Add login with IWA¶
Integrated Windows Authentication (IWA) is a popular authentication mechanism used to authenticate users on Microsoft Windows servers. It uses Kerberos or NTLM to authenticate users based on an encrypted ticket exchange system between a browser and a server.
Follow the sections below to configure IWA as a local or a federated authenticator in WSO2 Identity Server.
Set up Active Directory for IWA¶
Follow the steps below to register WSO2 Identity Server in Active Directory (AD).
-
Add a DNS host entry in Active Directory (AD) to map the IP address of WSO2 Identity Server to a hostname.
Info
- If there are multiple Kerberos domains, WSO2 Identity Server should have a virtual host name for each Kerberos domain.
- The DNS entry is generally created by taking the first part of the hostname and appending the Active Directory (AD) domain to it. For example, if the AD domain is
wso2.com, the final result will be,idp.wso2.com - Kerberos does not work with IP addresses, it only relies on domain names and correct DNS entries.
-
Add an entry to the DNS tool of the local machine in which WSO2 Identity Server is running to map the specified host name to the local IP address.
-
Create a service account in the Active Directory for WSO2 Identity Server or use an existing account.
Note
The account used for WSO2 Identity Server needs to be different from the one used by the user to login to the application.
-
Run the following commands to register WSO2 Identity Server as a service principal in Active Directory:
Note
The format of these commands is:
[setspn -A HTTP/<url of the identity server> <service_account>]setspn -A HTTP/idp.wso2.com <username> setspn -A HTTP/idp <username>
Set up WSO2 Identity Server for IWA¶
Follow the steps below to configure WSO2 Identity Server for IWA.
-
Set the hostname of WSO2 Identity Server to match its DNS entry in Active Directory. To do so, open the
deployment.tomlfound in the<IS_HOME>/repository/confdirectory and add the following configuration:[server] hostname="idp.wso2.com" -
Open the
jaas.conffile found in the<IS_HOME>/repository/conf/identityfolder and check if the configuration is as follows:Info
Learn more about Java Authentication and Authorization Service (JAAS).
Server { com.sun.security.auth.module.Krb5LoginModule required useKeyTab=false storeKey=true useTicketCache=false isInitiator=false; }; Client { com.sun.security.auth.module.Krb5LoginModule required useTicketCache=false; };
Register the IWA IdP¶
Now, let's register IWA as an authenticator in WSO2 Identity Server.
-
On the WSO2 Identity Server Console, go to Connections.
-
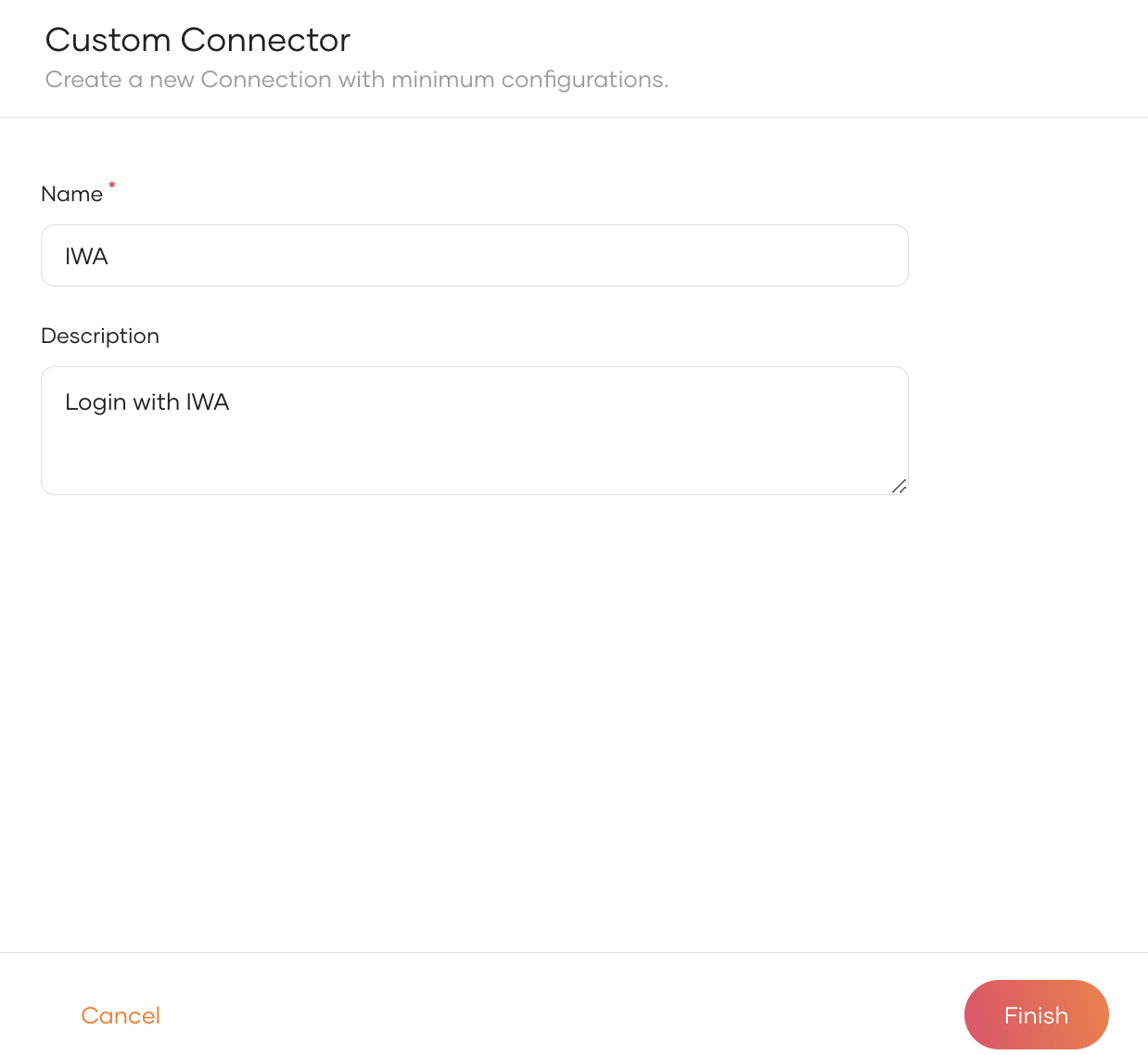
