Configure Just-in-Time user provisioning¶
This guide explains the concept of Just-In-Time (JIT) user provisioning, why and when to use it, and also the instructions for configuring it.
How JIT provisioning works¶
Just-in-Time (JIT) user provisioning is a method used to store a user's identity and user attributes in the WSO2 Identity Server user store when the user logs in with an external identity provider (IdP)
The flow of JIT user provisioning is as follows:
-
When an application initiates an authentication request, the user gets redirected to WSO2 Identity Server.
-
If the user selects an external IdP for authentication, WSO2 Identity Server redirects the user to the relevant IdP.
-
If WSO2 Identity Server receives a positive authentication response from the external IdP, JIT provisioning is triggered.
-
WSO2 Identity Server creates a user account in its internal user store along with the user attributes obtained from the authentication response.
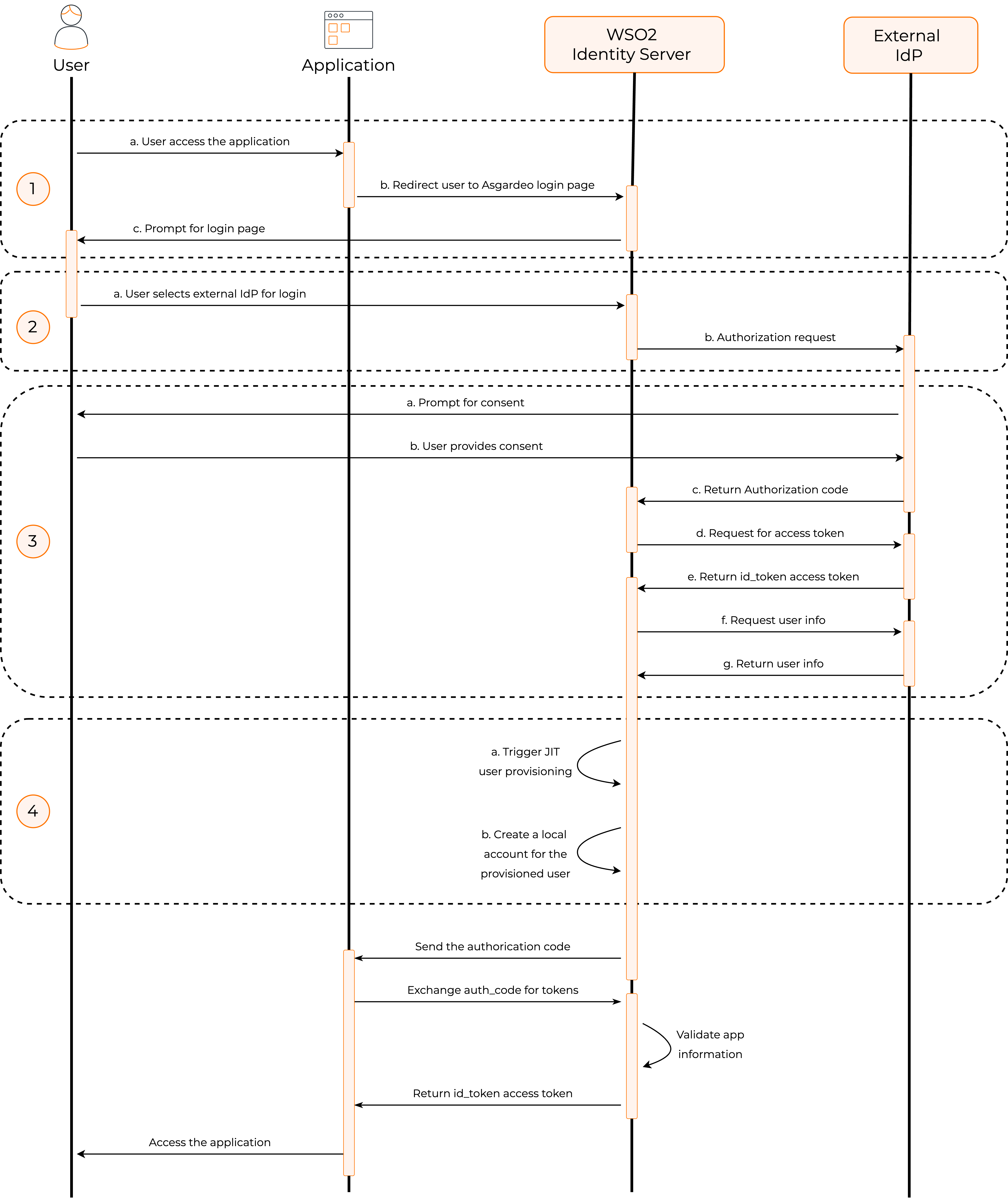
With this process, new user accounts are automatically provisioned to WSO2 Identity Server when users log in with external IdPs.
