Configuring a Service Provider for Adaptive Authentication¶
Adaptive authentication enables an identity provider to prompt multi-factor authentication steps based on a user's risk profile or user behavior, i.e., the authentication adapts to the situation or the user during the authentication process.
Example
For instance, high-risk logins such as a user attempting to log in from an unusual location causes the adaptive authentication mechanism to prompt an extra authentication in order to increase security.
For more information on adaptive authentication with WSO2 IS, see Adaptive Authentication.
This tutorial guides you through setting up a sample application to try out adaptive authentication and configuring it as a service provider in WSO2 IS.
Step 01: Set Up the Samples¶
Follow the steps below to set up the sample application to try out adaptive authentication using a sample application.
-
PickUp sample web application (SAML).
-
Deploy and configure
saml2-web-app-pickup-dispatchsample application. -
Access the PickUp application URL at http://localhost:8080/saml2-web-app-pickup-dispatch.com.
Note that a login screen appears.
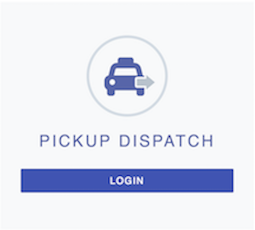
-
-
Deploy the sample authenticator dependency and web application in WSO2 IS.
-
Download the org.wso2.carbon.identity.sample.extension.authenticators-5.9.0.jar file and paste it inside the
<IS_HOME>/repository/components/dropinsdirectory.Note
The
org.wso2.carbon.identity.sample.extension.authenticators-5.9.0.jarcontains implementation of the sample authenticators (Demo HardwareKey authenticator, Demo Fingerprint authenticator, Demo FaceID authenticator) used in this tutorial. -
Download the sample-auth.war file and paste it inside the
<IS_HOME>/repository/deployment/server/webappsfolder.Note
This
sample-auth.warfile contains the WEB UI for the sample authenticators used in this tutorial. -
Start the WSO2 IS server and test whether all the samples are configured successfully.
-
Sign in to the WSO2 IS Management Console with one of the following URLs using
adminas the username and password.For HTTP --> http://<HTTP_HOST>:9776/carbon For HTTPS --> https://<HTTPS_HOST>:9443/carbon -
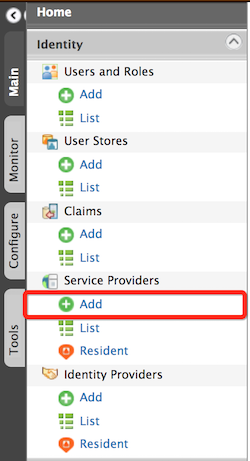
On the Main tab, click Service Providers > Add .
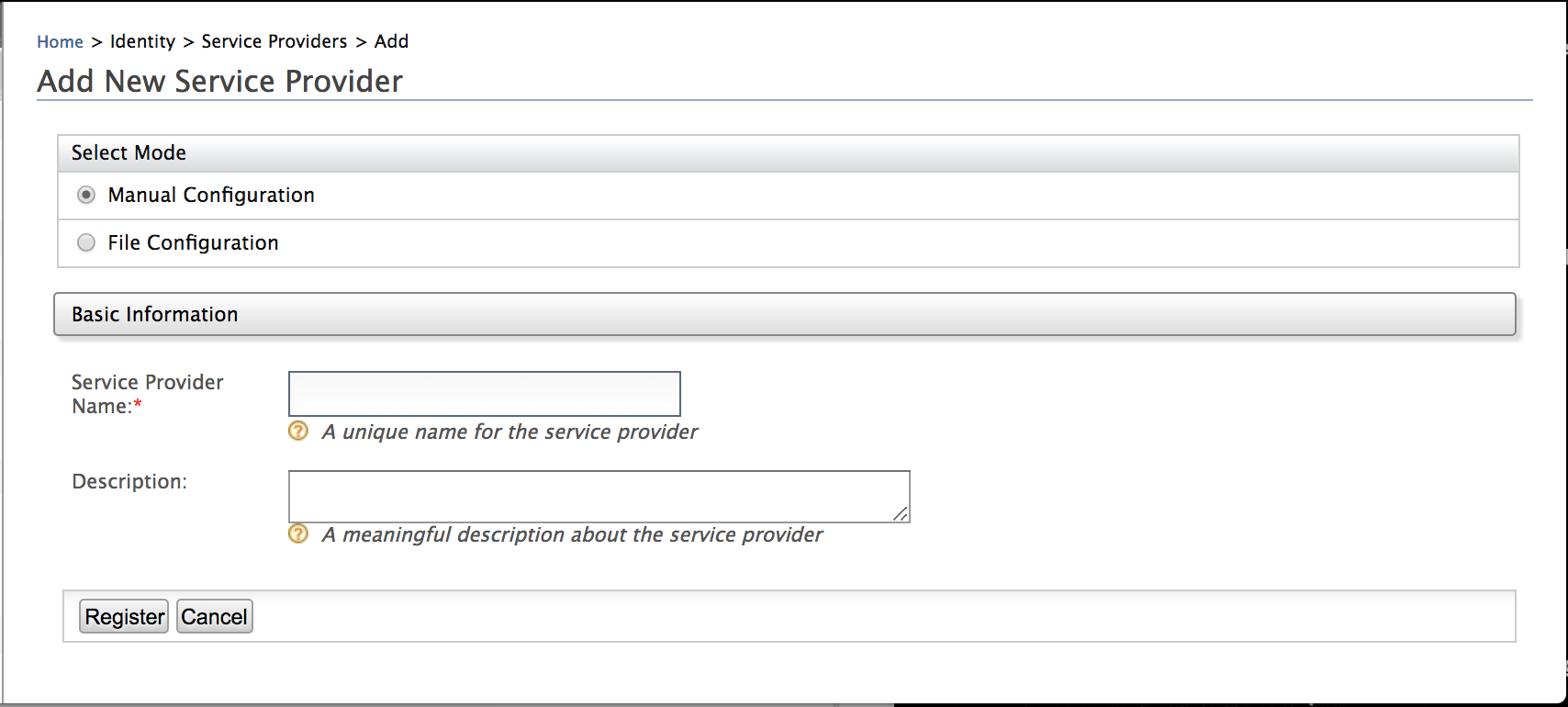
- Enter
testas the Service Provider Name and click Register.
-
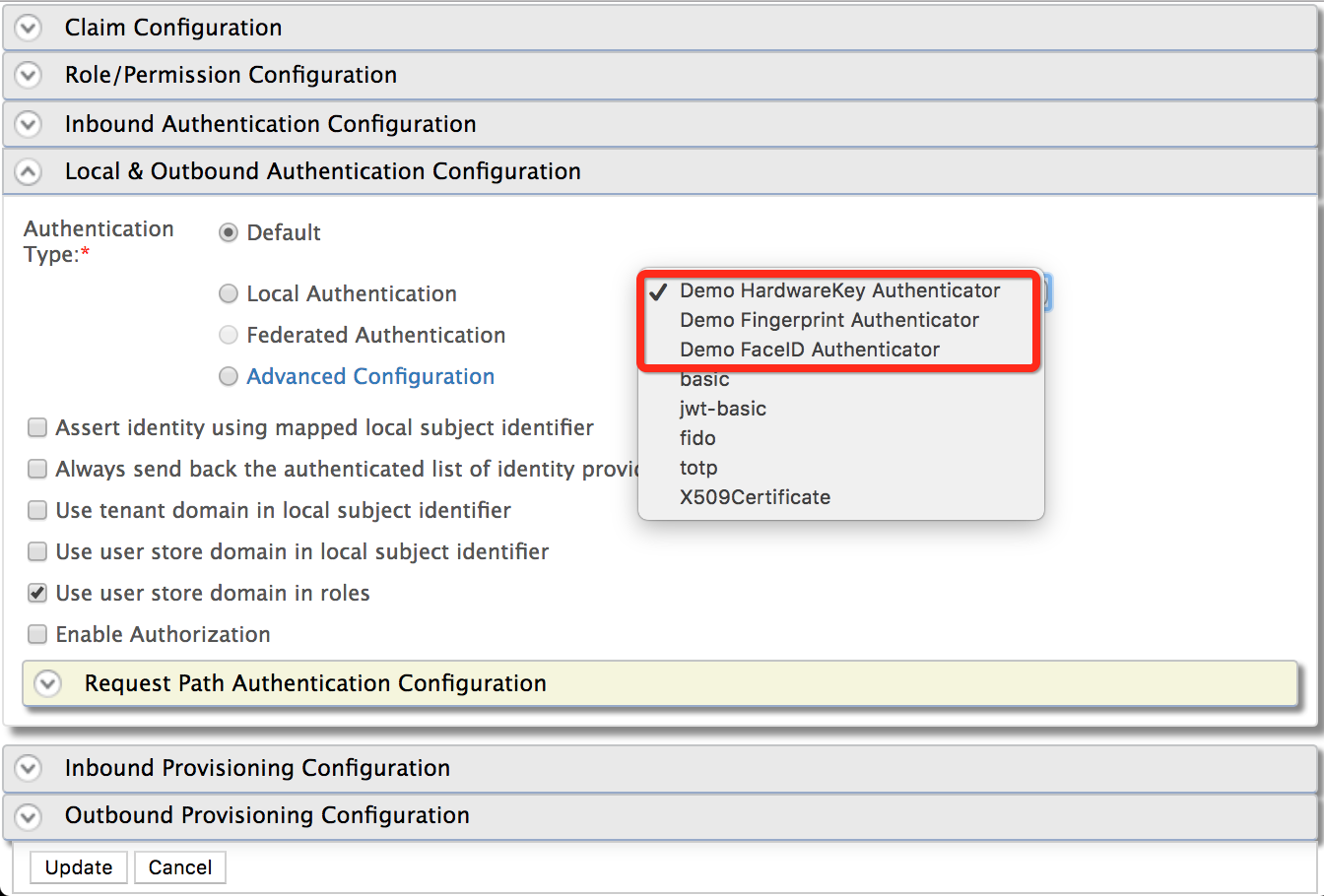
Expand the Local and Outbound Configuration section.
The following authenticators should be available in the local authenticators list.- Demo Fingerprint Authenticator
- Demo Hardware-Key Authenticator
- Demo Face ID Authenticator
Remain in the Management Console.
Note
These Demo Authenticators are provided as a way of learning and experimenting the adaptive authentication templates in realtime. These authenticators perform no real function and should not be used for any production or QA purposes.
-
-
Step 02: Configure the Service Provider¶
In this step, let's configure a service provider for the sample application by setting up inbound authentication.
Info
This tutorial guides you through setting up a service provider for a SAML application. To configure a service provider with other protocols such as OAuth and WS-Federation, see Configuring Inbound Authentication for a Service Provider.
Before you proceed
In the previous step, you have deployed and
registered the saml2-web-app-pickup-dispatch.com webapp.
If you complete that you can skip steps 1 to 4 below and directly jump
to step 5.
-
On the Main tab, click Service Providers > Add and add a new service provider called
saml2-web-app-pickup-dispatch.com.For more information about configuring a service provider, see Adding and Configuring a Service Provider.
-
Expand the Inbound Authentication configuration> SAML2 Web SSO configuration section, and click Configure.
