Add MFA based on login attempts¶
You can enable a more secure login flow for users based on the number of invalid login attempts by applying the Login-Attempt-Based conditional authentication template for Adaptive MFA. This template enables two-factor authentication with TOTP for users who exceed the number of invalid login attempts you specify.
Scenario¶
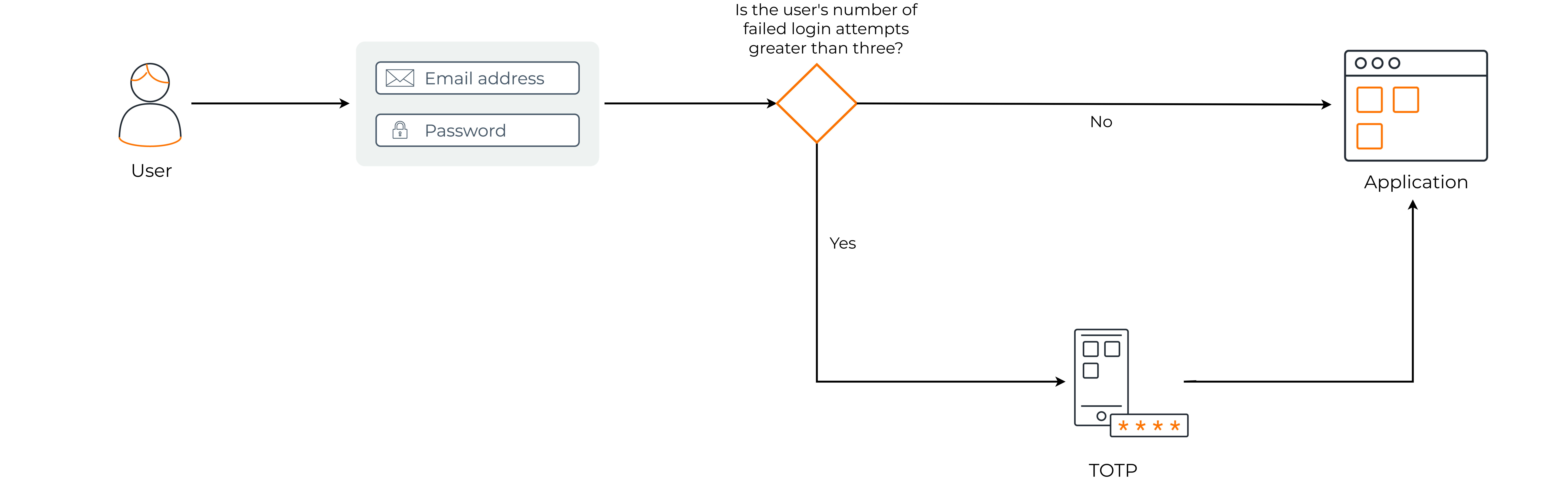
Consider a scenario where the login flow of the application is stepped up with TOTP if a user exceeds three failed login attempts. The authentication steps are as follows:
- Username and password
- TOTP
Prerequisites¶
You need to register an application with WSO2 Identity Server. You can register your own application or use one of the sample applications provided.
Configure the login flow¶
To enable conditional authentication:
-
On the WSO2 Identity Server Console, click Applications.
-
Select the relevant application and go to its Login Flow tab.
