Self registration¶
Enable users to self-register and create their own accounts within the organization on WSO2 Identity Server.
Configuration instructions¶
To set up self-registration, follow these steps:
- On the WSO2 Identity Server Console, go to Login & Registration > User Onboarding > Self Registration.
- Toggle the switch to enable self-registration.
- Configure the additional settings such as account verification, auto-login, and notification emails as needed.
- Click Update to save the changes.
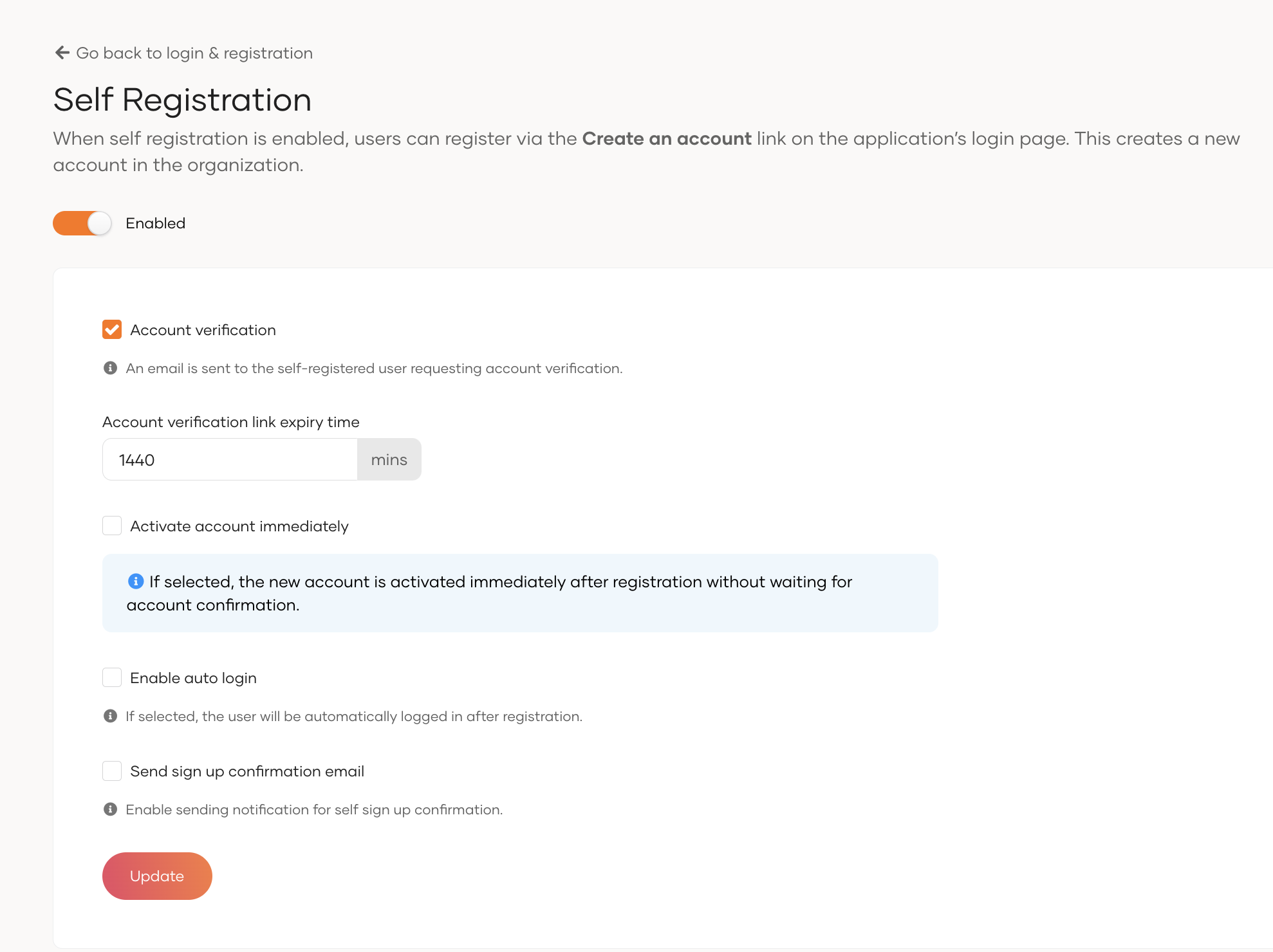
Parameters¶
| Parameter | Description |
|---|---|
Account Verification |
When enabled, requires users to verify their accounts as part of registration. |
Account verification link expiry time |
Time in minutes until the account verification link expires. |
Activate account immediately |
If selected, the new account is activated immediately after registration without waiting for account confirmation. |
Enable auto login |
If selected, the user will be automatically logged in after registration. |
Send sign up confirmation email |
A confirmation email is sent upon successful self-registration if this option is enabled. |