Click Create Connection and select Custom Connector.
-
Provide a name and a description for the connector and click Finish.
-
On the created custom connector, go to the Settings tab.
-
Click New Authenticator, select IWA Kerberos and click Next.
-
Enter the following details and click Finish.
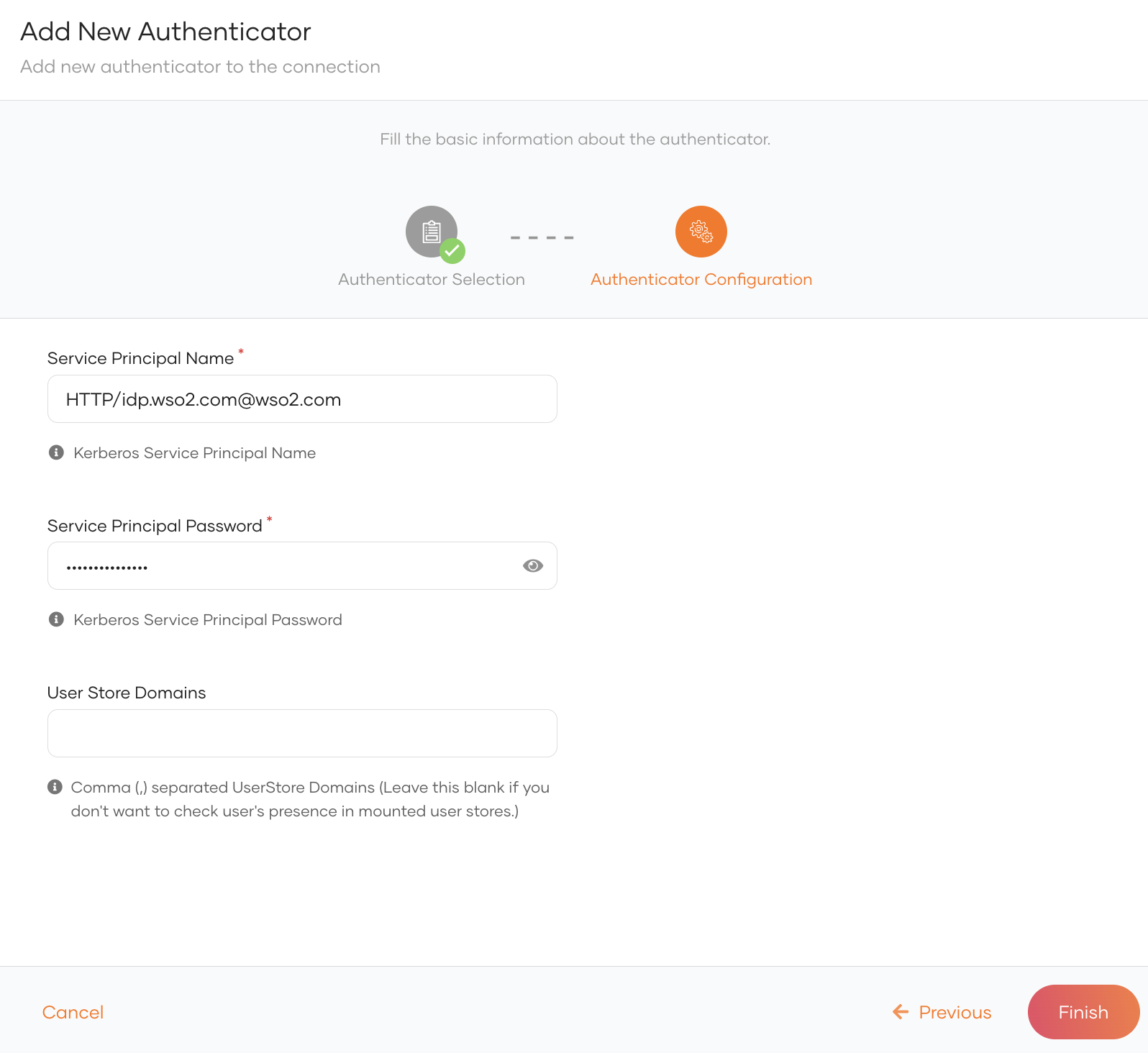
Service Principal Name The SPN registered above when setting up IWA with Active Directory in the form of <service class>/<host>@<AD domain>. e.g.HTTP/[email protected]Service Principal Password The password of the service account associated with the SPN. User Store Domains Fill only if you wish to configure IWA as a local authenticator. Leave this blank to set up IWA as a federated authenticator. Enter the name of a mounted user store (or a comma-separated list of multiple user stores) you want WSO2 Identity Server to search for the presence of the user account. e.g.
PRIMARY
Enable IWA login¶
Before you begin
You need to register an application with WSO2 Identity Server. You can register your own application or use one of the sample applications provided.
- On the WSO2 Identity Server Console, go to Applications.
-
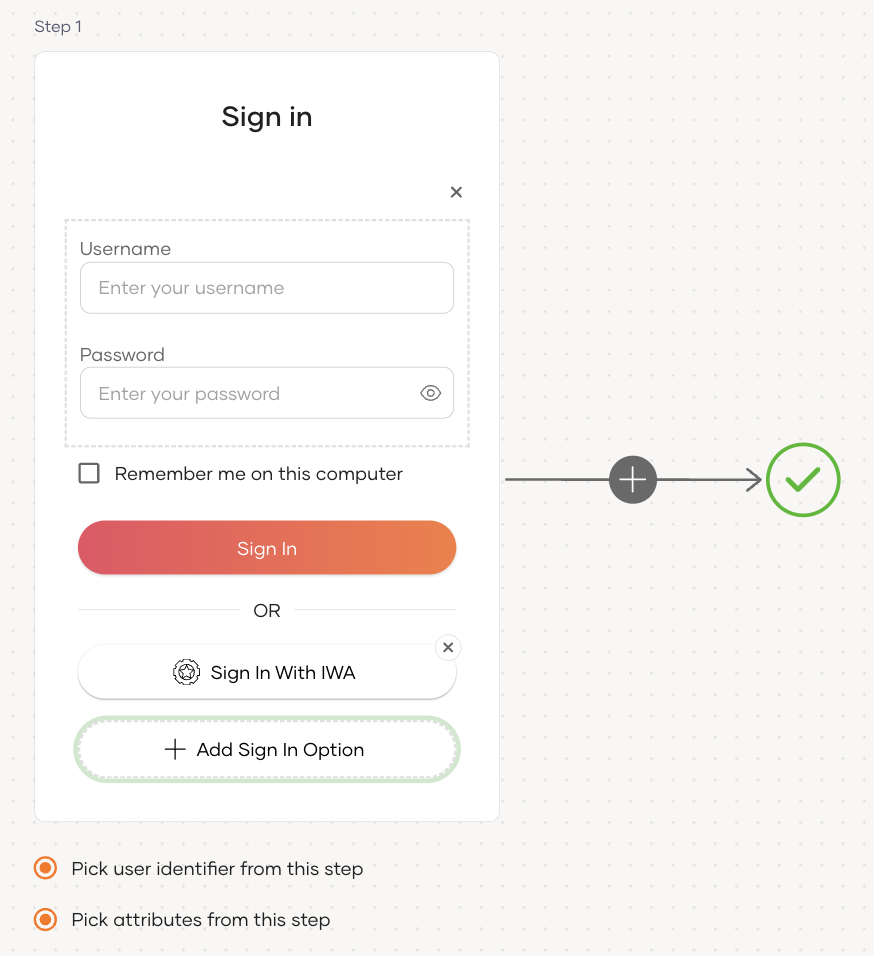
Select your application, go to the Login Flow tab and add IWA login from your preferred editor:
-
Go to Predefined Flows > Basic Flows > Add Passwordless login.
