Logging in to Salesforce using the Identity Server¶
This topic provides instructions on how to log into Salesforce using your WSO2 Identity Server credentials.
Before you begin!
When you log into Salesforce, you normally use an email address. So, to integrate this with the Identity Server, you need to configure WSO2 IS to enable users to log in using their email addresses.
Click here to get the steps on how configure the email address as the username.
Warning
Configuring the email address as the username in an already running Identity Server is not the production recommended way. Therefore, make sure to configure it before you begin working with WSO2 IS.
-
Open the
/repository/conf/deployment.toml file and add the following configuration. [tenant_mgt] enable_email_domain=true -
Open the
<IS_HOME>/repository/conf/claim-config.xmlfile and configure theAttributeIDproperty as mail for thehttp://wso2.org/claims/usernameclaim URI as shown below.Warning
This file is checked only when WSO2 IS is starting for the first time. Therefore, if you haven't configured this property at the time of starting up the server for the first time, you will get errors at the start up.
<Claim> <ClaimURI>http://wso2.org/claims/username</ClaimURI> <DisplayName>Username</DisplayName> <AttributeID>mail</AttributeID> <Description>Username</Description> </Claim> -
Open the
<IS_HOME>/repository/conf/identity/identity-mgt.propertiesfile and set the following property totrue.Info
This step is required due to a known issue that prevents the confirmation codes from being removed after they are used when email usernames are enabled. This occurs because the '@' character and some special characters are not allowed in the registry. To overcome this issue, enable hashed usernames when saving the confirmation codes by configuring the properties below.
UserInfoRecovery.UseHashedUserNames=trueOptionally, you can also configure the following property to determine which hash algorithm to use.
UserInfoRecovery.UsernameHashAlg=SHA-1 -
Configure the following set of parameters in the user store configuration, depending on the type of user store you are connected to (LDAP/Active Directory/ JDBC).
Parameter Description user_name_attribute
Set the mail attribute of the user. LDAP/Active Directory only
[user_store]
user_name_attribute = "mail"user_name_search_filterUse the mail attribute of the user instead of
cnoruid. LDAP/Active Directory only[user_store]
user_name_search_filter = "(&(objectClass=person)(uid=?))"user_name_list_filterUse the mail attribute of the user. LDAP/Active Directory only
[user_store]
user_name_list_filter = "(&(objectClass=identityPerson)(mail=*)))"username_javas_cript_regexChange this property that is under the relevant user store manager tag as follows. This property allows you to add special characters like "@" in the username.
[user_store]
username_javas_cript_regex = "^[a-zA-Z0-9.-]+@[a-zA-Z0-9.-]+.[a-zA-Z]{2,4}$"username_java_regexThis is a regular expression to validate usernames. By default, strings have a length of 5 to 30. Only non-empty characters are allowed. You can provide ranges of alphabets, numbers and also ranges of ASCII values in the RegEx properties.
[user_store]
username_java_regex = "^[a-zA-Z0-9.-]+@[a-zA-Z0-9.-]+.[a-zA-Z]{2,4}$"Realm configurations The
[super_admin]username must use the email attribute of the admin user.[admin_user]
username="[email protected]"
password="admin"Note
Before this configuration, the user having the username admin and password admin was considered the super administrator. The super administrator user cannot be deleted.
After this configuration, the user having the username [email protected] is considered the super administrator. The user having the username admin is considered as a normal administrator.
Tip
If you changed the password of the admin user to something other than 'admin', start the WSO2 IS server using the -Dsetup parameter as shown in the command below.
sh wso2server.sh -DsetupInfo
With these configuration users can log in to super tenant with both email user name ( [email protected] ) or non-email user names (larry). But for tenant only email user names allowed (tod@ gmail.com @ wso2.com )
Note
You can configure email user name without enabling
EnableEmailUserNameproperty, then users can log into both super tenant and tenant using email and non-email user names. But super tenant users should always use @carbon.super at the end of user names. -
Restart the server.
Related Topics
For more information on how to configure primary and secondary user stores, see Configuring User Stores.
Let's get started!
Configuring Salesforce¶
-
Sign up as a Salesforce developer if you don't have an account. If you already have an account, move on to step 2 and log in to Salesforce.
- Fill out the relevant information found in the following URL: https://developer.salesforce.com/signup
- Click Sign me up.
- You will receive a security token by email to confirm your new account. If you did not receive the email successfully, you will be able to reset it by following the steps given here.
