Configuring Yahoo¶
Yahoo can be used as a federated authenticator in the Identity Server. Do the following to configure the Identity Server to authenticate users using their Yahoo user accounts.
Tip
Before you begin
- Create a Yahoo developer account .
- Sign in to the WSO2 Identity Server Management
Console at
https://<Server Host>:9443/carbonusing yourusernameandpassword.
-
To navigate to the federated authenticators configuration section, do the following.
- Sign in. Enter your username and password to log on to the Management Console .
- Navigate to the Main menu to access the Identity menu.
Click Add under Identity Providers .
For more information, see Adding and Configuring an Identity Provider . - Fill in the details in the Basic Information section.
-
Expand the Yahoo Configuration form
Before you begin, you need to have an application registered in Yahoo. See Getting Started section in Yahoo document.
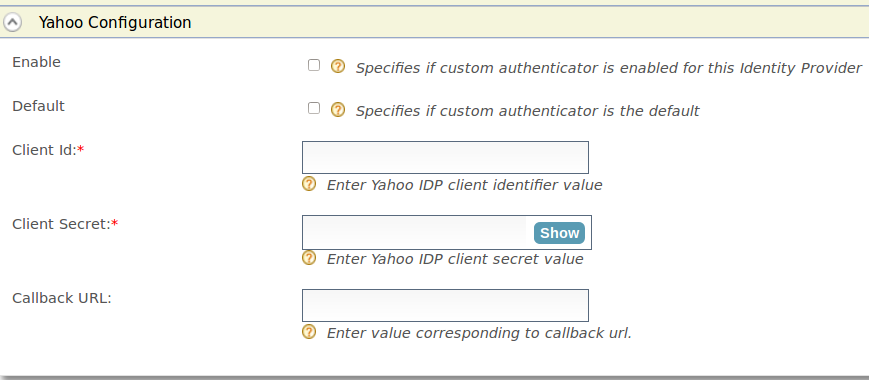
-
Fill in the following fields where relevant.
Field Description Sample value Enable Selecting this option enables Yahoo to be used as an authenticator for users provisioned to the Identity Server. Selected Default Selecting the Default checkbox signifies that Yahoo is the main/default form of authentication. This removes the selection made for any other Default checkboxes for other authenticators. Selected Client Secret This is the password from the Yahoo application. Click the Show button to view the value you enter. 12ffb4dfb2fed67a00846b42126991f8 Callback URL This is the URL to which the browser should be redirected after the authentication is successful. It should have this format: https://(host-name):(port)/acs.https://localhost:9443/commonauth Client Id This is the username from the Yahoo application. 1421263438188909
Related Topics
- Identity Federation is part of the process of configuring an identity provider. For more information on how to configure an identity provider, see Configuring an Identity Provider.