Authentication¶
See the topics given below to manage authentication for your applications.
Design the login flow¶
When you register an application, you can customize the login flow.
-
Configure WSO2 Identity Server login for single-page applications with OIDC or web applications with OIDC or SAML.
-
Add social login options such as Google, Facebook, Apple, and Microsoft.
-
Add other enterprise identity providers as login options.
-
Configure the number of factors (2FA or MFA) in the login flow to enforce multi-factor authentication.
-
Enforce conditional authentication to dynamically change the login flow of a user based on the user's devices, networks, locations, or usage contexts.
Manage user attributes¶
Manage the user attributes you want to share with your application:
Manage connections¶
You can define connections to external identity providers (IdPs) and use them to authenticate users who log in to your applications. This process of authenticating users with external IdPs is known as identity federation.
Note
The external identity provider (IdP) authenticates users and issues the identification information by using security tokens like SAML 2.0, OpenID Connect, OAuth 2.0, and WS-Trust.
Benefits of identity federation¶
There are several benefits of using identity federation:
-
Allows users to sign in with a user account registered with a trusted IdP without having to manually create accounts for them in WSO2 Identity Server.
Note
If the IdP is configured to use JIT user provisioning, signing in with an external IdP will automatically create a local account for the user in WSO2 Identity Server.
-
Give users the convenience of choosing their existing, trusted IdP when they sign in or sign up to your organization in WSO2 Identity Server.
Supported external IdPs¶
WSO2 Identity Server supports a variety of external identity providers with various open-standard protocols (such as OAuth2.0, OpenID Connect, and SAML).
You can configure any number of external connections for your application via WSO2 Identity Server.
Map groups with WSO2 Identity Server¶
Configure External Connection's Group attribute¶
To add groups to a connection on WSO2 Identity Server:
-
On the WSO2 Identity Server Console, go to Connections.
-
Select your connection and go to its Attributes tab.
-
Click Add Attribute Mapping to add a new attribute mapping.
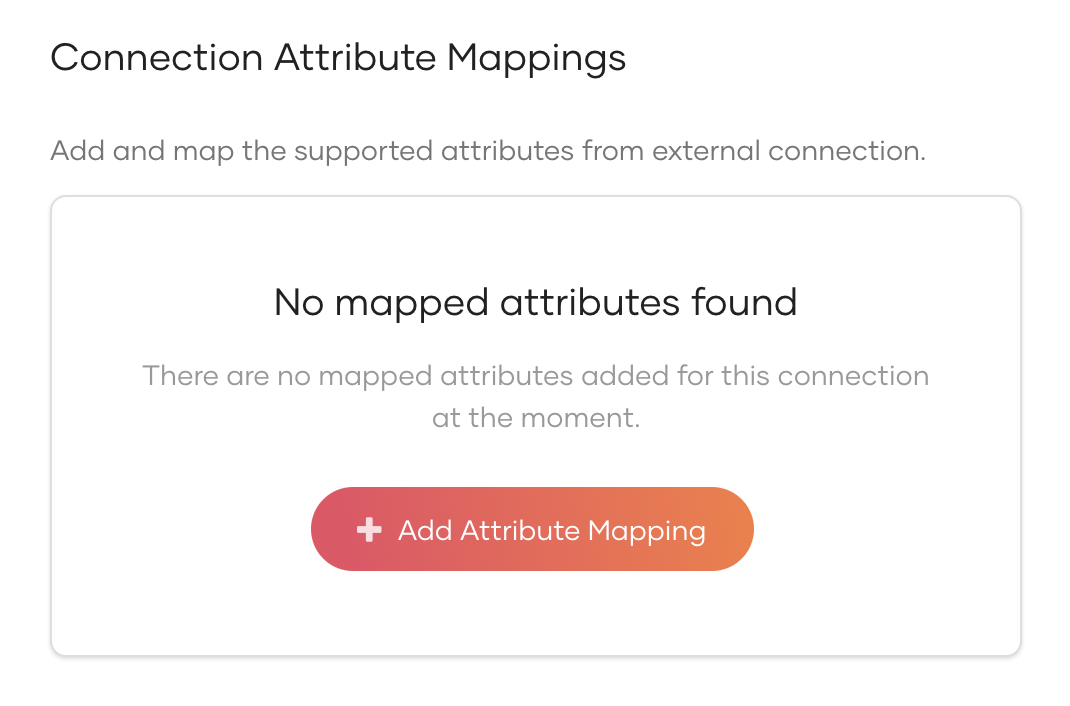
-
Enter the External IdP Attribute of the connection and map it to the Groups attribute of Asgardeo.