-
Log in with your new credentials as a Salesforce developer. Do this by clicking the Login link in the top right hand side of https://login.salesforce.com/.
Note
This document is explained using the Salesforce lightning theme. If you are using the classic theme, follow the steps given below to switch to the lightning theme.
Click here to find the steps on how to switch from the classic to the lightning theme.
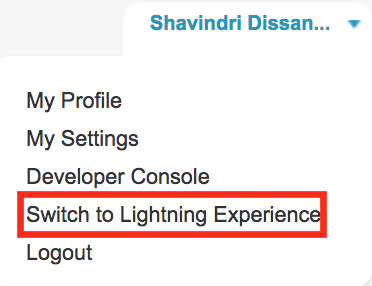
- Click your username to expand the drop down.
- Click Switch to Lightning Experience.
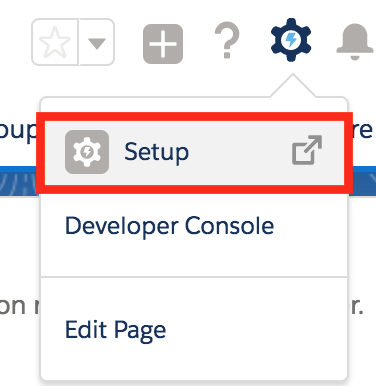
- Click the settings icon on the top-right-hand corner, and click
Set Up.
Now you are navigated to the lightening theme of Salesforce.
-
Click Allow to enable Salesforce to access your basic information.
-
Once you are logged in, create a new domain and access it. To do this, do the following steps.
- Search for My Domain in the search bar that is on the left
navigation panel.
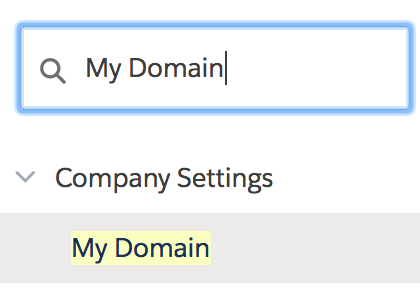
- Click My Domain.
-
In the page that appears, come up with a name for your domain. You can check if the domain is available by clicking the Check Availability button.
Info
For the page given below to load on your browser, make sure that the Salesforce cookies are not blocked.
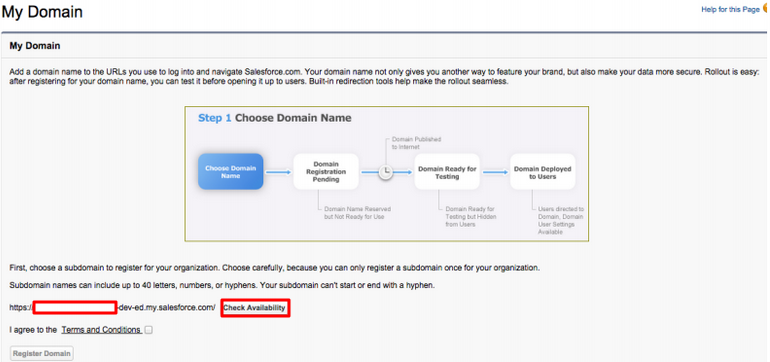
-
If the domain is available, select I agree to Terms and Conditions and click Register Domain to register your new domain.
-
Once the domain is registered to your account, click the Click here to login button to test this out.
- Search for My Domain in the search bar that is on the left
navigation panel.
-
On the left navigation menu, search for Single Sign-On Settings , and click it.
-
In the page that appears, click Edit and then select the SAML Enabled check box to enable federated single sign-on using SAML.
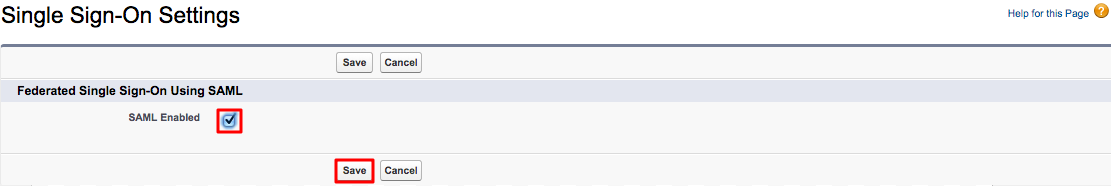
-
Click Save to save this configuration change.
