Add federated login¶
WSO2 Identity Server lets you add and configure external Identity Providers (IdP) so that users can bring their identities in these external IdPs and log in to applications. Follow the guides below to learn how you can integrate the external IdP of your choice with WSO2 Identity Server.
Create a connection¶
You can register an external IdP in WSO2 Identity Server by creating a connection. WSO2 Identity Server supports a variety of connections for your convenience. Select your preferred connection and follow the guide to learn how to configure it.
Configure JIT provisioning¶
When a user logs in with an external identity provider using the same email address registered in a local account, JIT-provisioning overrides the attributes of the local account with the attributes received from the external identity provider.
WSO2 Identity Server, by default, disables Just-In-Time (JIT) user provisioning for your external identity provider.
To enable JIT-provisioning,
-
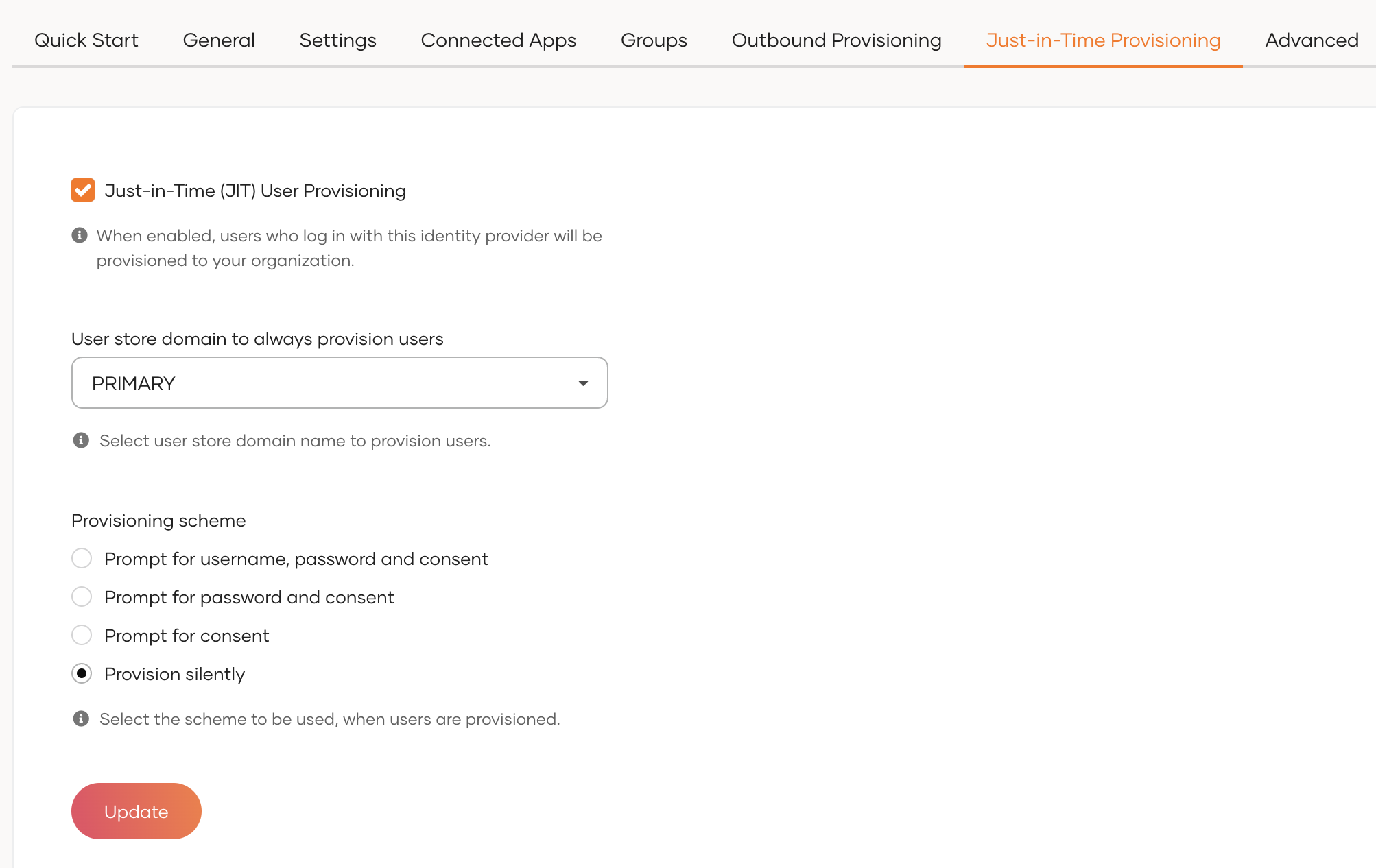
On the WSO2 Identity Server Console, click Connections and select the relevant connection.
