Add login with WS-Federation¶
You can add login with WS-Federation to your applications and enable users to log in with their external identities. Follow this guide to register a WS-Federation connection and add it to the login flow of your application.
Register the WS-Fedration IdP¶
Let's register the WS-Fed IdP in WSO2 Identity Server.
-
On the WSO2 Identity Server Console, go to Connections.
-
Click Create Connection and select Custom Connector.
-
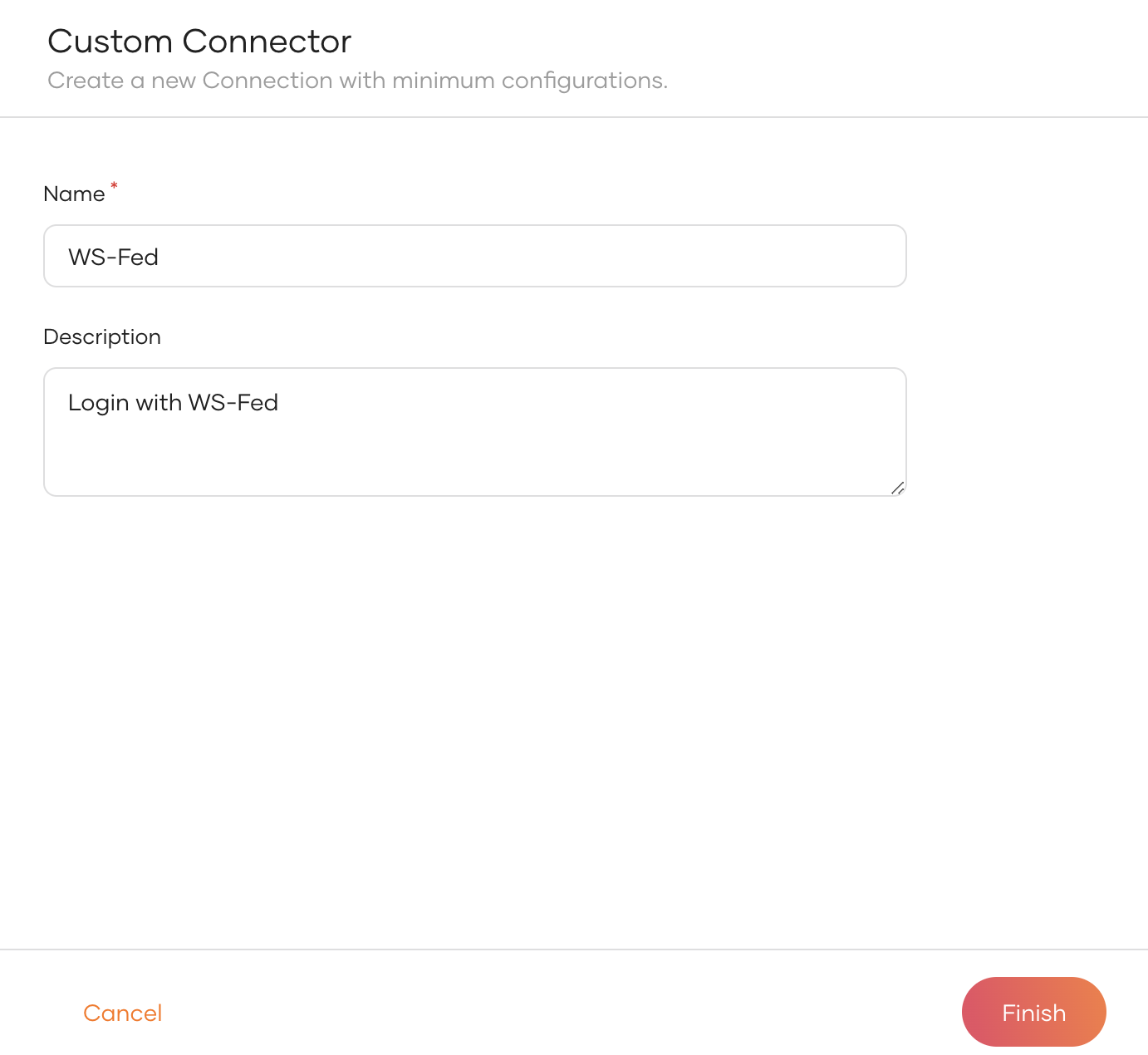
Provide a name and a description for the connector and click Finish.
-
On the created custom connector, go to the Settings tab.
-
Click New Authenticator, select WS-Federation and click Next.
-
Enter the following details and click Finish.