-
Click New under SAML Single Sign-On Settings. The following screen appears.
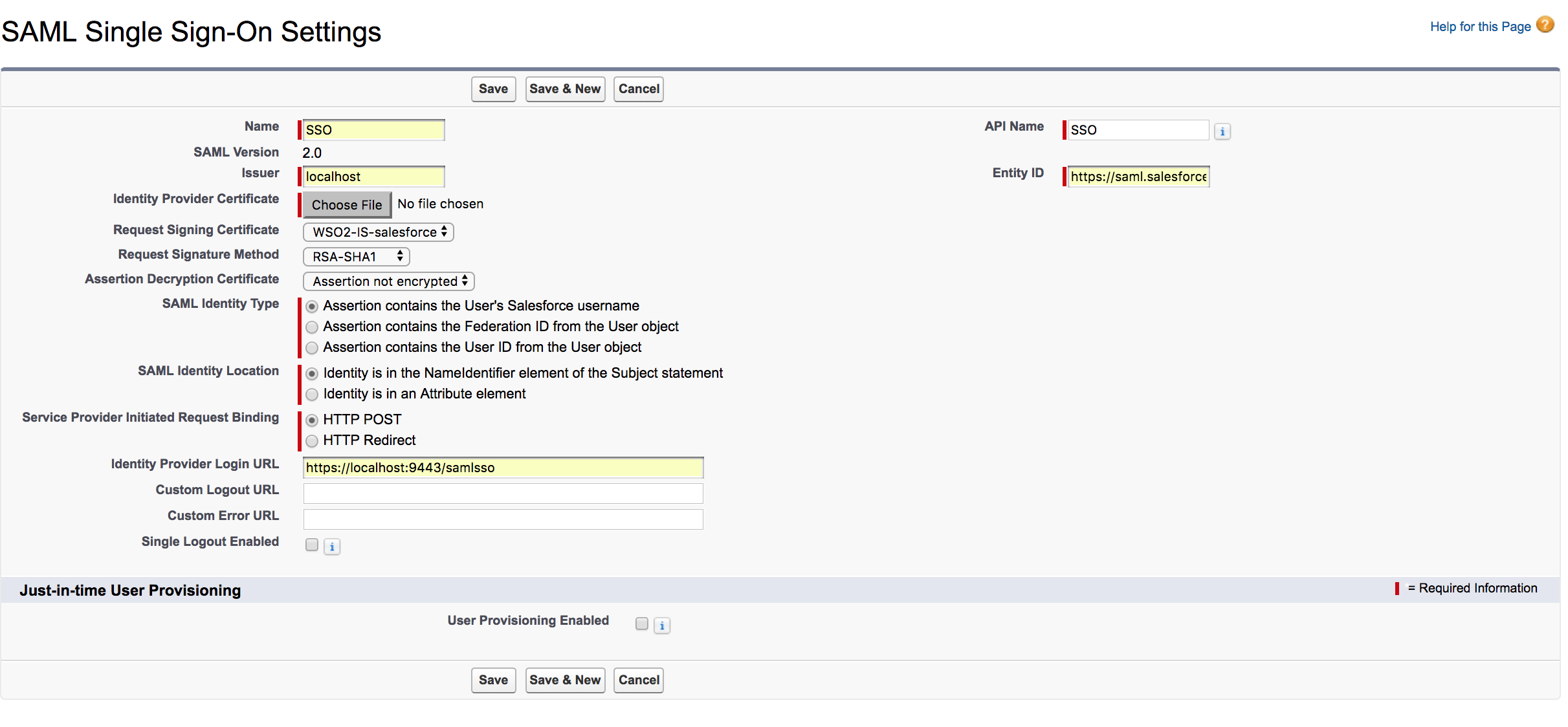
Ensure that you configure the following properties.
Click Save to save your configurations.
-
Go to Custom Settings in the left navigation pane and click My Domain.
-
Click Deploy to Users. Click Ok to the confirmation message that appears.
-
In the page that appears, you must configure the Authentication Configuration section. Scroll down to this section and click Edit.
-
Under Authentication Service, select SSO instead of Login Page.