-
Select the IWA connection.
-
Click Confirm to add IWA to the sign-in flow.
Recommendations
It is recommended to add your social and enterprise connections to the first authentication step as they are used for identifying the user.
-
-
Click Update to save your changes.
Try it out¶
Configure your browser to support Kerberos and NTLM.
Before you proceed, add the relevant configurations to the browser of your choice by following the steps below.
Microsoft Edge and Chrome
-
Open the Start menu.
-
Search for Internet Options and click on it.
-
Go to its Security tab.
-
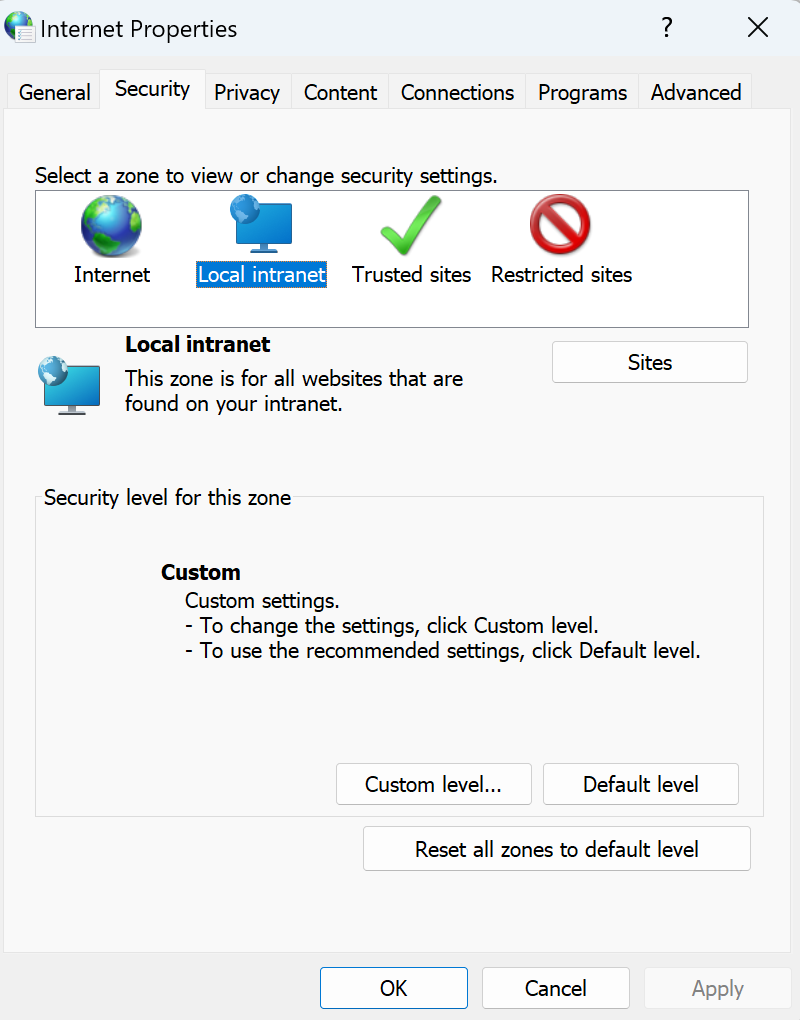
Select Local intranet and click sites.
-
On the dialog box that appears, click Advanced.