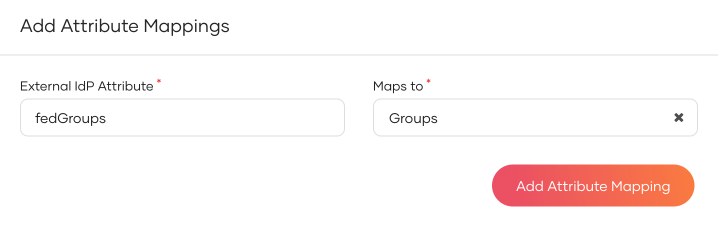
-
Click Add Attribute Mapping and then click Save.
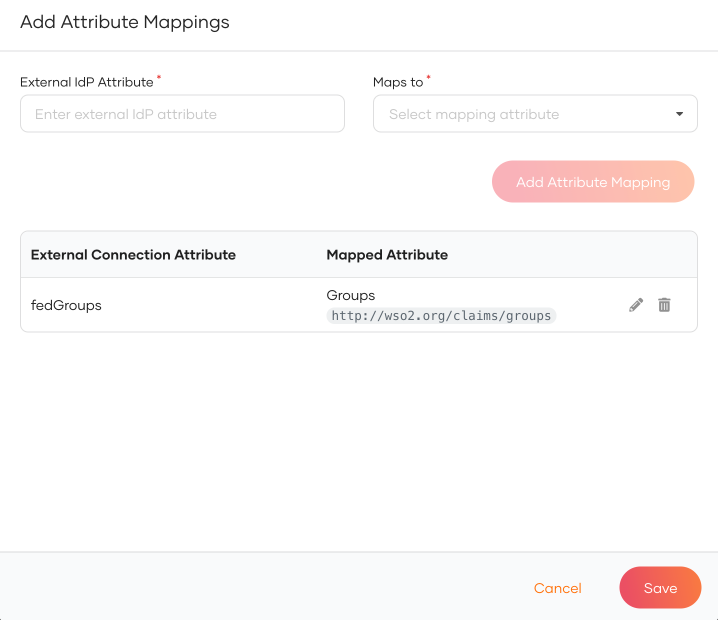
-
Click Update to save the changes.
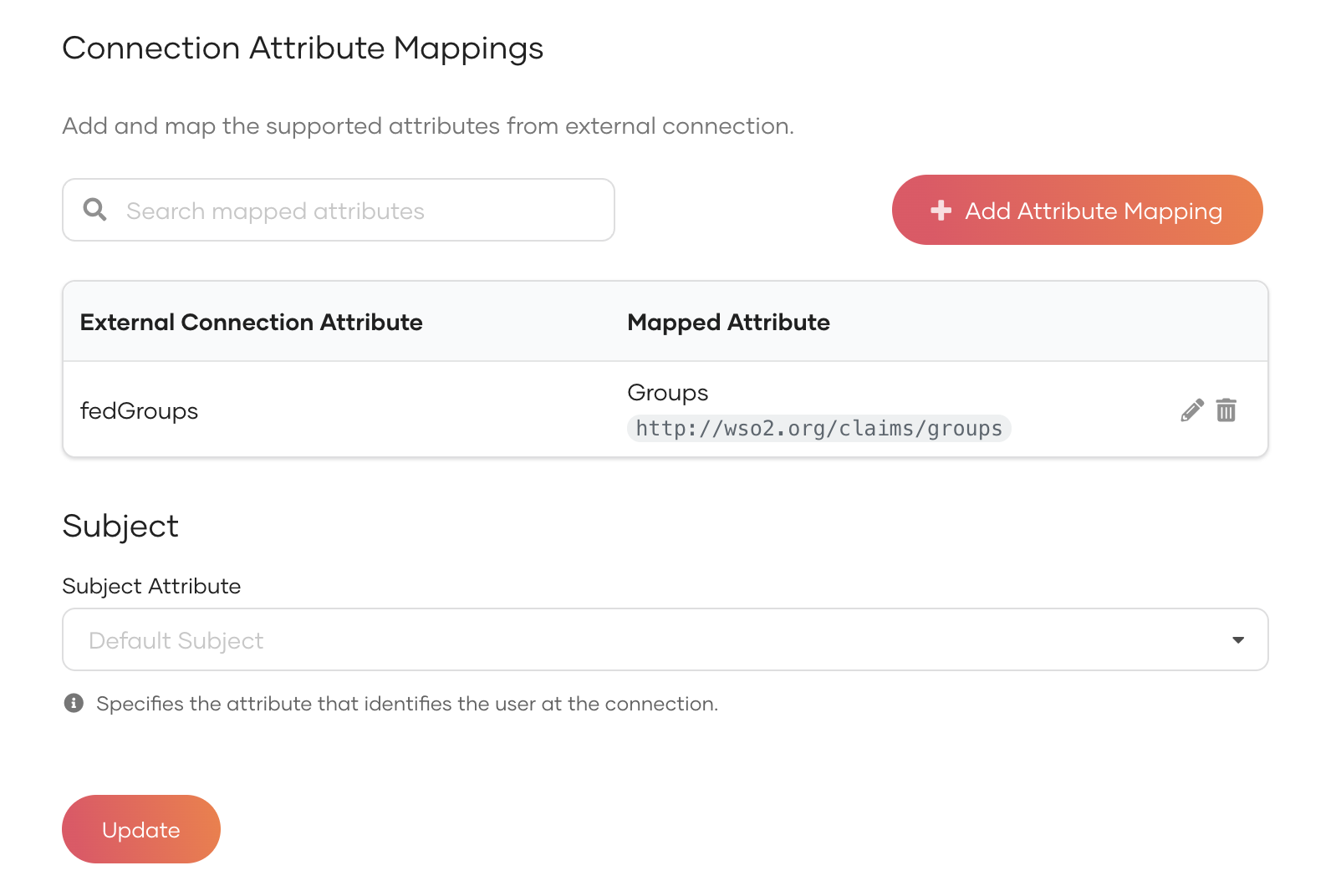
Add groups to connections¶
Follow the steps below to add the groups from your connection to Asgardeo:
- On the Asgardeo Console, go to Connections.
- Select your connection and go to its Groups tab.
-
Click New Group and enter the group name. Be sure to enter the exact group name that will be returned from the connection.
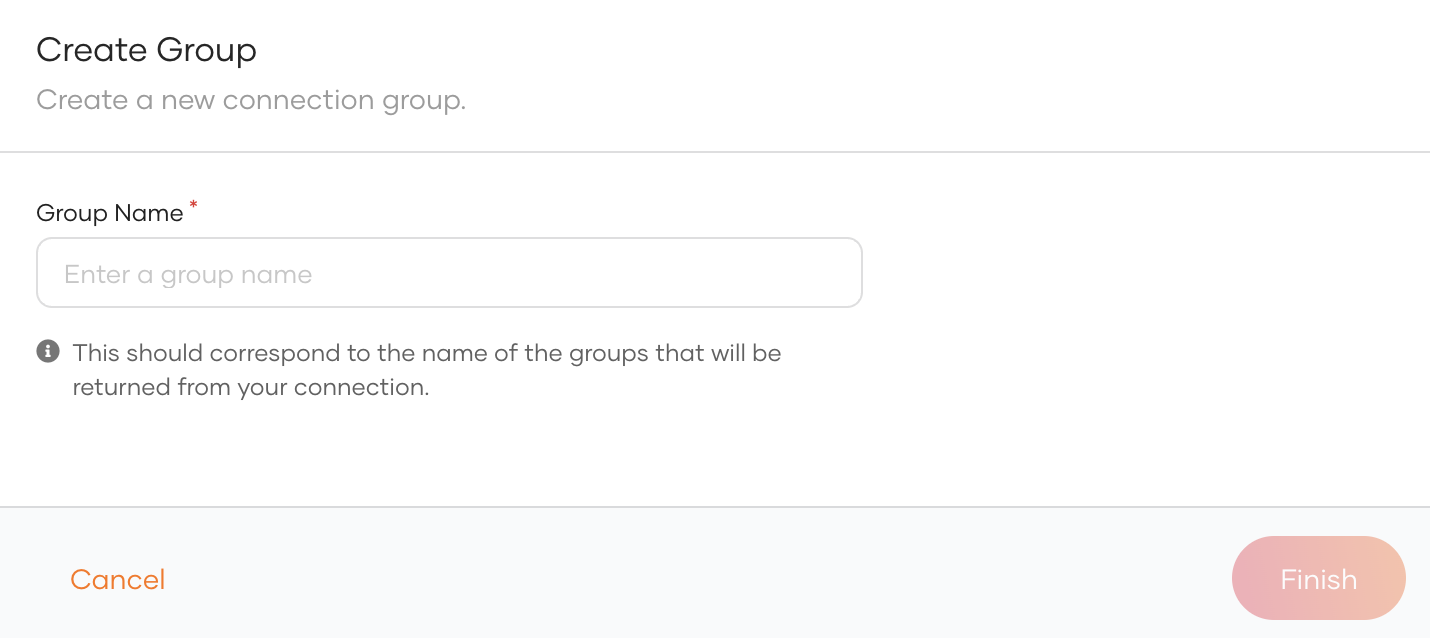
-
Click Finish to add the group information.