-
Go to the Just-in-Time Provisioning tab of the selected connection.
-
Check/Uncheck the Just-in-Time (JIT) User Provisioning checkbox to enable/disable it.
-
Click Update to save the changes.
Note
-
Learn more about JIT provisioning configurations in configure JIT user provisioning.
-
You can use the identity provider APIs to customize the attribute syncing behavior between the external identity provider and WSO2 Identity Server.
Map groups with WSO2 Identity Server¶
Configure External Connection's Group attribute¶
To add groups to a connection on WSO2 Identity Server:
-
On the WSO2 Identity Server Console, go to Connections.
-
Select your connection and go to its Attributes tab.
-
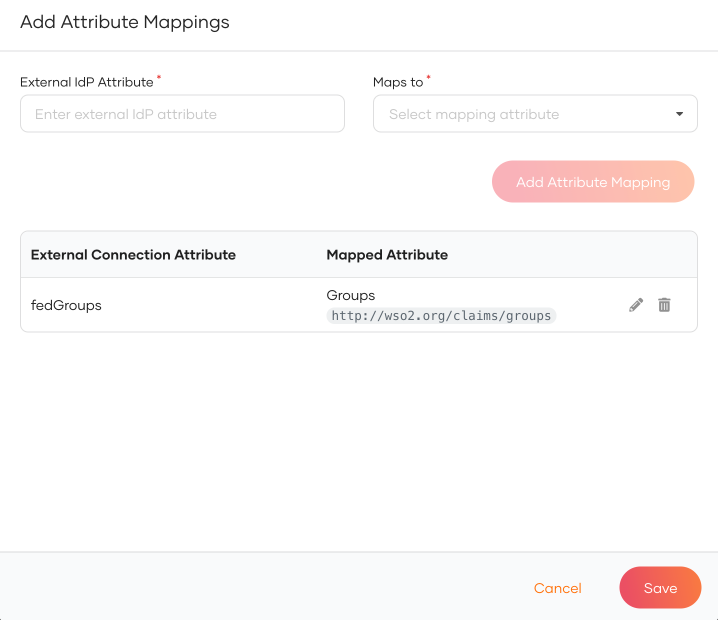
Click Add Attribute Mapping to add a new attribute mapping.
-
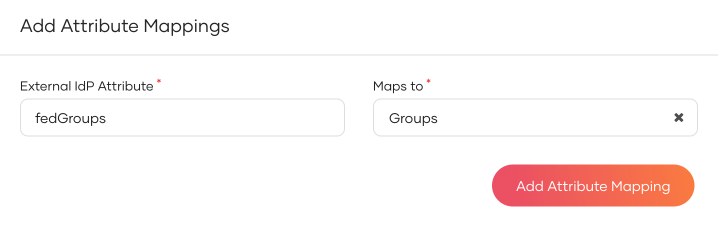
Enter the External IdP Attribute of the connection and map it to the Groups attribute of Asgardeo.
-
Click Add Attribute Mapping and then click Save.
-
Click Update to save the changes.