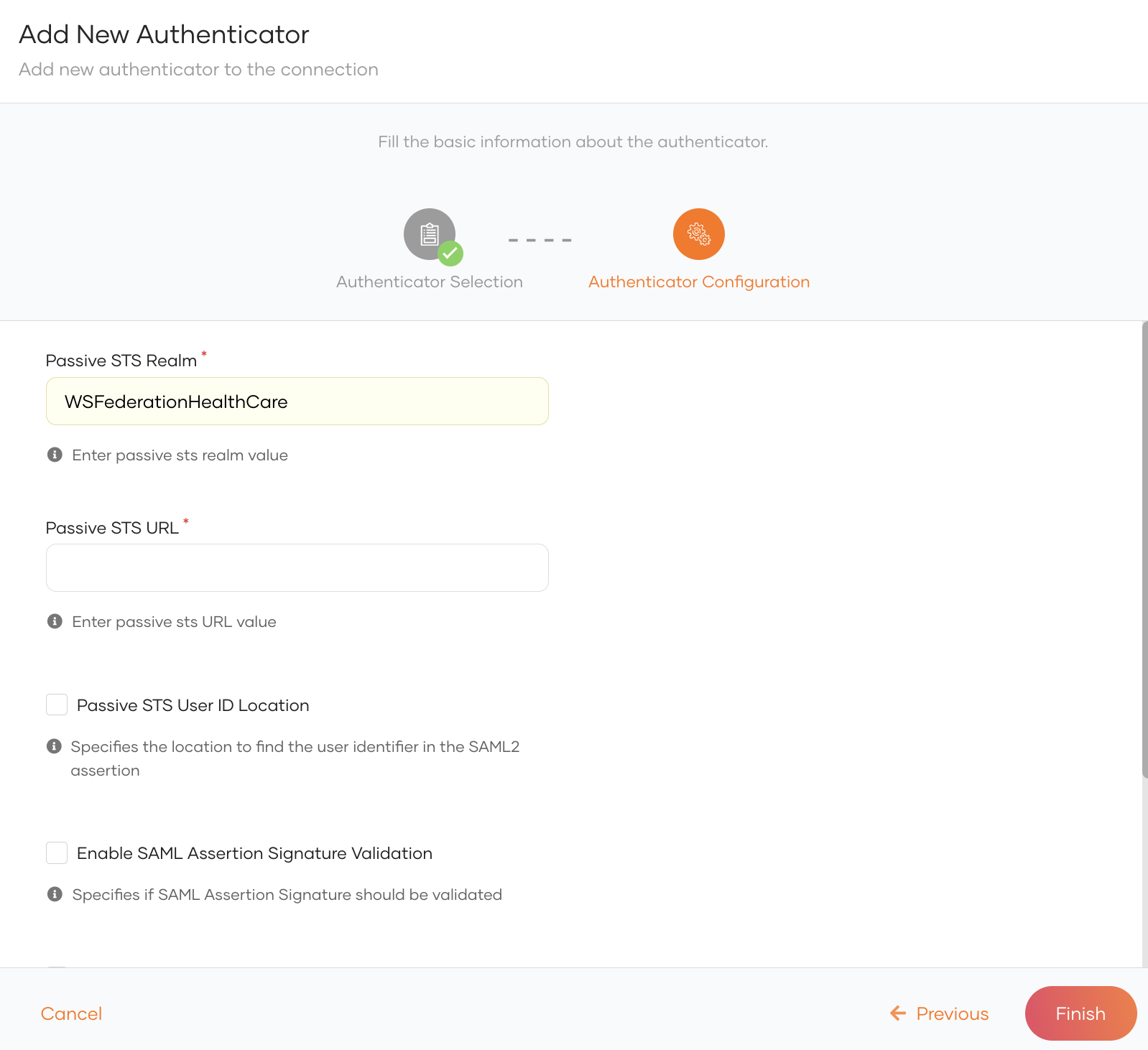
Parameter Description Passive STS Realm Value of your choice that serves as the unique identifier for the realm. e.g. WSFederationHealthCarePassive STS URL Passive STS endpoint of the IdP. e.g. for WSO2 Identity Server, it is
.https://localhost:9443/passivestsPassive STS User ID Location Select whether the User ID is found in the Name Identifieras part of the authentication request or found among the claims.Enable SAML Assertion Signature Validation Select to enable validation for the signature sent over the SAML assertion. Enable SAML Assertion Audience Validation Select to enable validation for the audience attribute sent in the SAML assertion. Additional Query Parameters Include any other parameters that are required by the external IdP.
Enable WS-Fed for login¶
Before you begin
You need to register an application with WSO2 Identity Server. You can register your own application or use one of the sample applications provided.
-
On the WSO2 Identity Server Console, go to Applications.