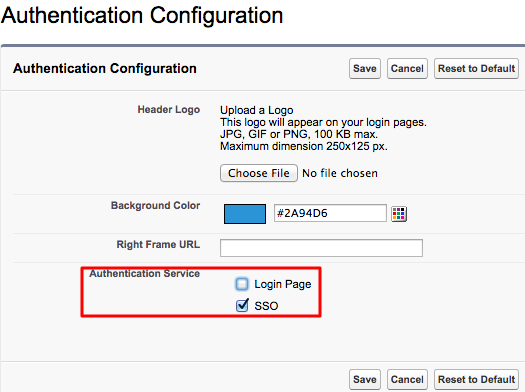
-
Click Save.
Configure claims¶
Follow the steps below to map the Salesforce attributes to WSO2 IS claims using the WSO2 IS console.
-
Log in to the Management Console.
The default username and password of the administrator is both admin.
-
On the Main menu, click Claims > Add.
-
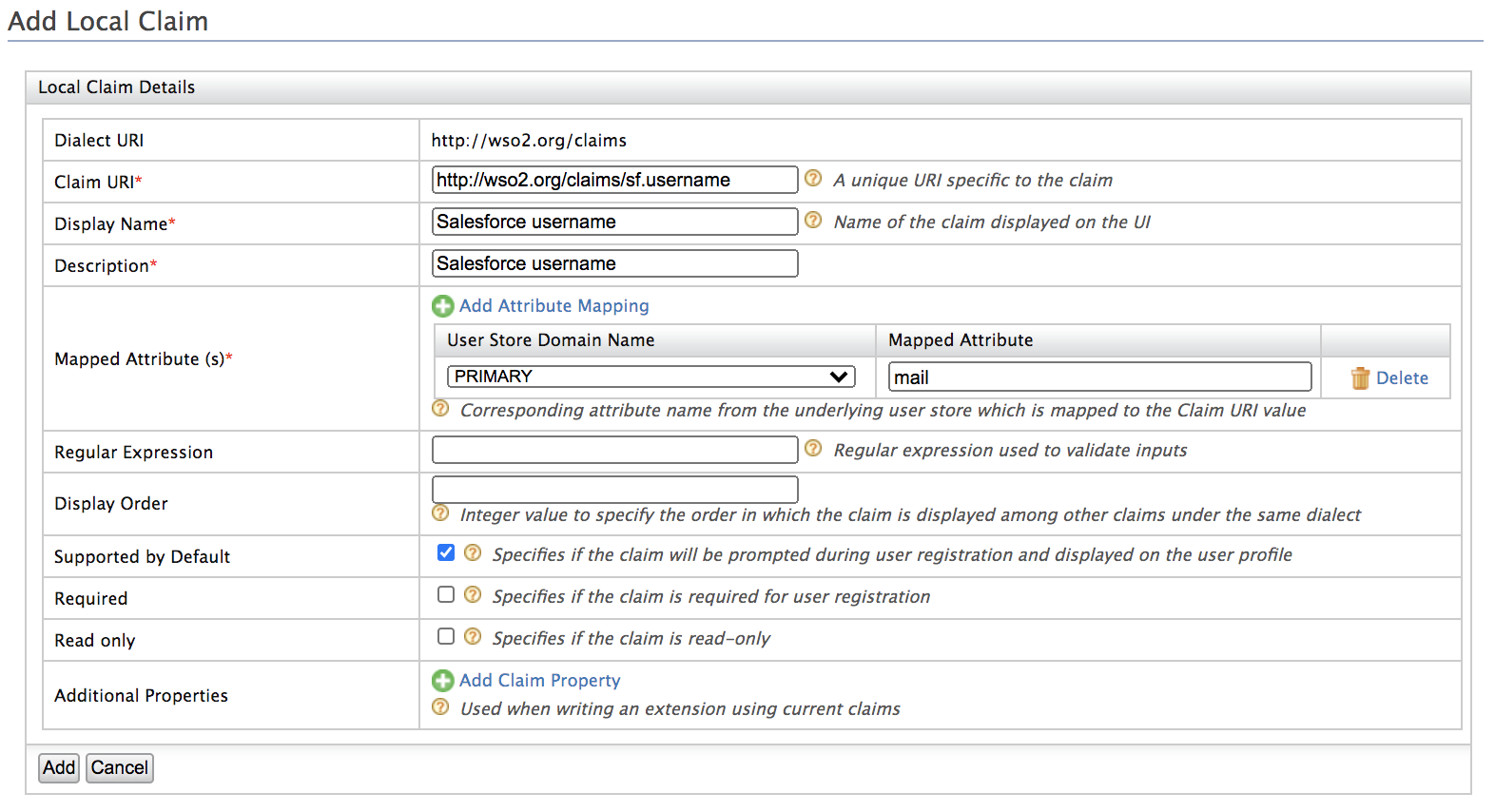
Click Add Local Claim.
