Login attempts¶
Secure user accounts from unauthorized access by configuring the login attempts policy in WSO2 Identity Server.
Configuration instructions¶
To manage login attempts settings, do the following:
- In the WSO2 Identity Server Console, go to Login & Registration > Login Security > Login Attempts.
- Adjust the settings according to your security requirements.
- Click Update to save the changes.
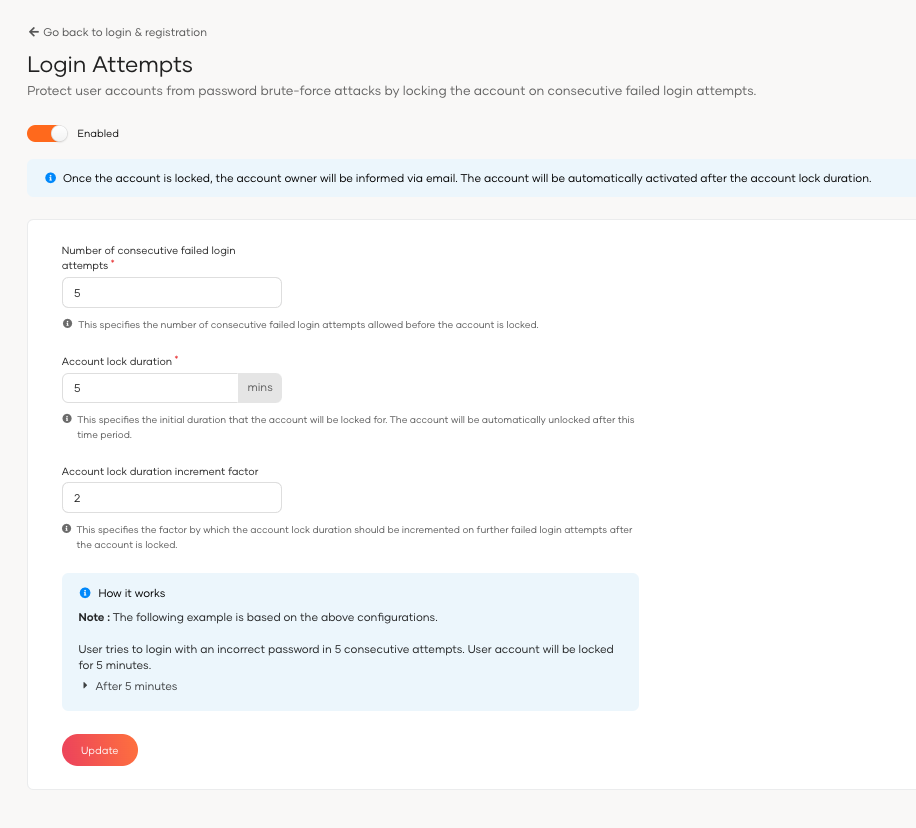
Parameters¶
| Parameter | Description |
|---|---|
Number of Consecutive Failed Login Attempts |
The count of consecutive incorrect login attempts before locking the account. |
Account Lock Duration |
The time in minutes an account stays locked after reaching the failed attempt limit. |
Account Lock Duration Increment Factor |
The rate at which the lock duration increases after successive lockouts. |
Info
- In the WSO2 Identity Server login pages, a generic error message is displayed by default to end-users in the event of login failures. To show more specific error messages on the login page, the following properties can be configured in the
deployment.tomlfile, which is located in the<IS_HOME>/repository/confdirectory.
Basic authenticator configurations:
[authentication.authenticator.basic.parameters]
showAuthFailureReason = true
showAuthFailureReasonOnLoginPage = true
Email OTP authenticator configurations:
[authentication.authenticator.email_otp.parameters]
showAuthFailureReason = true
showAuthFailureReasonOnLoginPage = true
TOTP authenticator configurations:
[authentication.authenticator.totp.parameters]
showAuthFailureReason = true
showAuthFailureReasonOnLoginPage = true