Enable/Disable JIT user provisioning¶
Prerequisite
Register the external IdP as a connection in WSO2 Identity Server.
To enable/disable JIT user provisioning for an external Identity provider:
-
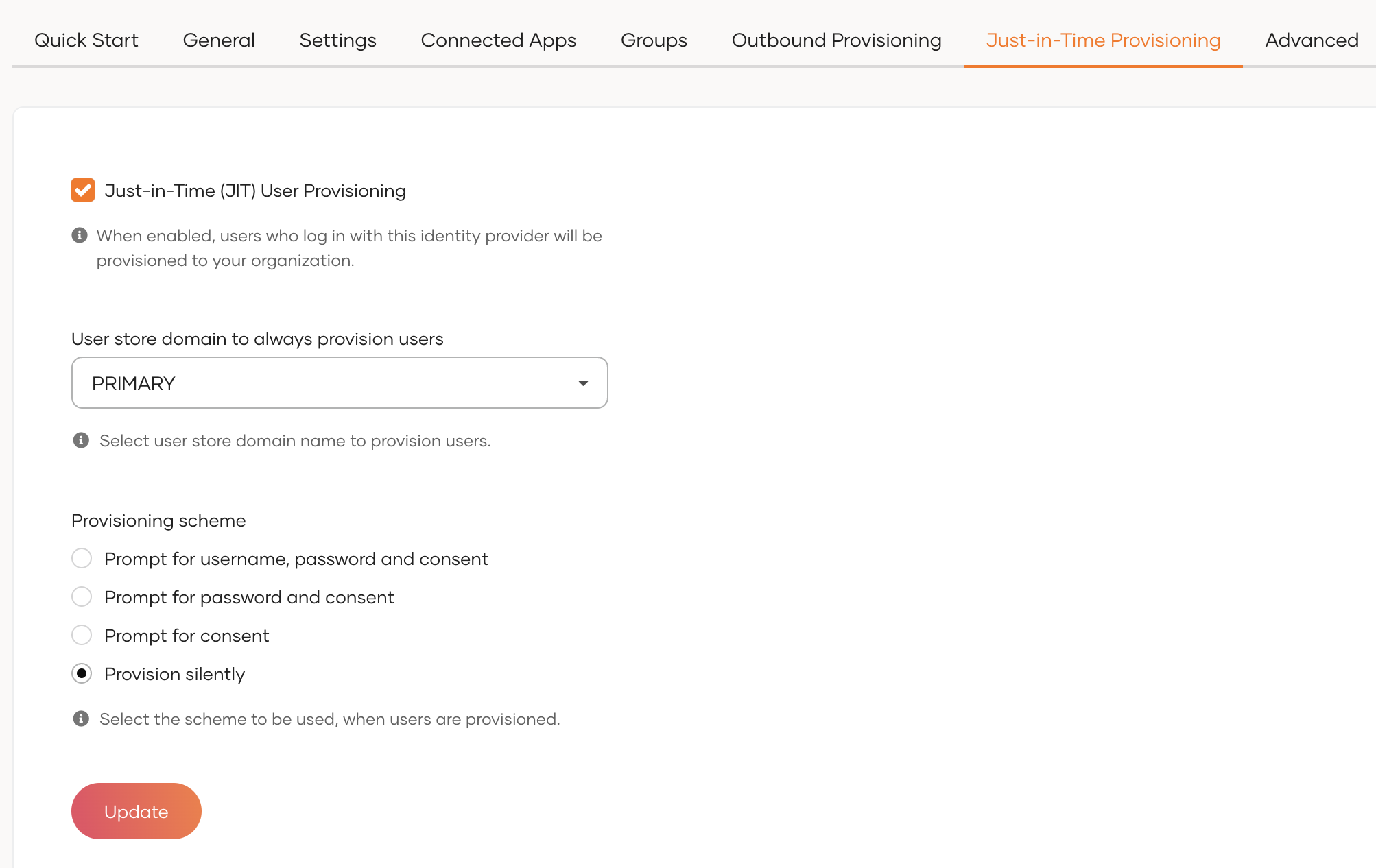
On the WSO2 Identity Server Console, click Connections and select the relevant connection.
-
Go to the Just-in-Time Provisioning tab of the selected connection.
-
Check/Uncheck the Just-in-Time (JIT) User Provisioning checkbox to enable/disable it.
-
Click Update to save.
Note
- When JIT is enabled, WSO2 Identity Server updates the existing local account created with the same email address or if a new user, creates a user profile with the user attributes received from the external IdP.
- When JIT is disabled, a user profile is not created. Therefore, there is no location to store the attributes of the user. In such cases, the attributes are directly passed to the application.
Warning
If you have configured multi-factor authentication (MFA), disabling JIT user provisioning might break the application login flow. Learn more about troubleshooting sign-in flow errors with JIT.