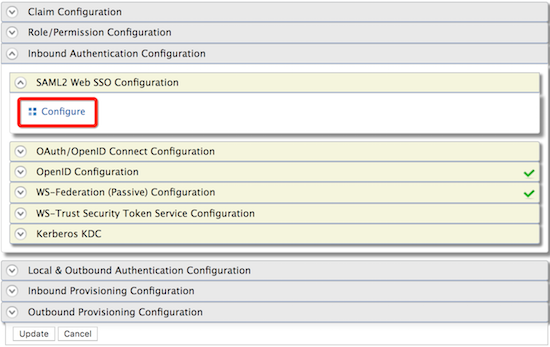
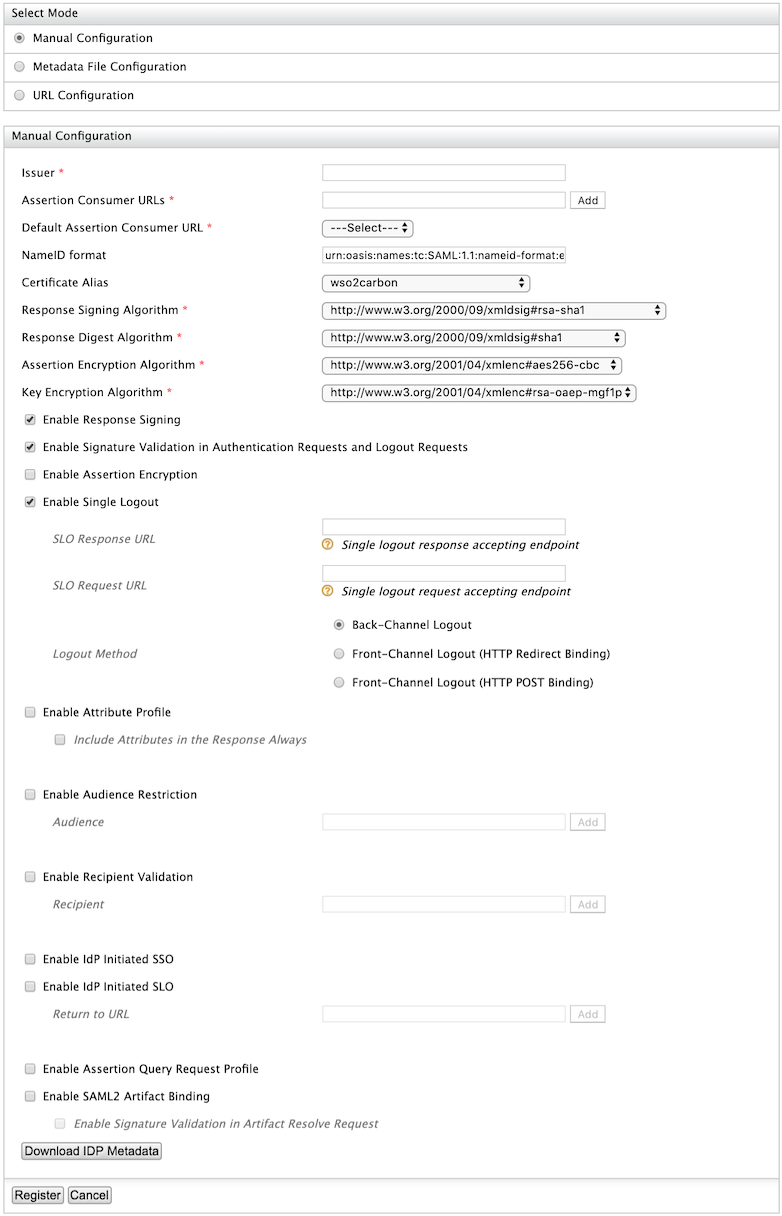
- Fill in the following fields.
- Issuer:
saml2-web-app-pickup-dispatch.com - Assertion Consumer URL:
http://localhost.com:8080/saml2-web-app-pickup-dispatch.com/consumer
- Issuer:
- Leave the rest of the default configurations as it is and click
Register.
