentication is performed by providing the username and password request parameters.- Bulksms uses the POST method and the required parameters are to
be encoded in the URL. So the fields would be as follows.
SMS URL https://bulksms.vsms.net/eapi/submission/send_sms/2/2.0?username=&password=&message=$ctx.msg&msisdn=$ctx.numHTTP Method POSTHTTP Headers Content-Type: application/x-www-form-urlencoded
Click here to configure Twilio as the service provider.
You will need a Twilio-enabled phone number (a phone number purchased through Twilio) to send SMS using Twilio.
Follow the steps given below if Twilio is used as the SMS provider:
- Go to https://www.twilio.com/try-twilio and create an account.
-
While registering the account, verify your mobile number and click on console home https://www.twilio.com/console to get free credit (Account SID and Auth Token).
-
Twilio uses the POST method with headers, and the text message and phone number are sent as the payload. The fields would be as follows.
SMS URL https://api.twilio.com/2010-04-01/Accounts/{AccountSID}/SMS/Messages.jsonHTTP Method POSTHTTP Headers Authorization: Basic base64{AccountSID:AuthToken}HTTP Payload Body=$ctx.msg&To=$ctx.num&From=urlencode{FROM_NUM} -
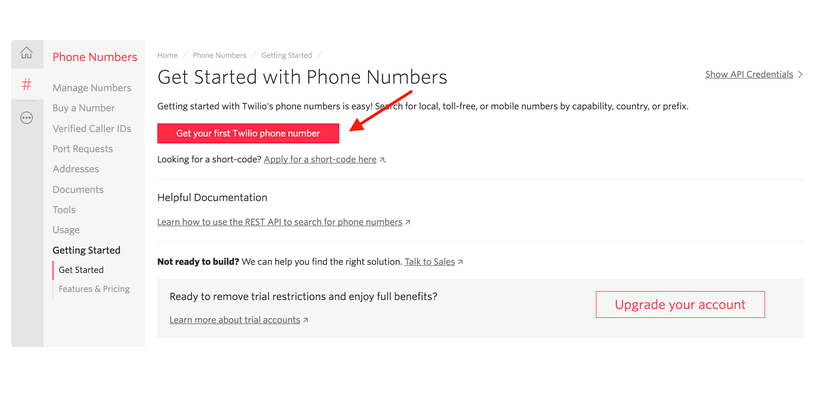
After signing up for your trial account, navigate to the Phone Numbers page in your console. You’ll see the phone number that has been selected for you. Note the phone number’s capabilities, such as "Voice", "SMS", and "MMS".
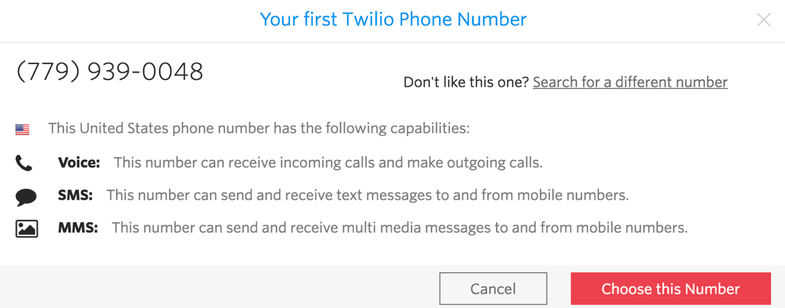
Get your first Twilio phone number and use that as the
FROM_NUMin your HTTP Payload. For more information, see this tutorial in the Twilio documentation. -
-
Click Register .
Configuring the service provider¶
The next step is to configure the service provider.
-
Navigate to Main tab -> Identity -> Service Providers -> Add.
-
Give a suitable name (e.g., saml-dispatch) as the Service Provider Name.
