Add Microsoft login¶
You can add Microsoft login to your applications using WSO2 Identity Server and enable users to log in with their Microsoft accounts.
Follow this guide for instructions.
Register WSO2 Identity Server on Microsoft¶
You need to register WSO2 Identity Server as an OAuth2.0 application on Microsoft Entra ID.
Note
For detailed instructions, you can follow the Microsoft documentation.
-
Sign in to the Microsoft Entra admin center using an account with administrator permission.
Note
You must use an account in the same Microsoft 365 subscription (tenant) with which you intend to register the app.
-
Go to Identity > Applications > App registrations and select New registration.
-
Click Add and select App registration from the list.
-
Provide the required information for app registration.
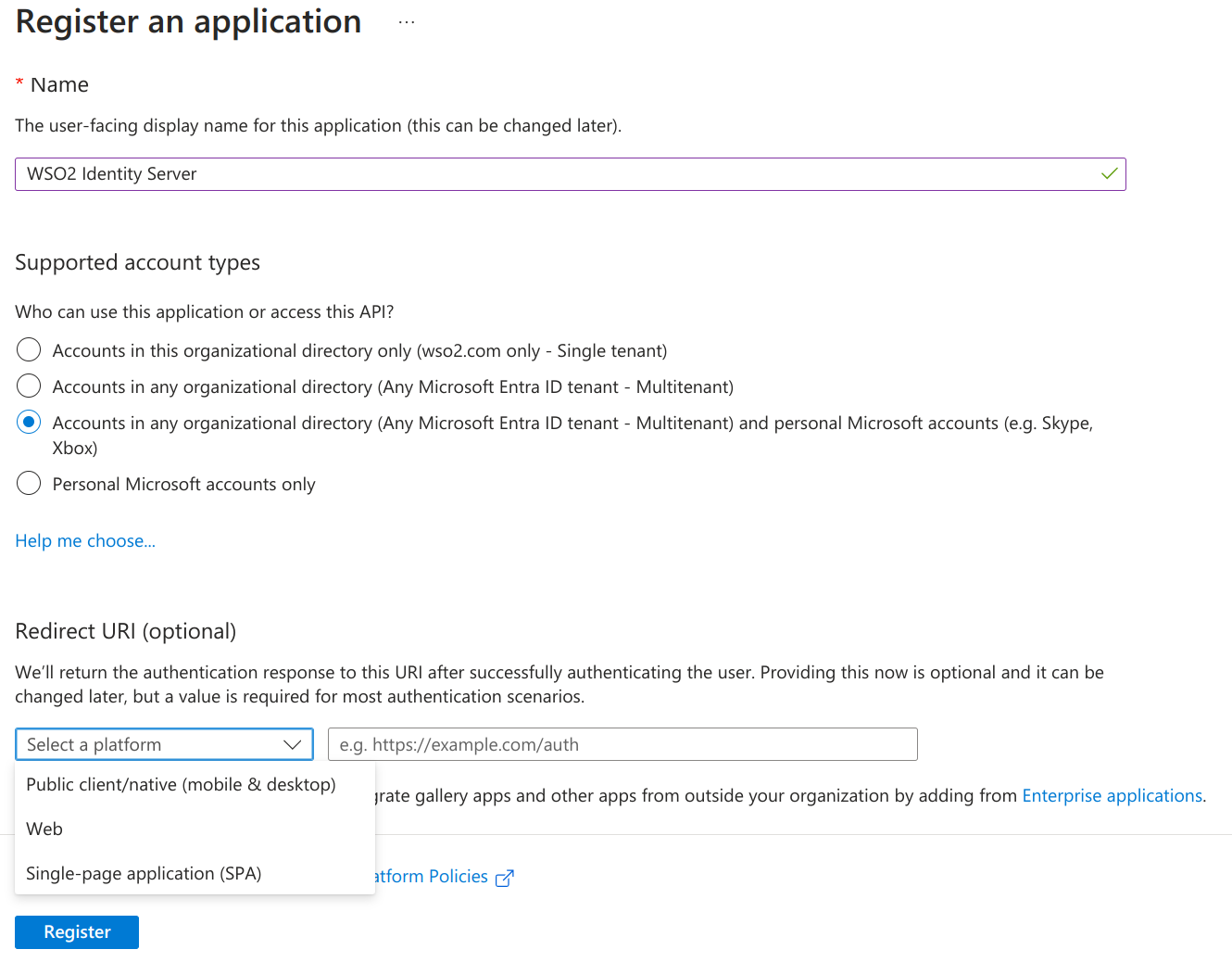
Parameter Description Name Enter a meaningful name for your application. Supported Account Type Select the supported account type.
