Configuring Roles for an Identity Provider¶
Role mapping is an important task when adding an identity provider to the Identity Server, as the roles of the Identity Server are different from the roles of the identity provider that you connect.
To configure the roles of the identity provider:
- On the Management Console, go to Main > Identity > Identity Providers section.
- Click List, select the identity provider you want to edit, and click on the corresponding Edit link.
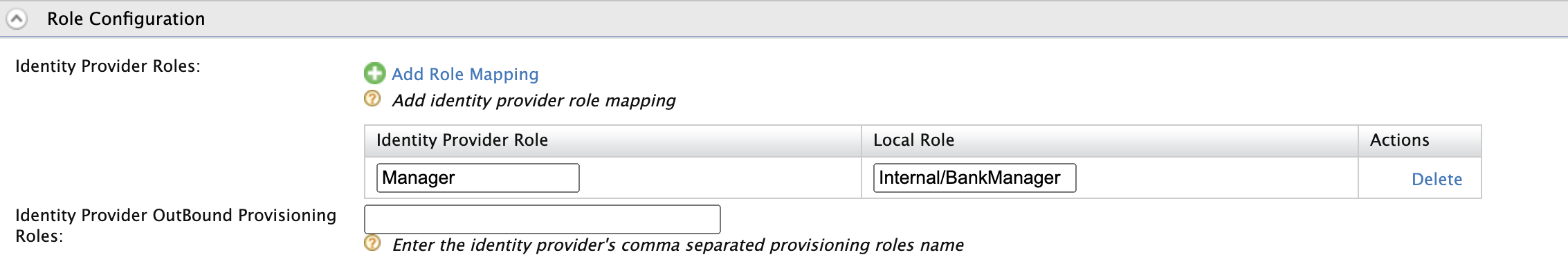
- Expand the Role Configurations tab, and click Add Role Mapping.
-
Enter the Identity Provider Role and map it to the Local Role available in the Identity Server.
Important
Note that you can only map local roles that belong to the Internal domain. Learn more about creating local roles on Identity Server.
-
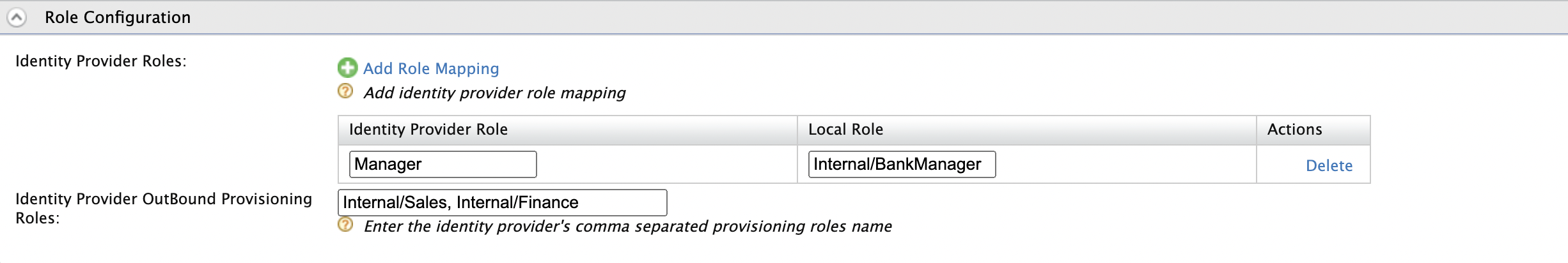
Enter the roles that you wish to provision on the Identity Provider OutBound Provisioning Roles field.
Info
All users who are assigned to this role will be provisioned from the Identity Server to the identity provider. You can provision users that have multiple roles by specifying the roles in a comma-separated list.
Note
The Federated IDP role claim value separator is used to separate multiple roles in the role claim value obtained from the Identity Provider. In order to configure the Federated IDP role claim value separator, add the following configuration to the deployment.toml file in <carbon-home>/repository/conf and restart the server.
[federated.idp]
role_claim_value_attribute_separator=","If this is not configured and if the no MulitAttributeSeparator is configured, the default separator will be " ,,, ".