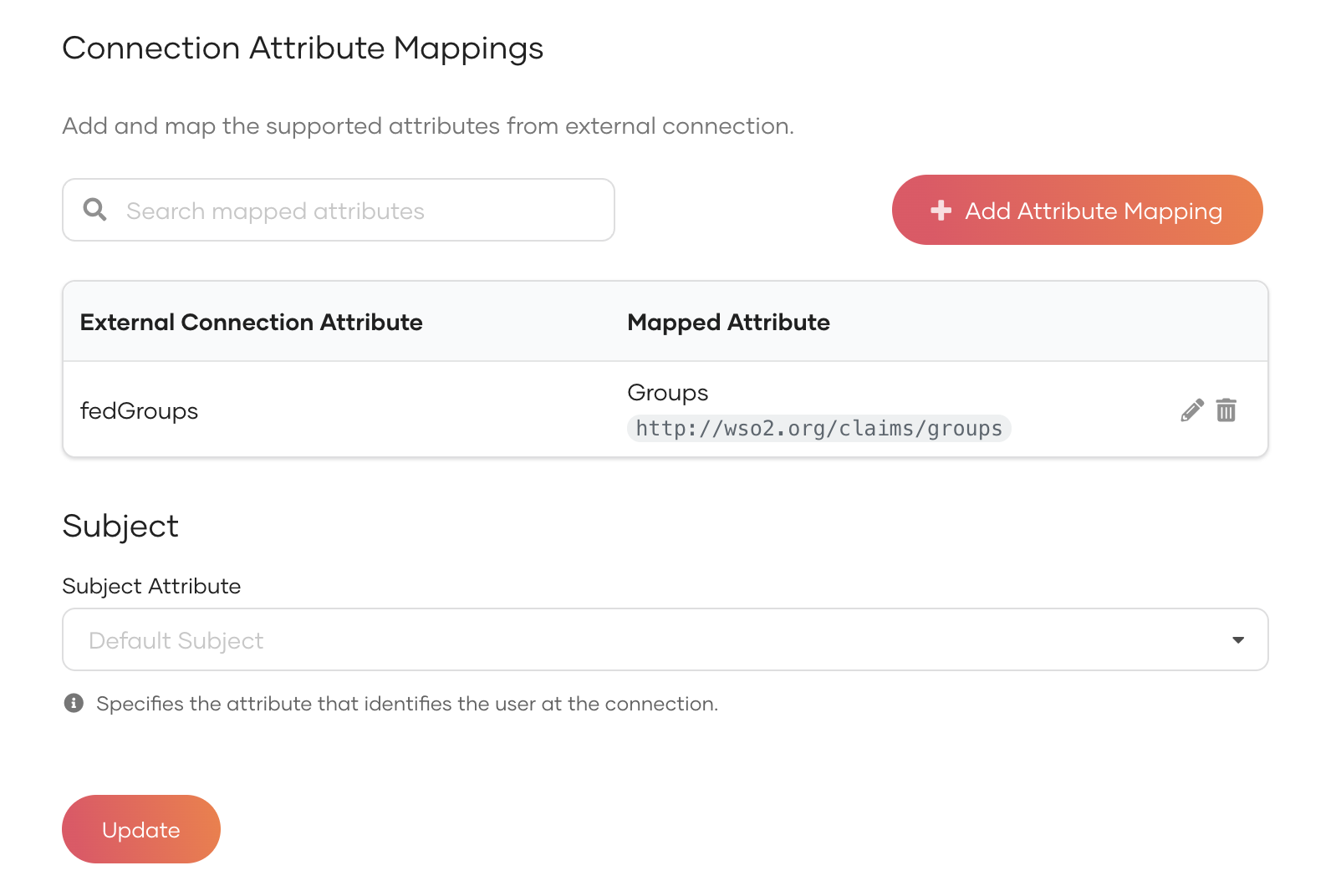
Add groups to connections¶
Follow the steps below to add the groups from your connection to Asgardeo:
- On the Asgardeo Console, go to Connections.
- Select your connection and go to its Groups tab.
-
Click New Group and enter the group name. Be sure to enter the exact group name that will be returned from the connection.