Value:Accounts in any organizational directory (Any Microsoft Entra ID tenant - Multitenant) and personal Microsoft accounts (e.g., Skype, Xbox)Redirect URI Select Web as the platform and provide the URL to redirect after the login is completed.
Value:https://localhost:9443/commonauth -
Click Register to create the application.
Note
Take note of the client ID after the application is created.
Now, let's generate a client secret for the application.
- Go to Certificates & secrets on the left navigation and click + New client secret.
- Enter a description for the client secret and select the expiry time.
-
Click Add to add the client secret.
Important
Take note of the generated Value. Microsoft Entra will allow copying this value only once. This value is the newly generated client secret for your Microsoft connection in WSO2 Identity Server.
Register the Microsoft IdP¶
Now, let's register the Microsoft IdP in WSO2 Identity Server.
- On the WSO2 Identity Server Console, go to Connections.
- Click New Connections and select Microsoft.
-
Enter the following details of the Microsoft identity provider and click Finish:
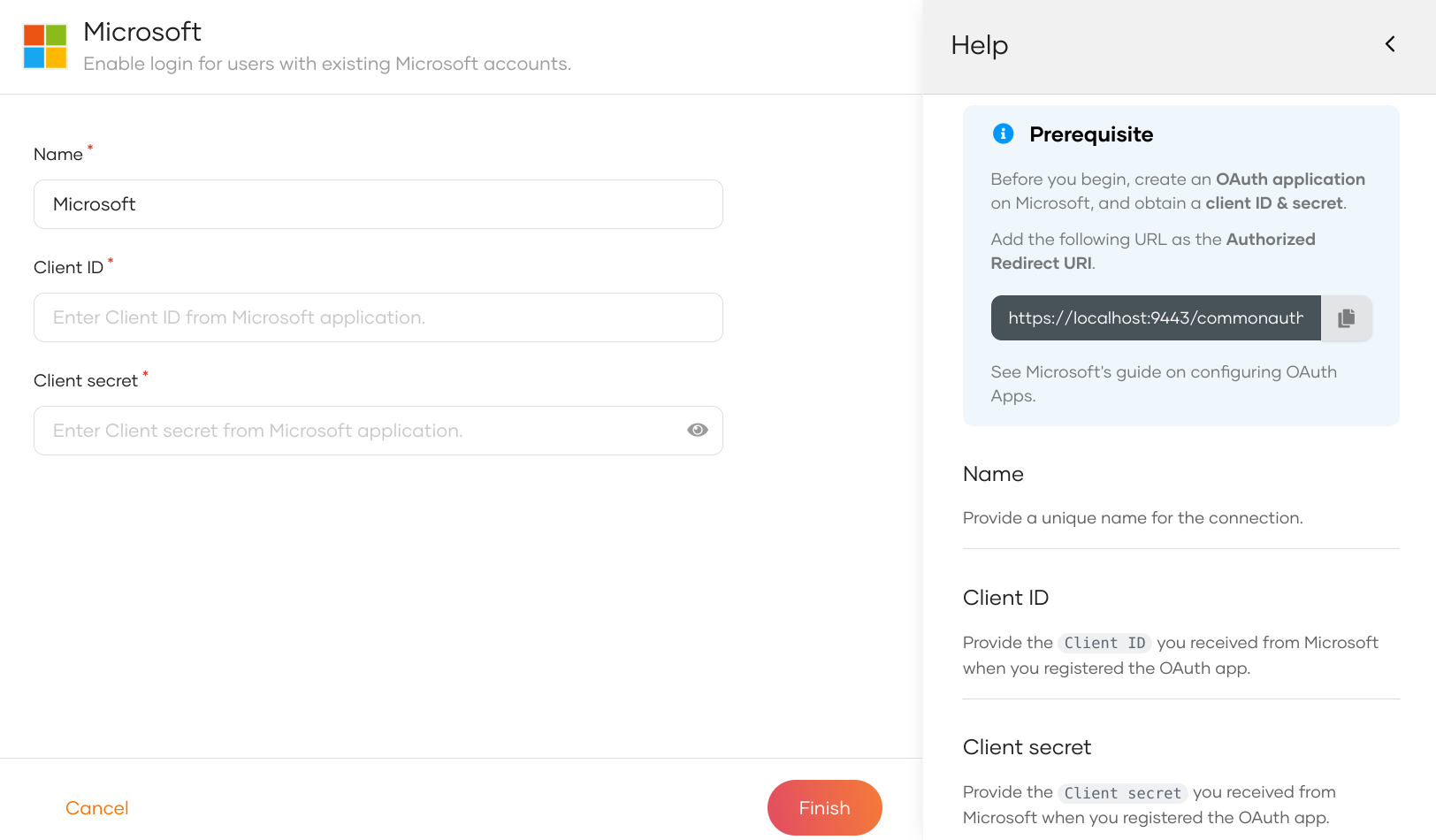
