Configuring IP-Based Adaptive Authentication¶
This tutorial demonstrates IP-based adaptive authentication with WSO2 Identity Server using sample authenticators. This is useful if you want to add security for users logging in from external networks or other geographic locations. Using the IP-based adaptive authentication template, you can specify network ranges using the ip address so that users logging in from an external network that is unlisted in the authentication script, are prompted to perform an additional level of authentication, while users logging in from the internal configured network specified on the script can simply provide their credentials (basic authentication) to access a resource.
Follow the instructions given below:
Before you begin
- Set up the service provider and sample application for adaptive authentication. For instructions on how to do this, see Configuring a Service Provider for Adaptive Authentication.
- For more information about adaptive authentication with WSO2 Identity Server, see Adaptive Authentication.
Configuring the sample scenario¶
- Log in to the management console.
- Navigate to Service Providers>List and click Edit on the
saml2-web-app-pickup-dispatch.comservice provider. - Expand the Local and Outbound Configuration section and click Advanced Authentication.
-
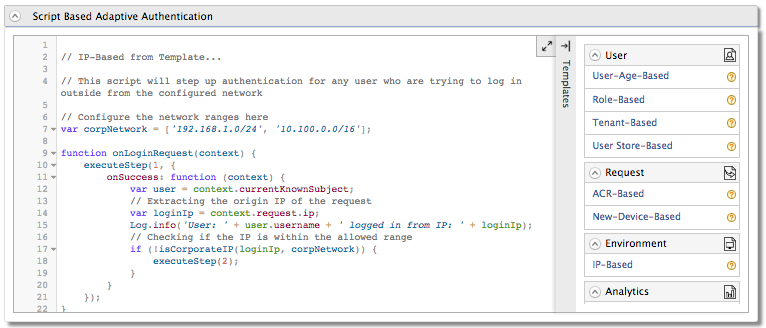
Click on Templates on the right side of the Script Based Conditional Authentication field and then click IP-Based.
-
Click Ok. The authentication script and authentication steps are configured. The authentication script prompts the second step of authentication for users who log in from an IP address that is not included within the network range configured in the script. To try out this scenario, enter the IP address of your machine to define it as an internal network.
var corpNetwork = ['192.168.1.0/24', '10.100.0.0/16']; -
The second authentication step that is added is
totp.However,totpis an authentication step that you would normally use in production. To try out this scenario sample authenticators with the sample application, delete thetotpauthenticator and add the following sample authenticator instead.-
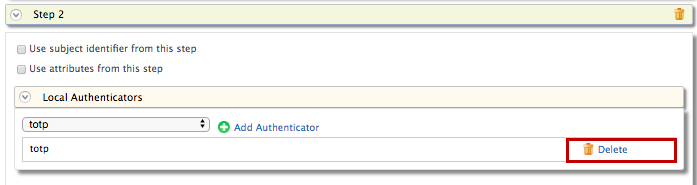
Click Delete to remove the
totpauthenticator from Step 2 (the second authentication step).
-
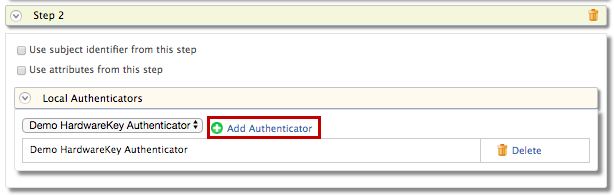
Select Demo Hardware Key Authenticator and click Add.
-
-
Click Update.
Trying out the sample scenario¶
- Create a new user named Alex with login permissions.
- Access the following sample PickUp application URL: http://localhost.com:8080/saml2-web-app-pickup-dispatch.com .
- Click Login and enter Alex's credentials. Note that you are successfully logged in after only the basic authentication step because you are logging in from an IP address that is within the configured network.
- On the management console, navigate to Service Providers>List and click Edit on the saml2-web-app-pickup-dispatch.com service provider.
-
Edit the authentication script in the Script Based Conditional Authentication field and enter an IP address that is outside your network range.
var corpNetwork = ['192.168.1.0/24', '10.100.0.0/16']; -
Click Update.
- Access the following sample PickUp application URL: http://localhost.com:8080/saml2-web-app-pickup-dispatch.com .
-
Click Login and enter Alex's credentials. Note that you are now prompted to provide hardware key authentication because you are logging in from an IP address that is external to the configured network.
Tip
You can also try this scenario with two different machines in different networks to simulate a real world scenario.