-
Add the following claim:
- Claim URI: http://wso2.org/claims/sf.username
- Display Name: Salesforce username
- Description: Salesforce username
- Mapped Attribute: mail
-
Supported by Default: Selected
Configuring the service provider¶
Follow the steps given below to configure salesforce as a service provider in WSO2 IS.
-
Sign in. Enter your username and password to log on to the Management Console.
The default username and password of the administrator is both admin.
-
Navigate to the Main menu to access the Identity menu. Click Add under Service Providers.
-
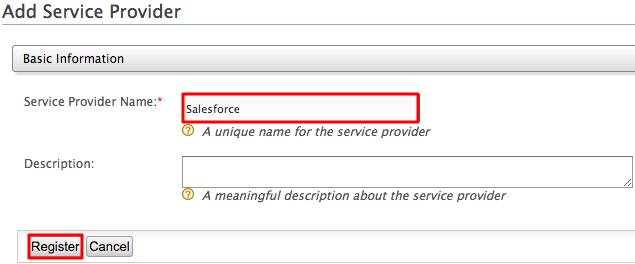
Fill in the Service Provider Name and provide a brief Description of the service provider. Only Service Provider Name is a required field and we use Salesforce as the name for this example.
-
Click Register.
-
Expand the Inbound Authentication Configuration and the SAML2 Web SSO Configuration and click Configure.
-
In the form that appears, fill out the following configuration details required for single sign-on. For more details about attributes in the following configuration refer SAML2 Web SSO Configuration .
Field Value Description Issuer https://saml.salesforce.comThis is the <saml:Issuer>element that contains the unique identifier of the service provider. This is the same value you entered as the Entity-ID when creating the salesforce application. This is also the issuer value specified in the SAML Authentication Request issued by the service provider. When configuring single-sign-on across Carbon servers, ensure that this value is equal to the service_provider_id value mentioned in thedeployment.tomlfile of the relying party Carbon server.Assertion Consumer URL See the steps in the tip given below the table for instructions on how to get the Salesforce Assertion Consumer URL.
This is the URL to which the browser should be redirected to after the authentication is successful. This is the Assertion Consumer Service (ACS) URL of the service provider. The identity provider redirects the SAML2 response to this ACS URL. However, if the SAML2 request is signed and SAML2 request contains the ACS URL, the Identity Server will honor the ACS URL of the SAML2 request. In this case, you must use your Salesforce login URL. In Salesforce, click Security Controls on your left menu and then click Single Sign-On Settings. In the page that appears, click on the SSO settings that you created to view the details. Use the Salesforce Login URL listed there for this value. NameID Format The default value can be used here. This defines the name identifier formats supported by the identity provider. The service provider and identity provider usually communicate with each other regarding a specific subject. That subject should be identified through a Name-Identifier (NameID) , which should be in some format so that It is easy for the other party to identify it based on the format. Name identifiers are used to provide information regarding a user. Enable Response Signing Selected Select Enable Response Signing to sign the SAML2 Responses returned after the authentication process.
Enable Attribute Profile Selected Select Enable Attribute Profile to enable this and add a claim by entering the claim link and clicking the Add Claim button. The Identity Server provides support for a basic attribute profile where the identity provider can include the user’s attributes in the SAML Assertions as part of the attribute statement. Once you select the check box to Include Attributes in the Response Always , the identity provider always includes the attribute values related to the selected claims in the SAML attribute statement. Follow the steps below to get the Salesforce Assertion Consumer URL
-
Log into the Salesforce developer account: https://login.salesforce.com
-
Search for My Domain in the search bar that is on the left navigation panel.