Parameter Description Name A unique name for this Microsoft identity provider. Client ID The client ID obtained from Microsoft. Client secret The client secret obtained from Microsoft.
When a user logs in with an external identity provider using the same email address registered in a local account, JIT-provisioning overrides the attributes of the local account with the attributes received from the external identity provider.
WSO2 Identity Server, by default, disables Just-In-Time (JIT) user provisioning for your external identity provider.
To enable JIT-provisioning,
-
On the WSO2 Identity Server Console, click Connections and select the relevant connection.
-
Go to the Just-in-Time Provisioning tab of the selected connection.
-
Check/Uncheck the Just-in-Time (JIT) User Provisioning checkbox to enable/disable it.
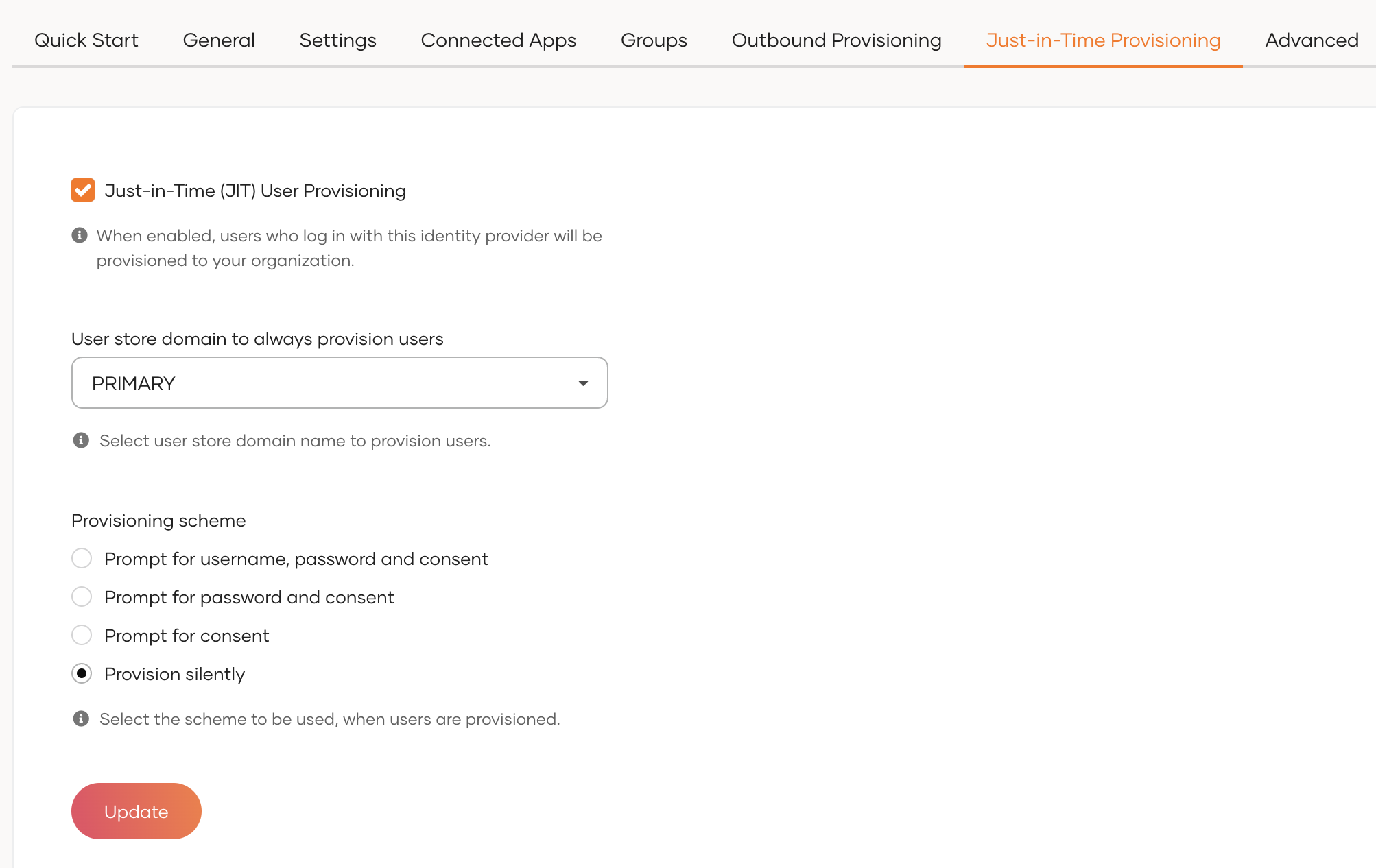
-
Click Update to save the changes.
Note
-
Learn more about JIT provisioning configurations in configure JIT user provisioning.
-
You can use the identity provider APIs to customize the attribute syncing behavior between the external identity provider and WSO2 Identity Server.
After the Microsoft identity provider is created, go to the Settings tab and see the list of scopes to which Microsoft has granted permissions.
- email: Allows to view the user's email address.
- openid: Allows authentication using OpenID Connect and to obtain the ID token.
- profile: Allows to view the user's basic profile data.
Note
WSO2 Identity Server needs these scopes to get user information. WSO2 Identity Server checks the attribute configurations of the application and sends the relevant attributes received from Microsoft to the app. You can read the Microsoft documentation to learn more.
Enable Microsoft login¶
Before you begin
You need to register an application with WSO2 Identity Server. You can register your own application or use one of the sample applications provided.
To enable Microsoft login:
- On the WSO2 Identity Server Console, go to Applications.
-
Select your application, go to the Login Flow tab and add Microsoft login from your preferred editor:
-
Click Add Sign In Option to add a new authenticator to the first step.
-
Select the Microsoft connection.
-
Click Confirm to add login with Microsoft to the sign-in flow.