-
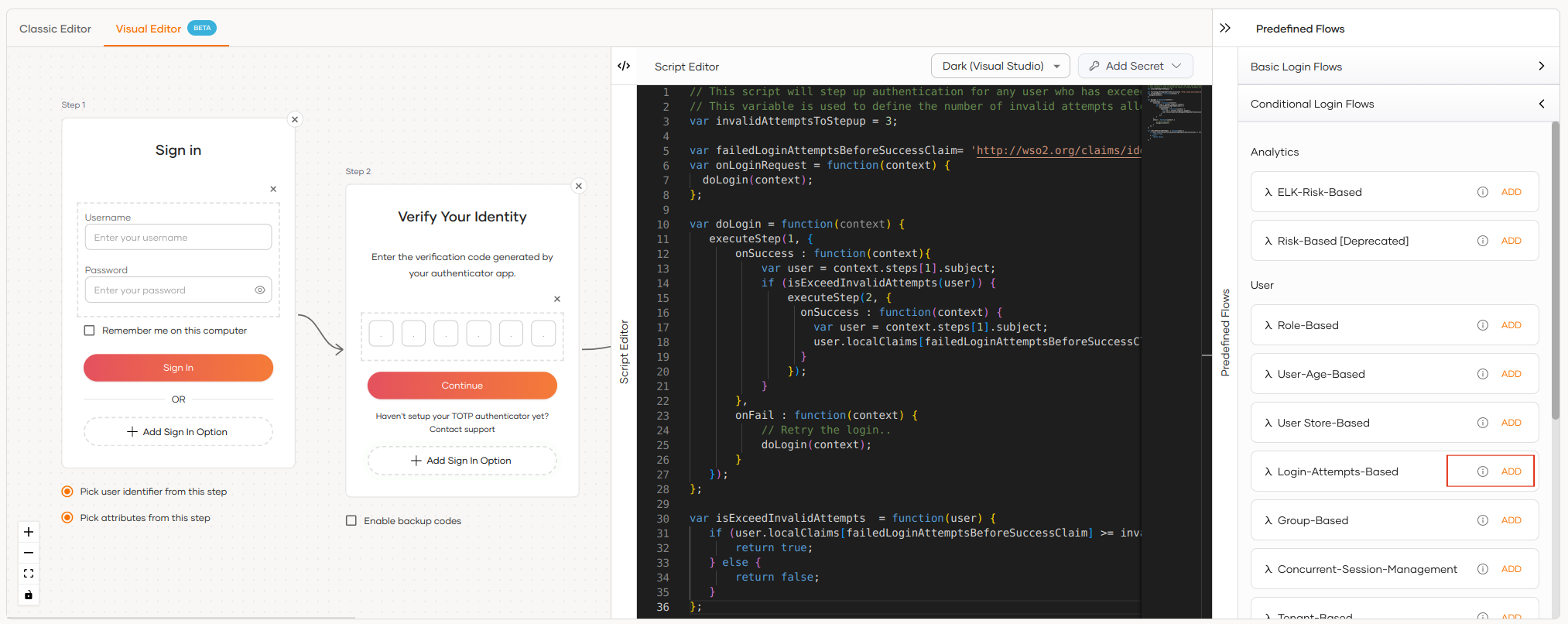
Add login attempt based adaptive MFA as follows:
-
Go to Predefined Flows > Conditional Login Flows.
-
Click Adaptive MFA > Login-Attempts-Based > ADD to add the role-based adaptive MFA script.
-
Click Confirm to replace any existing script with the selected predefined script.
-
-
Verify that the login flow is now updated with the following two authentication steps:
- Step 1: Username and Password
- Step 2: TOTP
-
Update the following parameter in the script.
Parameter Description invalidAttemptsToStepupMinimum number of attempts made by a user to prompt 2FA. For this example scenario, enter
3. -
Click Update to confirm.
How it works¶
Shown below is the script of the login-attempt-based conditional authentication template.
// This script will step up authentication for any user who has exceeded 3 invalid login attempts continuously.
// This variable is used to define the number of invalid attempts allowed before prompting the second facto.
var invalidAttemptsToStepup = 3;
var failedLoginAttemptsBeforeSuccessClaim= 'http://wso2.org/claims/identity/failedLoginAttemptsBeforeSuccess';
var onLoginRequest = function(context) {
doLogin(context);
};
var doLogin = function(context) {
executeStep(1, {
onSuccess : function(context){
var user = context.steps[1].subject;
if (isExceedInvalidAttempts(user)) {
executeStep(2, {
onSuccess : function(context) {
var user = context.steps[1].subject;
user.localClaims[failedLoginAttemptsBeforeSuccessClaim] = "0";
}
});
}
},
onFail : function(context) {
// Retry the login..
doLogin(context);
}
});
};
var isExceedInvalidAttempts = function(user) {
if (user.localClaims[failedLoginAttemptsBeforeSuccessClaim] >= invalidAttemptsToStepup) {
return true;
} else {
return false;
}
};
Let's look at how this script works.
Note
Find out more about the scripting language in the Conditional Authentication API Reference.
Try it out¶
Follow the steps given below.
- Access the application URL.
- Try to log in, but use invalid credentials.
- Repeat step 2 for two more attempts making three failed login attempts.
-
Try to log in to the application using valid credentials.
The user will be prompted to enter the TOTP received on their registered TOTP authenticator.