-
Enter the URL of WSO2 Identity Server and click Add.
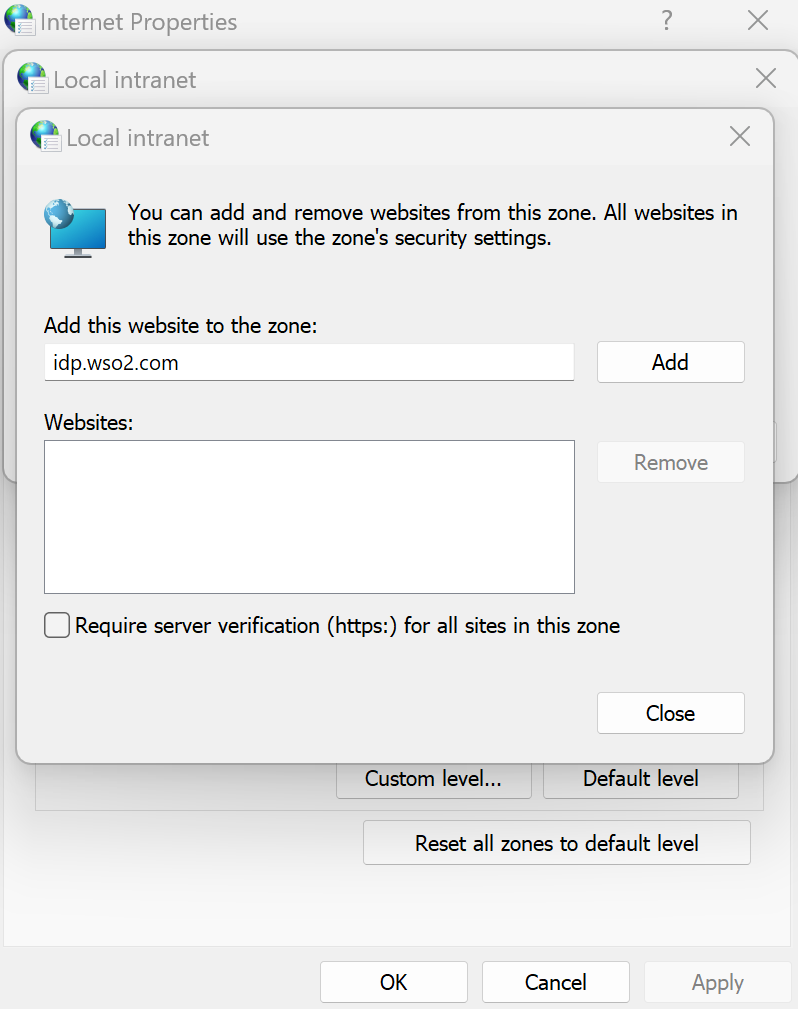
-
Click Close and click OK.
Info
Chrome inherits the above settings and no additional configurations are necessary.
Mozilla Firefox
-
On the address bar, type
about:configand press Enter. -
Ignore the warning and continue to the advanced settings of Firefox.
-
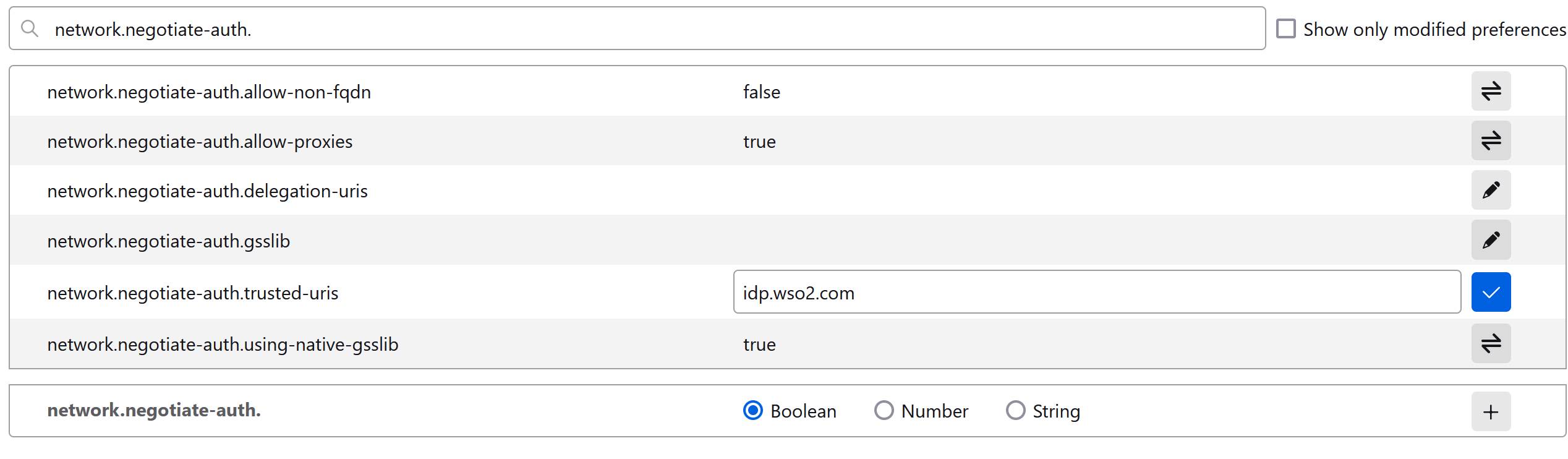
Search for
network.negotiate-auth.trusted-urisfrom the address bar and click its "Edit" icon. -
Enter the URL of WSO2 Identity Server and click the Save icon.