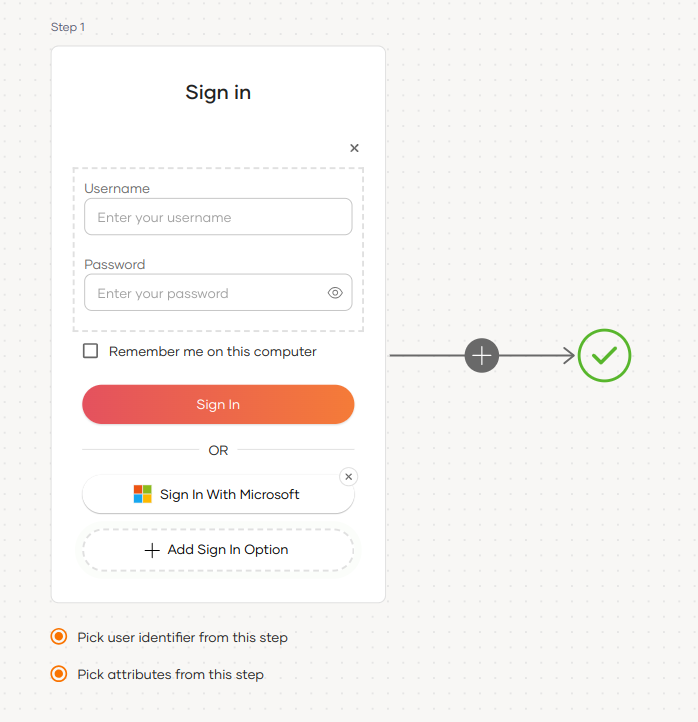
Recommendations
It is recommended to add your social and enterprise connections to the first authentication step as they are used for identifying the user.
-
-
Click Update to save your changes.
Try it out¶
Follow the steps given below.
- Access the application URL.
- Click Login to open the WSO2 Identity Server login page.
-
On the WSO2 Identity Server login page, Sign in with Microsoft.
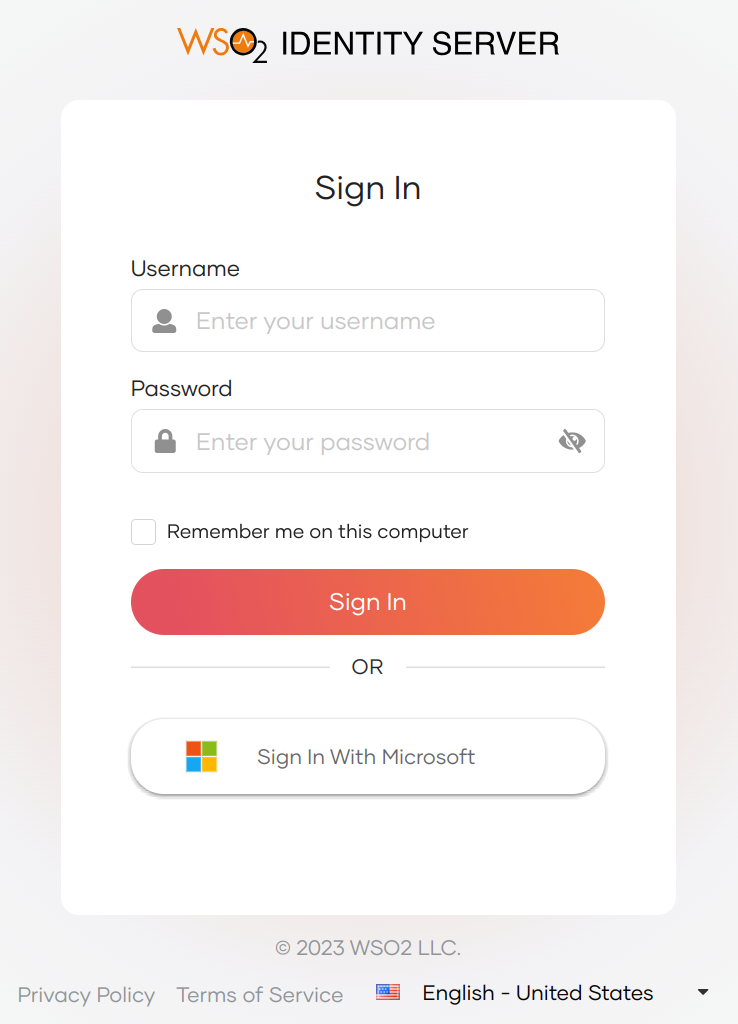
-
Log in to Microsoft with an existing user account.
Note
When a user successfully logs in with Microsoft for the first time, a user account is created in the WSO2 Identity Server Console with the Microsoft username. Microsoft will manage this new user account.
Configure connection¶
To learn more about other configurations available for the connection, refer to the add federated login documentation.