-
Select your application, go to the Login Flow tab and add WS-Federation from your preferred editor:
-
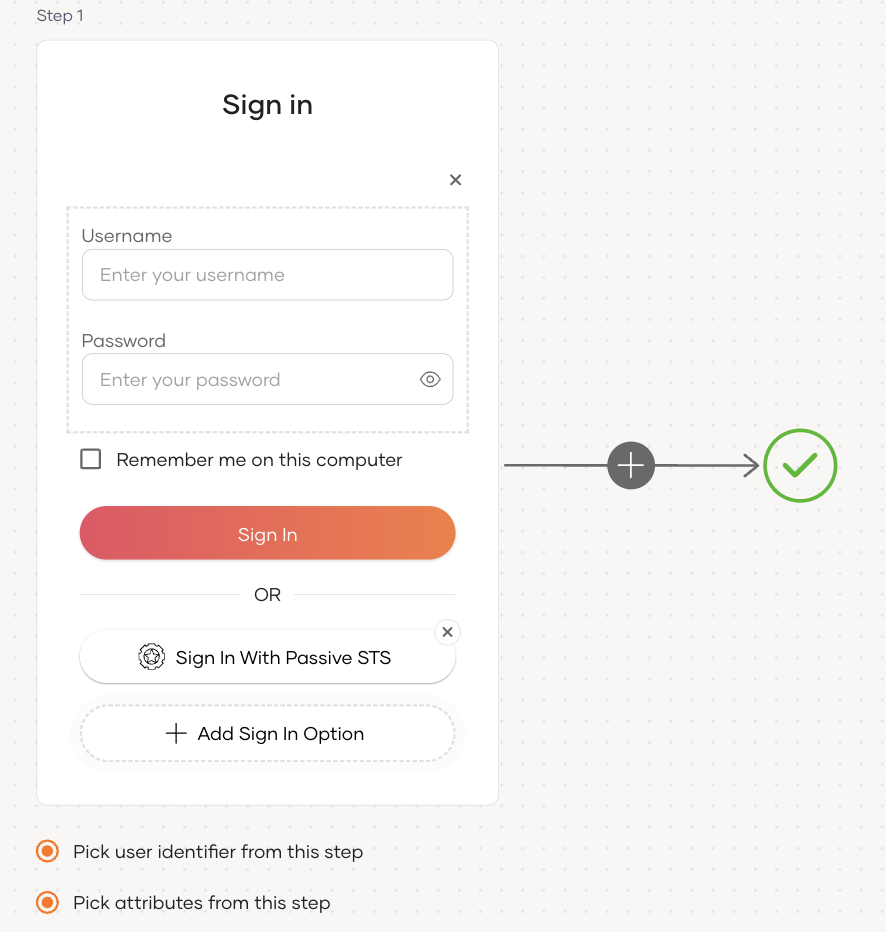
Click Add Sign In Option to add a new authenticator to the first step.
-
Select the WS-Federation connection.
-
Click Confirm to add login with WS-Federation to the sign-in flow.
Recommendations
It is recommended to add your social and enterprise connections to the first authentication step as they are used for identifying the user.
-
-
Click Update to save your changes.
Configure user attributes¶
Configuring attributes for an Identity Provider (IdP) involves mapping the attributes available in the external IdP to local attributes. This is done so that WSO2 Identity Server can identify the user attributes in the response sent from the external IdP.
To do so,
-
On the WSO2 Identity Server Console, click Connections.
-
Select the relevant IdP connection from the list and click Set up.
-
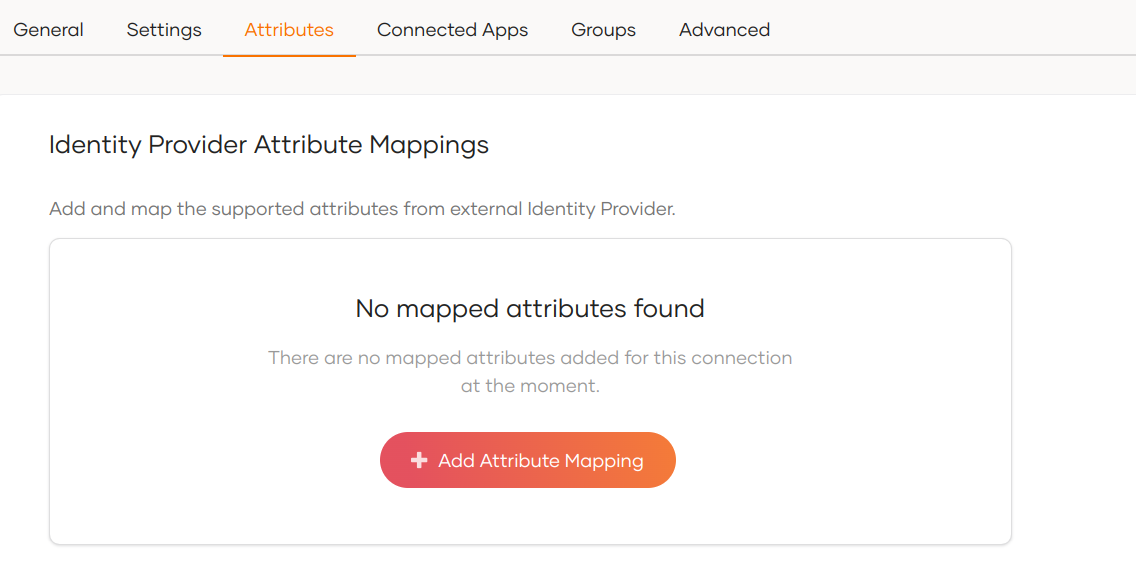
Go to the Attributes tab and under Identity Provider Attribute Mappings, click Add Attribute Mapping.
-
Enter the external attribute, select the corresponding local attribute to which it maps and click Add Attribute Mapping.
-
Click Save to save the entries.
-
Under Subject, select a Subject Attribute that will be used to uniquely identify the user.
-
Under Provisioning Attributes Selection, select the required attributes that needs to be sent in the response to provision the user in WSO2 Identity Server.
-
Click Update to save the changes.