Troubleshoot sign-in flow errors¶
If you have disabled JIT provisioning for an IdP, applications that use multi-factor authentication may break as certain MFA mechanisms (such as TOTP and Email OTP) require users to have local accounts in WSO2 Identity Server.
When configuring an application's sign-in flow involving JIT-disabled IdPs and such MFA options, WSO2 Identity Server displays the following warning:
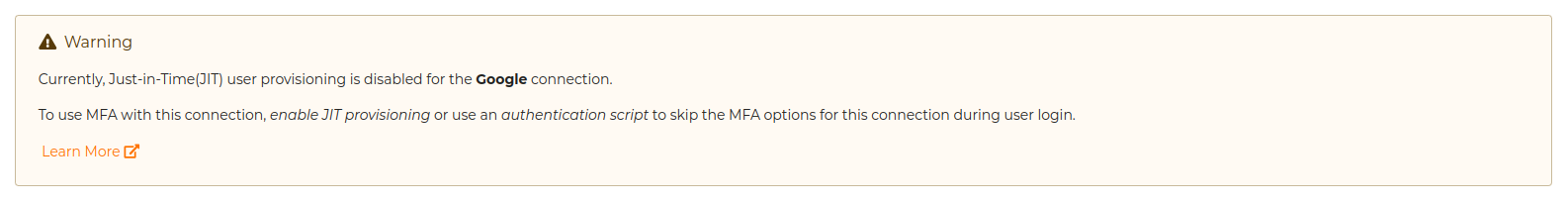
To avoid unexpected errors, you can use the following conditional authentication script to skip the MFA step when using JIT-disabled connectors.
var localAuthenticator = 'LOCAL';
var onLoginRequest = function (context) {
executeStep(1, {
onSuccess: function (context) {
var step = context.steps[1];
if (step.idp == localAuthenticator) {
executeStep(2); // MFA Step
}
}
});
};
Note
For more information on this script, refer to the sign-in option-based conditional authentication script.