-
Configure Inbound Authentication for the service provider. For instructions, see Configuring Inbound Authentication for a Service Provider
-
Go to Claim configuration and select the
http://wso2.org/claims/mobileclaim for the Subject Claim URI.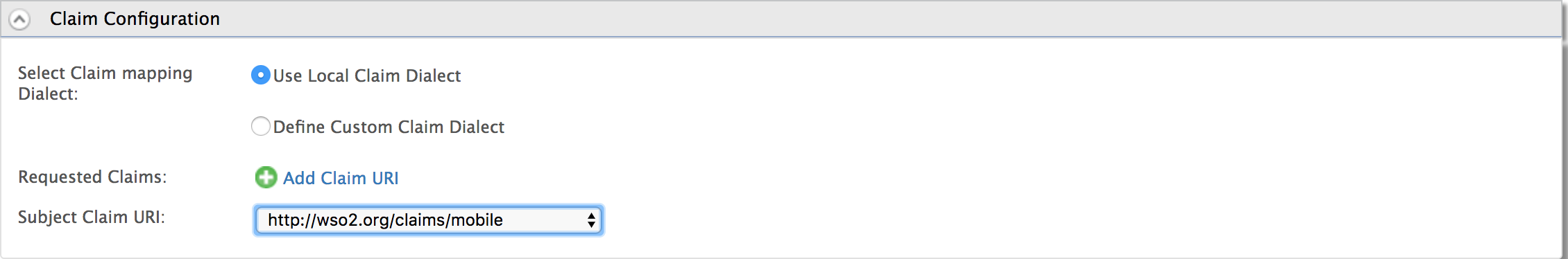
-
Go to Local and Outbound Authentication Configuration section.
-
Select the Advanced configuration radio button option.
-
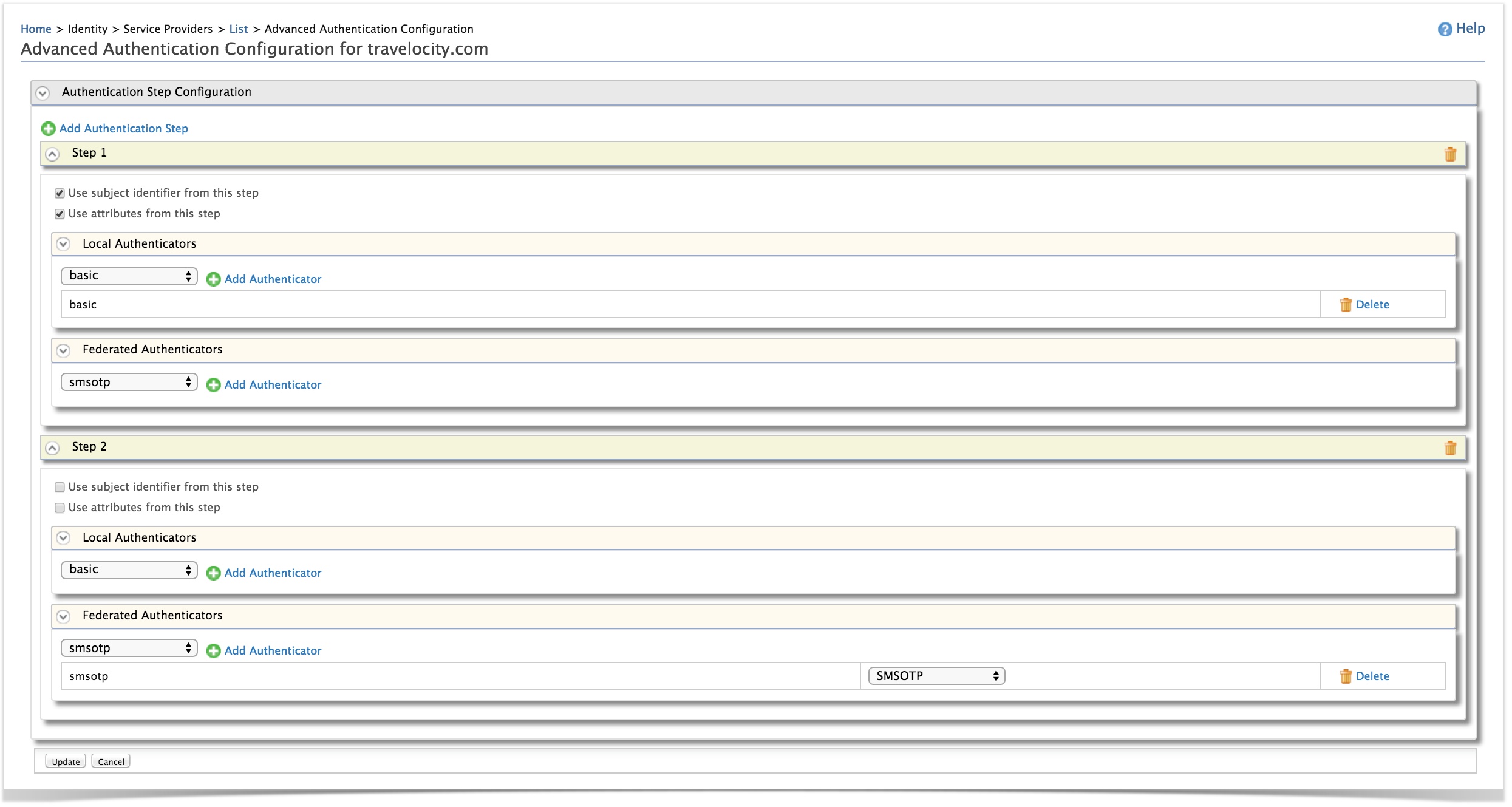
Creating the first authentication step:
-
Click Add Authentication Step.