-
Click My Domain. You are navigated to the domain you created when configuring salesforce
-
Click Edit under Authentication Configurations. You are navigated to a new page having the following URl:
https://<DOMAIN_NAME>/domainname/EditLogin.apexp -
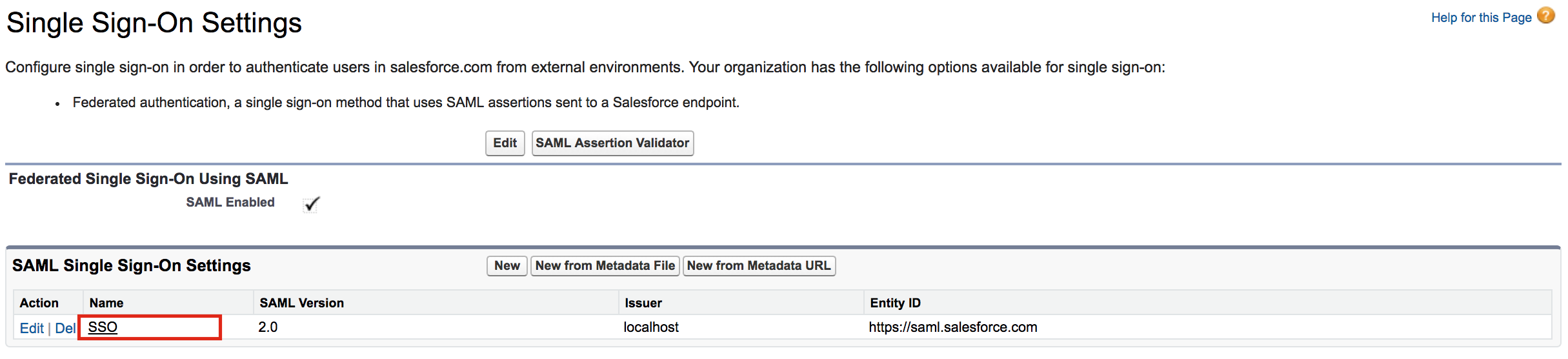
On the left navigation menu, search for Single Sign-On Settings , and click it.
-
Click on the name of the Single Sign-On Setting you created. In this case, click SSO.
-
Copy the URL that is defined as the Login URL to access Salesforce.
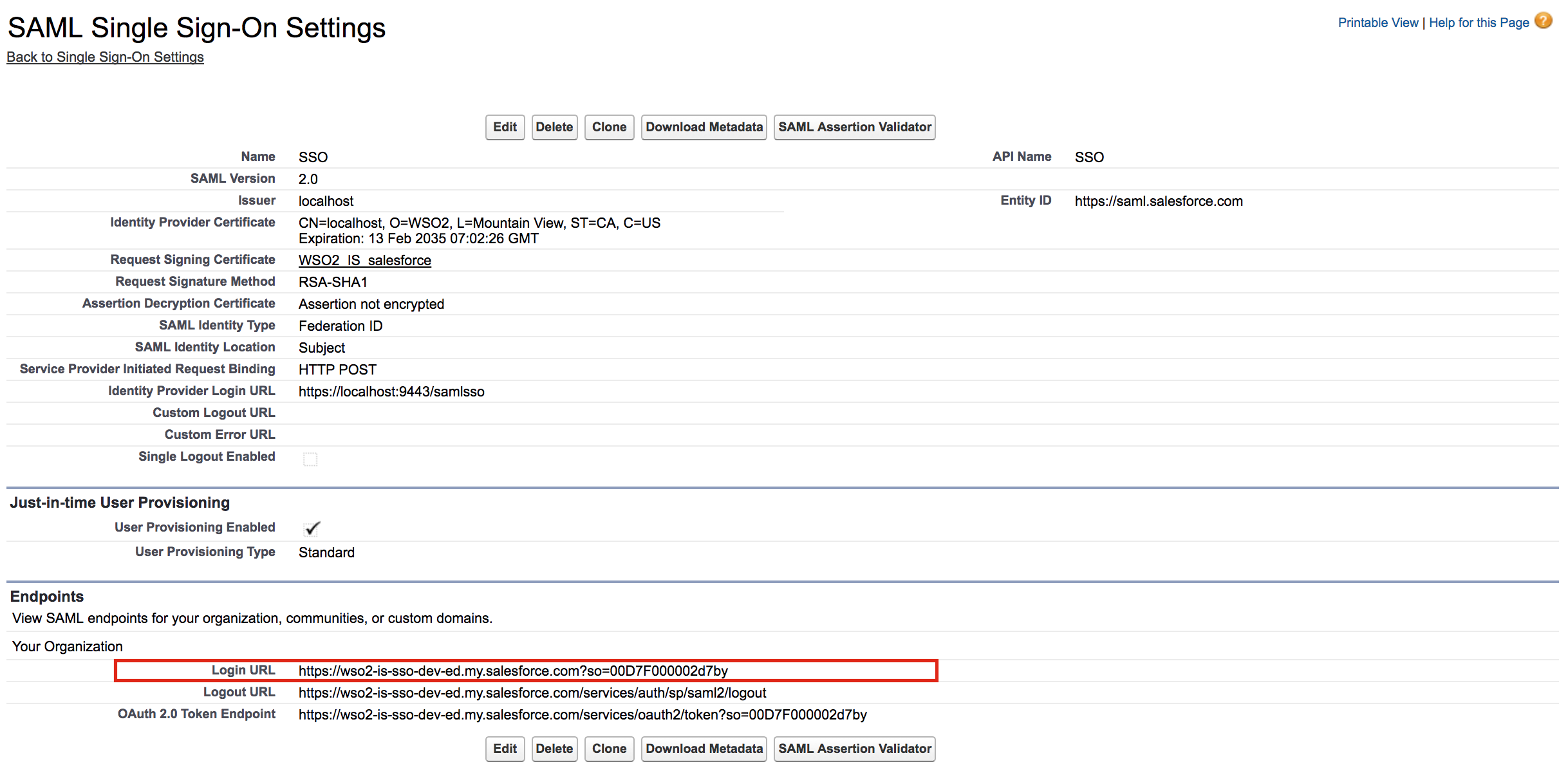
-
-
Click Update to save your configurations.
-