Follow the steps given below.
-
Access the application URL.
-
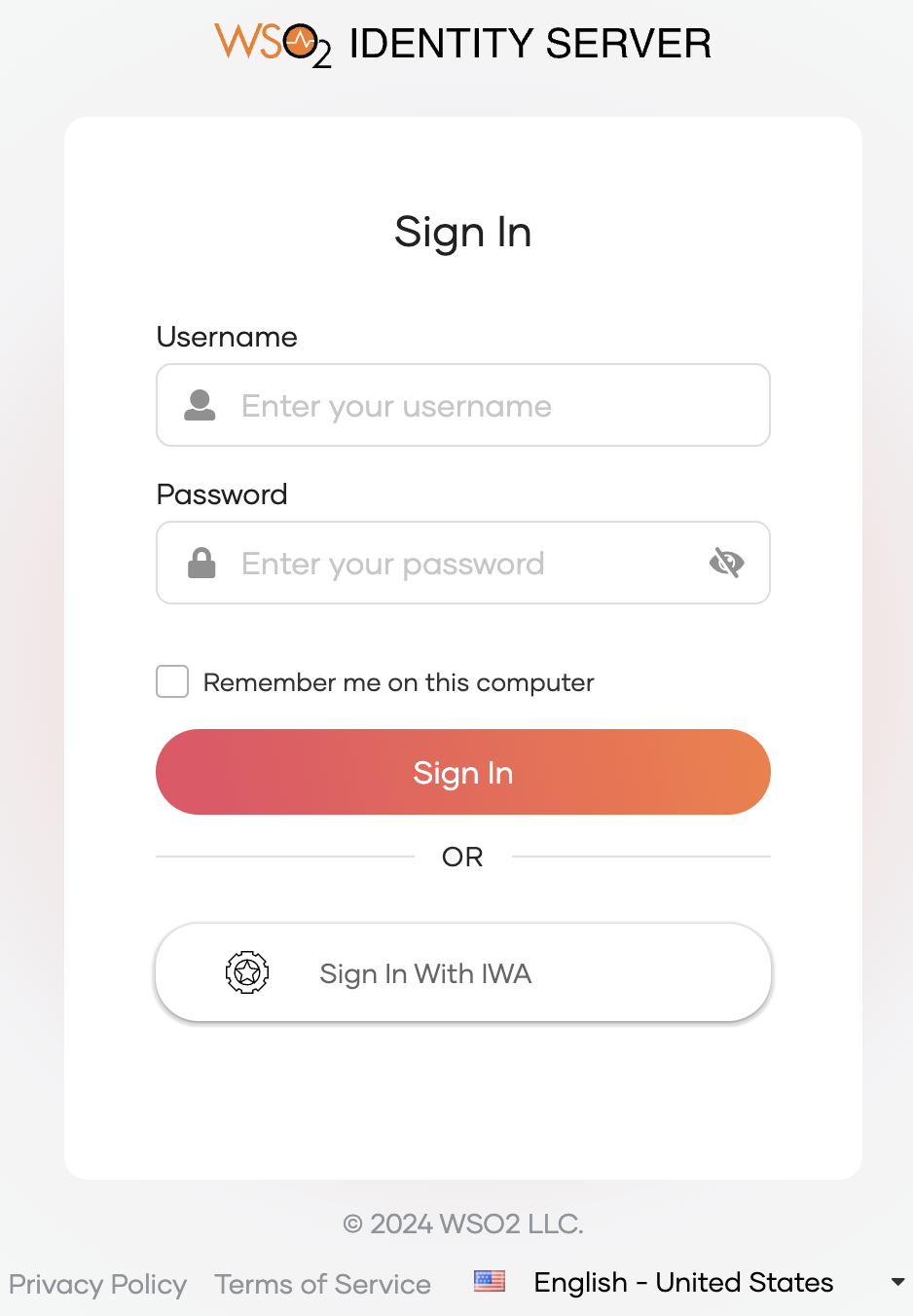
Click Login to open the WSO2 Identity Server login page.