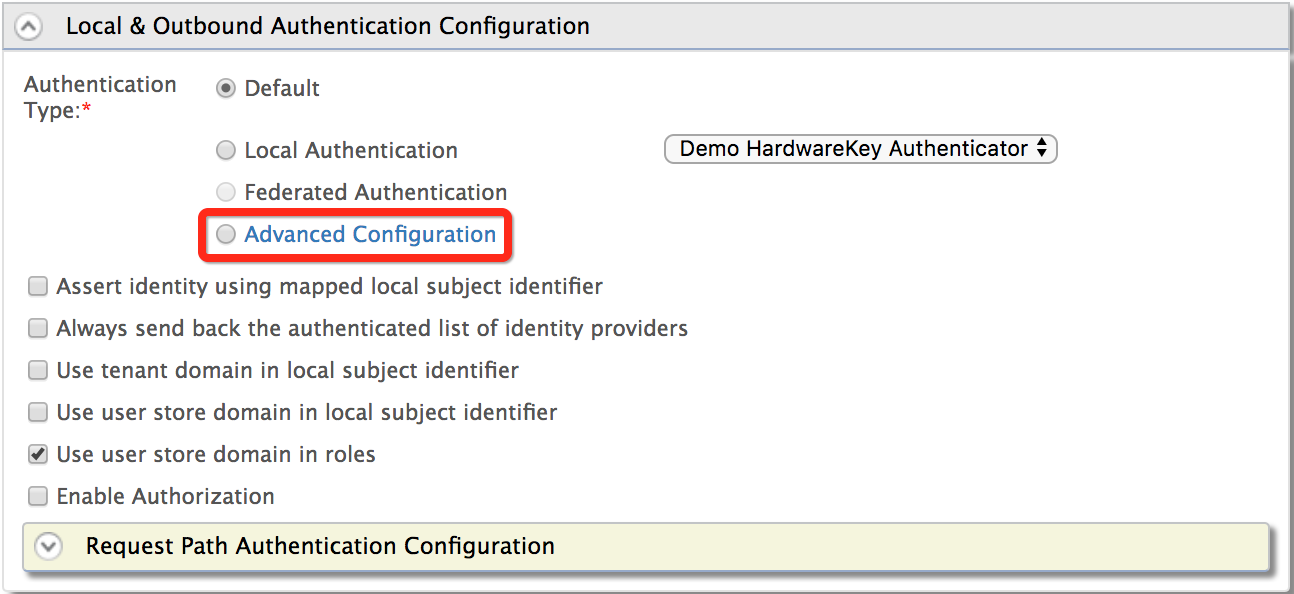
- Expand Local and Outbound Authentication Configuration and click
Advanced Configuration.
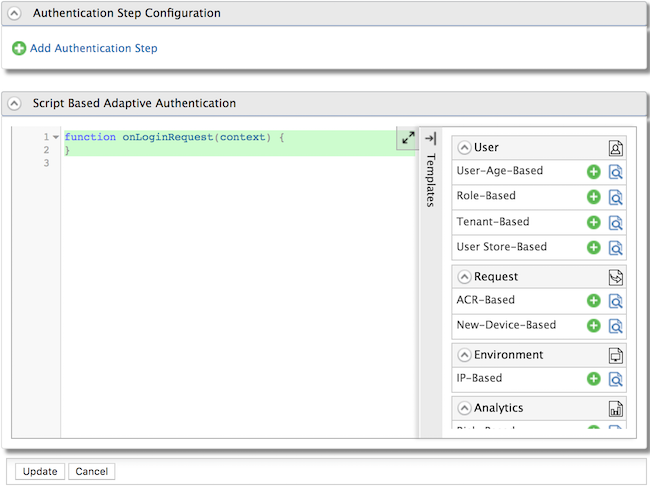
- You can add authentication steps or use a template to configure
adaptive authentication depending on your requirement. For example,
add Demo HardwareKey Authenticator.
- Add the following configuration to the
<IS_HOME>/repository/conf/deployment.tomlfile.
[[resource.access_control]]
context = "/sample-auth(.*)"
secure = false
http_method = "all"What's Next?¶
Now that you have set up the service provider, the sample application, and the demo authenticators, you can try out the scenarios that use pre-defined templates for different adaptive authentication use cases.
Top