Expand the Claim Configuration tab.
-
Select Define Custom Claim Dialect and then click Add Claim URI to add the following set of claims.
Service Provider Claim Local Claim Requested Claim Mandatory Claim User.ProfileId https://wso2.org/claims/role Selected Selected User.Username https://wso2.org/claims/username Selected Selected User.Email https://wso2.org/claims/emailaddress Selected Selected User.LastName https://wso2.org/claims/lastname Selected Selected 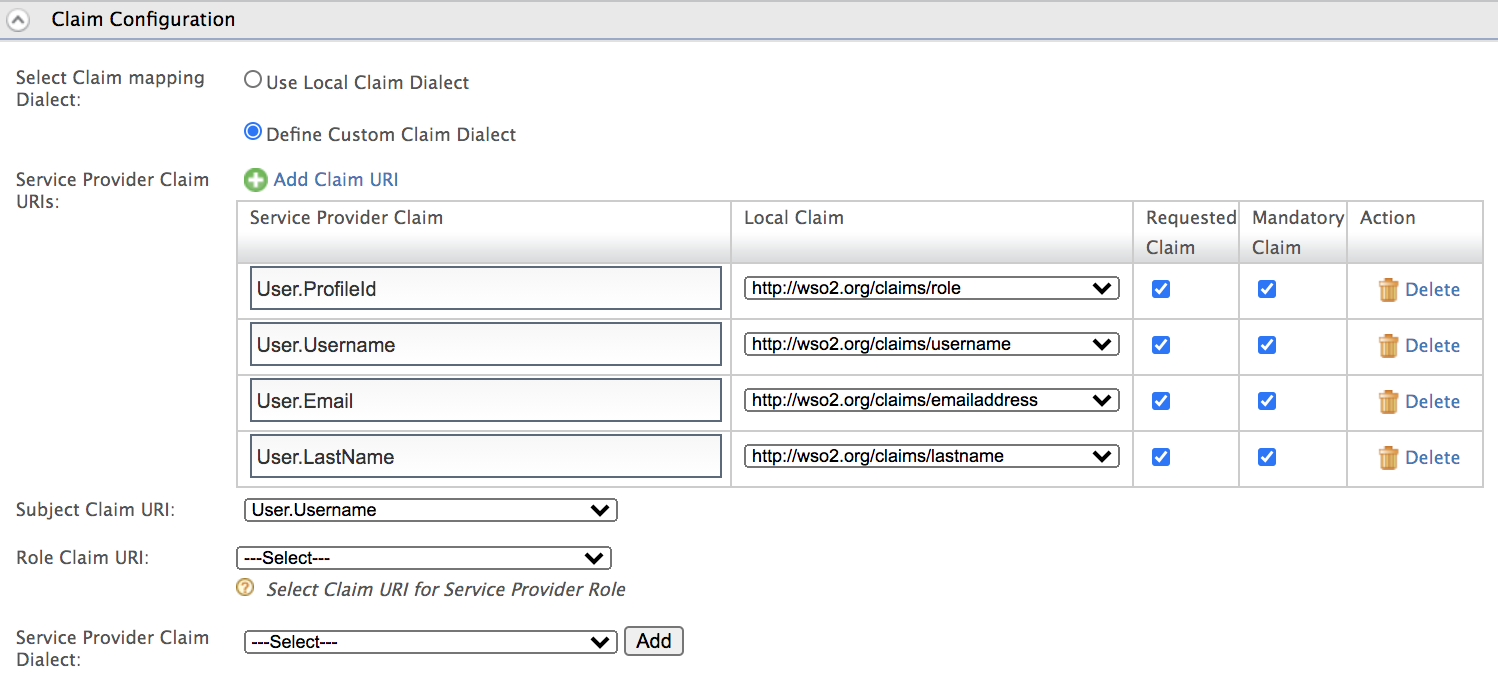
-
Select
User.Usernameas the Subject Claim URI. -
Expand the Role/Permission Configuration tab and expand Role Mapping.