-
On the WSO2 Identity Server login page, Sign in with IWA.
Configure user attributes¶
Configuring attributes for an Identity Provider (IdP) involves mapping the attributes available in the external IdP to local attributes. This is done so that WSO2 Identity Server can identify the user attributes in the response sent from the external IdP.
To do so,
-
On the WSO2 Identity Server Console, click Connections.
-
Select the relevant IdP connection from the list and click Set up.
-
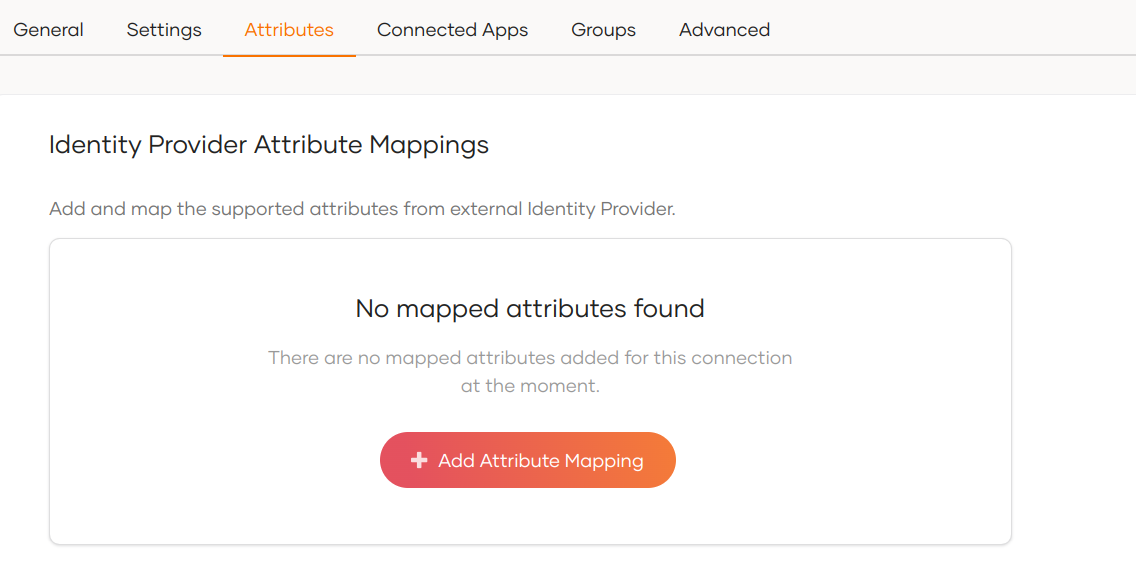
Go to the Attributes tab and under Identity Provider Attribute Mappings, click Add Attribute Mapping.
-
Enter the external attribute, select the corresponding local attribute to which it maps and click Add Attribute Mapping.
-
Click Save to save the entries.
-
Under Subject, select a Subject Attribute that will be used to uniquely identify the user.
-
Under Provisioning Attributes Selection, select the required attributes that needs to be sent in the response to provision the user in WSO2 Identity Server.
-
Click Update to save the changes.
Configure connection¶
To learn more about other configurations available for the connection, refer to the add federated login documentation.
Troubleshooting tips¶
-
Use hostnames only (no IP addresses).
-
Verify the configurations in the
jaas.conffile, particularly theisInitiator=falseproperty under theServersection (see the Set up Active Directory for IWA section). -
Make sure that your service principal (IS) is associated with only one account.
-
If you get an exception with an error message along the lines of “Checksum failed”, check whether you have given the correct password.