-
Click Add Authenticator that is under Local Authenticators of Step 1 to add the basic authentication as the first step.
Adding basic authentication as a first step ensures that the first step of authentication will be done using the user's credentials that are configured with the WSO2 Identity Server
-
-
Creating the second authentication step:
-
Click Add Authentication Step.
-
Click Add Authenticator that is under Federated Authenticators of Step 2 to add the SMSOTP identity provider you created as the second step.
SMSOTP is a second step that adds another layer of authentication and security.
-
-
-
Click Update to save the changes.
You have now added and configured the service provider.
Updating the mobile number of the user¶
Follow the steps given below to update the mobile number of the users in WSO2 IS.
-
Navigate to Main -> Identity -> Users and Roles -> List -> Users to view existing users.
-
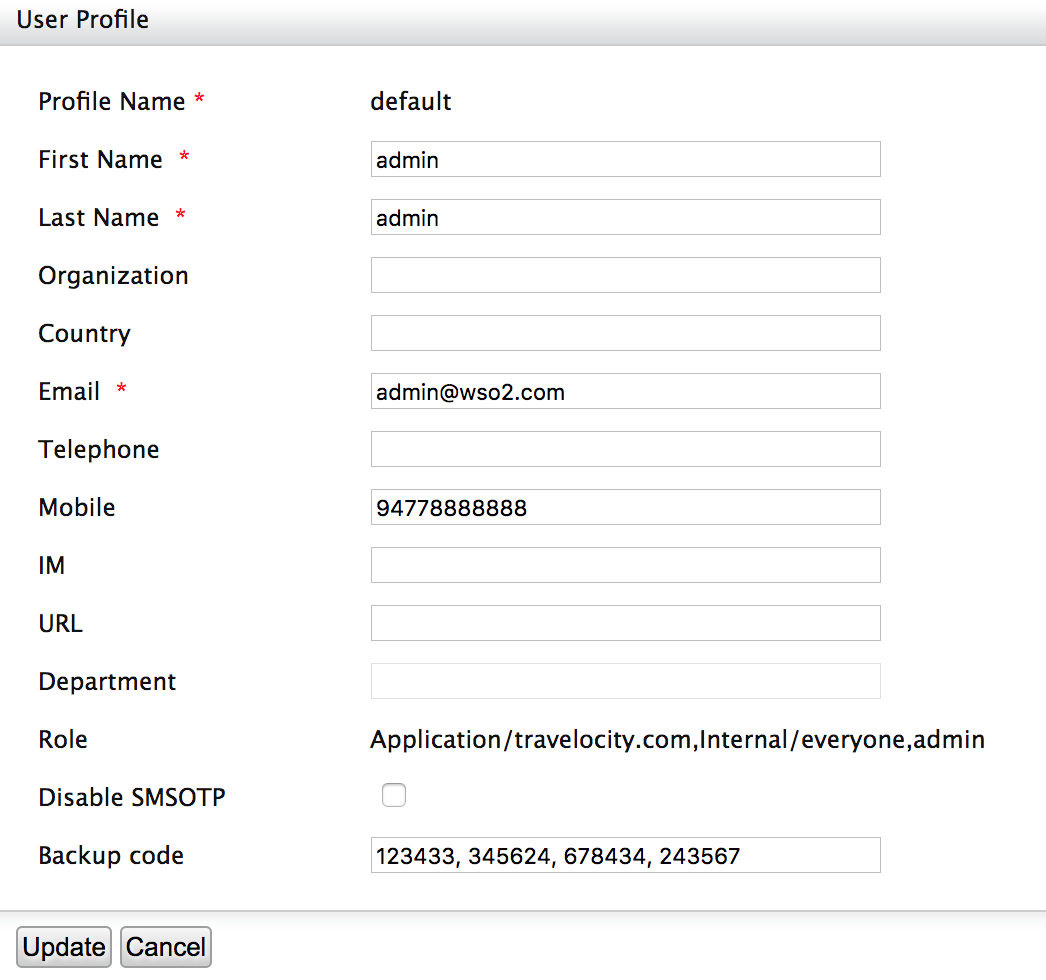
Click User Profile of the user you want to edit and update the mobile number.