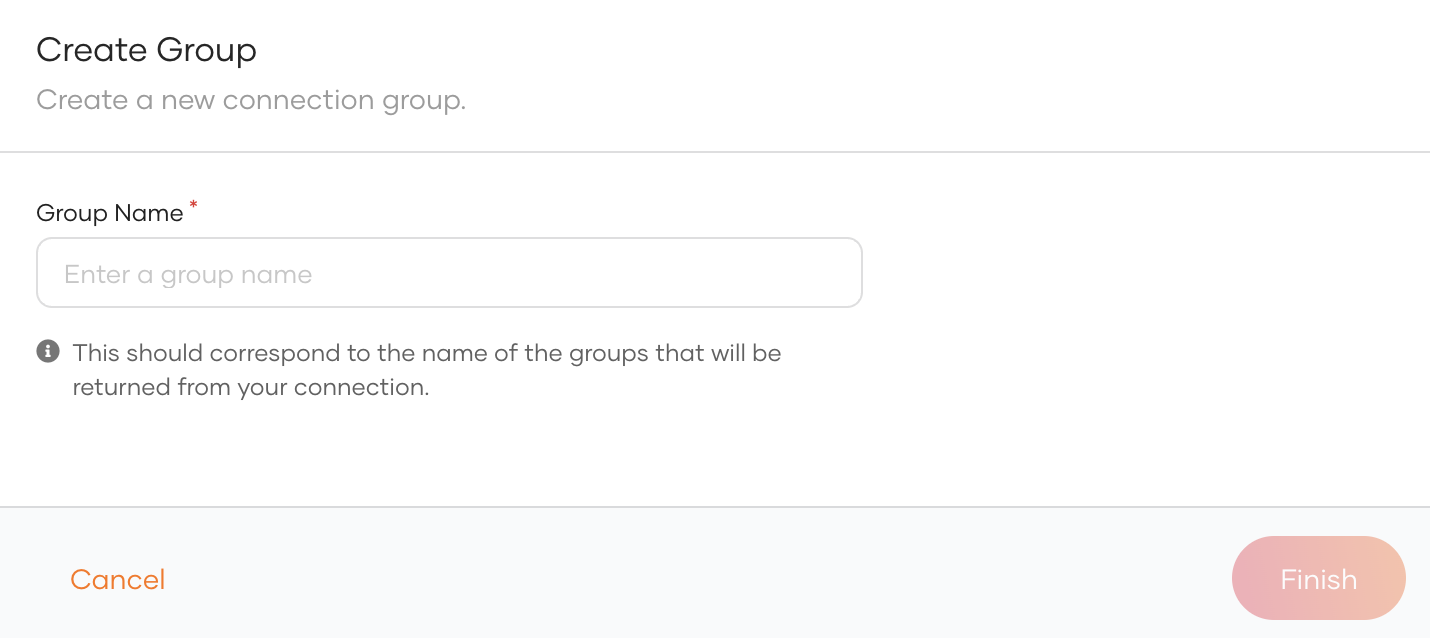
-
Click Finish to add the group information.
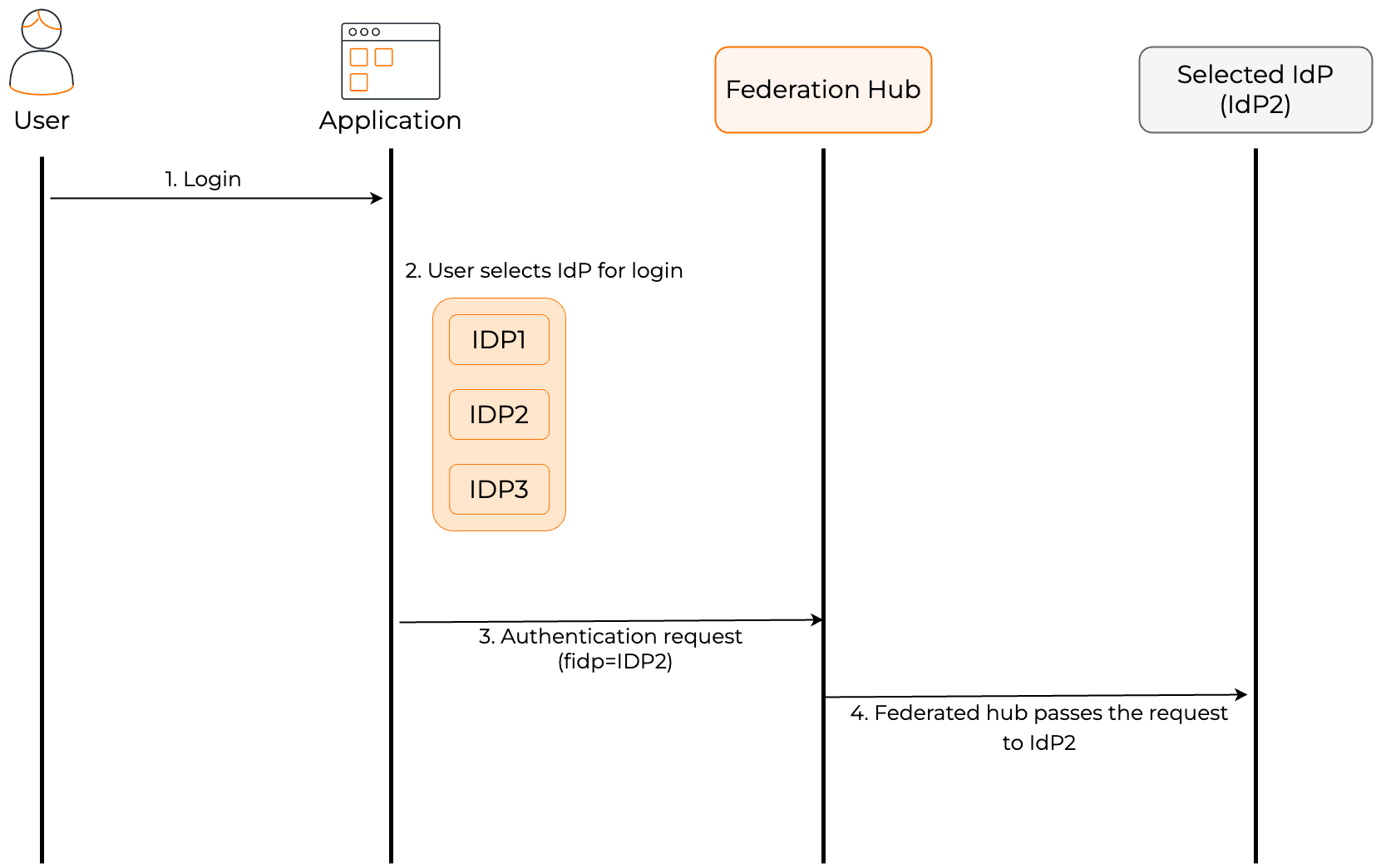
Add connections to federation hub¶
Federation hub is a collection of multiple IdPs configured on WSO2 Identity Server. On the federation hub, each IdP is recognized by the home realm identifier of the IdP.
The following diagram illustrates an authentication flow involving a federated hub.
Note
On the application's login page, you can support either local and federated authentication or just federated authentication. This can be done by setting the proxy_mode configuration to one of the following modes:
smart |
Allow both local and federated authentication |
dumb |
Allow only federated authentication. The home realm identifier must be configured to operate in this mode. If it is not configured, a separate screen should be displayed to get it from the user. |
proxy_mode by opening the deployment.toml file in the <IS_HOME>/repository/conf directory
and setting one of the above modes as follows.
[authentication]
proxy_mode="smart"
To add a connection to federation hub,
-
On the WSO2 Identity Server Console, click Connections and select the relevant connection.
-
Go to the Advanced tab of the selected connection.
-
Turn on the Federation Hub toggle to add the connection.
-
Enter the Home Realm Identifier. This value is an identifier used when your application uses a federated IdP. If a user selects this IdP and sends an authentication request, the fidp query parameter will be populated with this value. (example: fidp = googleIdP)
-
Click Update to save the changes.
Delete a connection¶
Before you begin
If your connection has applications associated with it, you will not be able to delete the connection.
Before deleting such connections:
- Check the associated applications from the Connected Apps tab of the connection.
- Click on an application that uses the connection and you will be redirected to the Login Flow tab of the respective application.
- Remove the connection from the sign-in flow of the associated applications.
- Repeat steps 2 and 3 for all listed applications.
- Proceed to delete the connection.
To delete a connection:
- On the WSO2 Identity Server Console, go to Connections.
- Click Set up and navigate to the General tab.
-
At the bottom of the page, click the button in the Delete connection.
Note
You cannot delete connections that are available by default.
-
Select the checkbox and confirm your action.