Warning
The mobile number needs to be in the following format.
Example: 94778888888
NOTE: If the format is wrong you would not get the text message.
Note
Make sure the number is registered with an SMS provider in order to send the SMS. For this tutorial, you can use the mobile number that was used to register with the SMS provider.
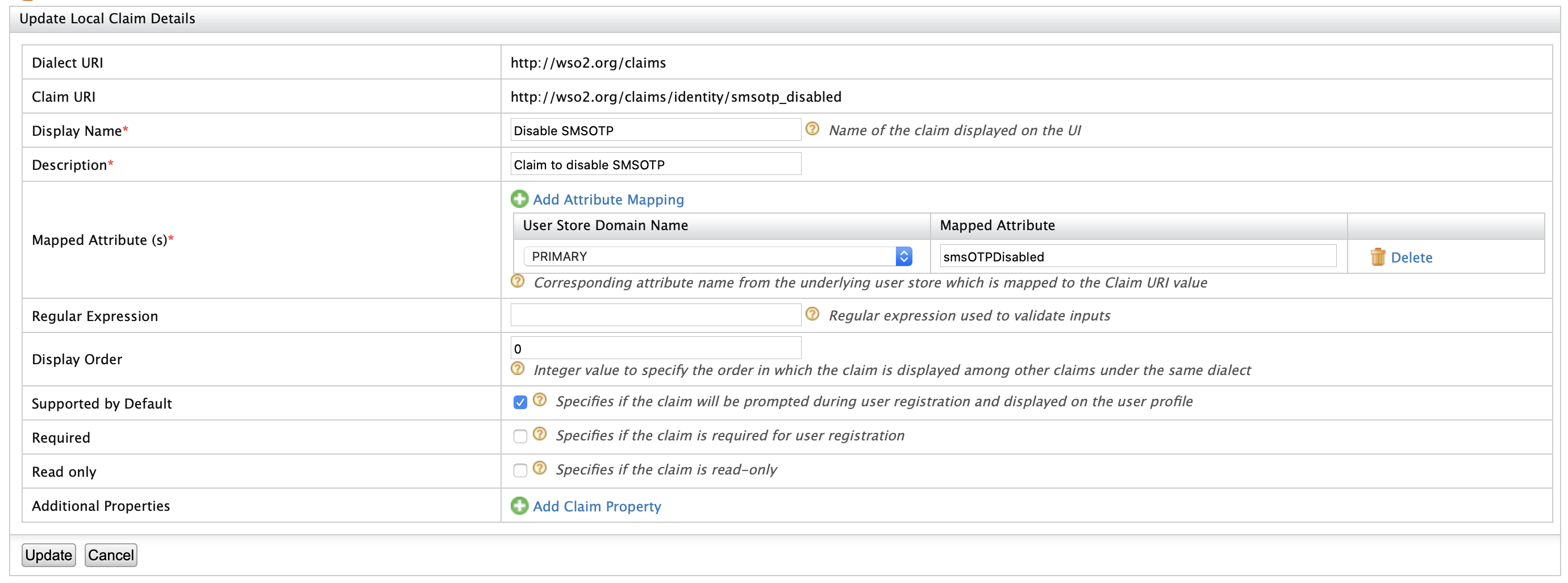
Add Disable SMSOTP option for Users¶
-
Navigate to Main -> Identity -> Claims -> List -> Click
http://wso2.org/claims. -
Find Claim
Disable SMSOTPand click Edit. -
Enable
Supported by Defaultoption and click Update.
Now Disable SMSOTP option is available for the user.
Note
To verify whether the option is available for the users, navigate to a user
profile of a user and check Disable SMSOTP option is available.
Configuring backup codes for SMSOTP¶
Optionally , you can configure back up codes when SMS OTP is disabled. To configure backup codes, follow the steps given below.
Adding OTP backup codes claim¶
-
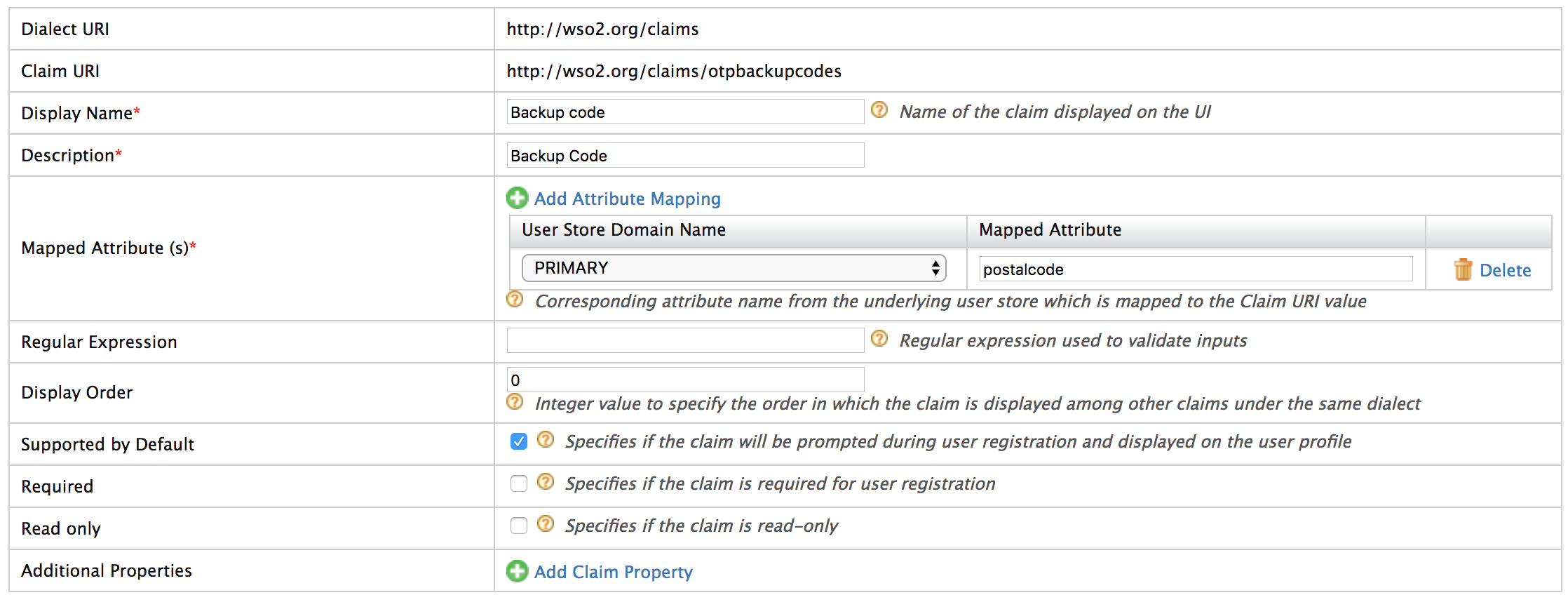
Navigate to Main menu -> Identity -> Claims -> Add -> Add Local Claim.
-
Enter
http://wso2.org/claims/otpbackupcodesas the value for Claim Uri. -
Add a Display Name and Description. For example,
Backup Code. -
Enter
postalcodeas the value for Mapped Attribute. -
Select Supported by Default.
-
Click Add.
Add backup codes for users¶
-
Navigate to Main -> Identity -> Users and Roles -> List -> Users.
-
Click User Profile of a preferred user and update the backup codes so that the user can disable SMS OTP by selecting Disable SMS OTP if required.
Info
A backup code can have any number of digits, and you can define many backup codes as comma separated values.
Info
For a full tutorial demonstrating multi-factor authentication with SMSOTP using a sample application, see Configuring Multifactor Authentication.