-
Click Add Role Mapping to add the following role mappings.
Local Role Service Provider Role sales_user Standard Platform User solution_manager Solution Manager 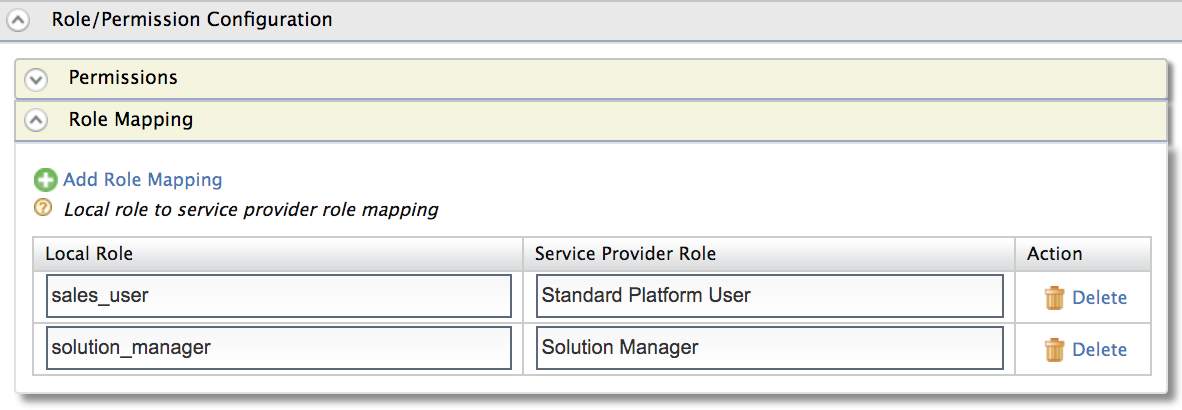
-
Click Update to save the configurations.
Testing the configurations¶
Do the following steps to test out the configurations for a new user in Salesforce and the Identity Server.
-
Create a user in WSO2 IS.
- Once you log in to the Identity Server, navigate to the Main menu in the Management Console, click Add under Users and Roles.
- Click Users. This link is only visible to users with the Admin role.
- Click Add New User. When adding a new user, use an email
address as the username.
Since it is not mandatory to assign a role to a user in this tutorial, click Finish.
-
Create a user in Salesforce. This user should have the same email address as the user in WSO2 IS
- Log in to the Salesforce developer account: https://login.salesforce.com/.
- On the left navigation pane, under ADMINISTRATION, click Users under Users.
- On the page that appears, click the New User button to create a new user.
-
Create a user with the same username as the one you created in the Identity Server. Click Save to save your changes. An email will be sent to the email address you provided for the user.
Note
This is mainly for testing purposes. In a real business scenario, you would be more likely to use Just-In-Time (JIT) provisioning to provision a user to Salesforce.
-
Access your Salesforce login URL on an incognito or private browser.
Info
The salesforce login URL is unique to your Salesforce application. Follow the steps given below to get this URL:
-
Search for My Domain in the search bar that is on the left navigation panel.
-
Click My Domain and you are navigated to the domain you created under the section Configuring Salesforce.
-
Click Edit under Authentication Configurations and you are navigated to a new page having the following URl:
https://<DOMAIN_NAME>/domainname/EditLogin.apexp -
On the left navigation menu, expand Security Controls, and click, Single Sign-On Settings.
-
Click on the name of the Single Sign-On Setting you created. In this case, click SSO.
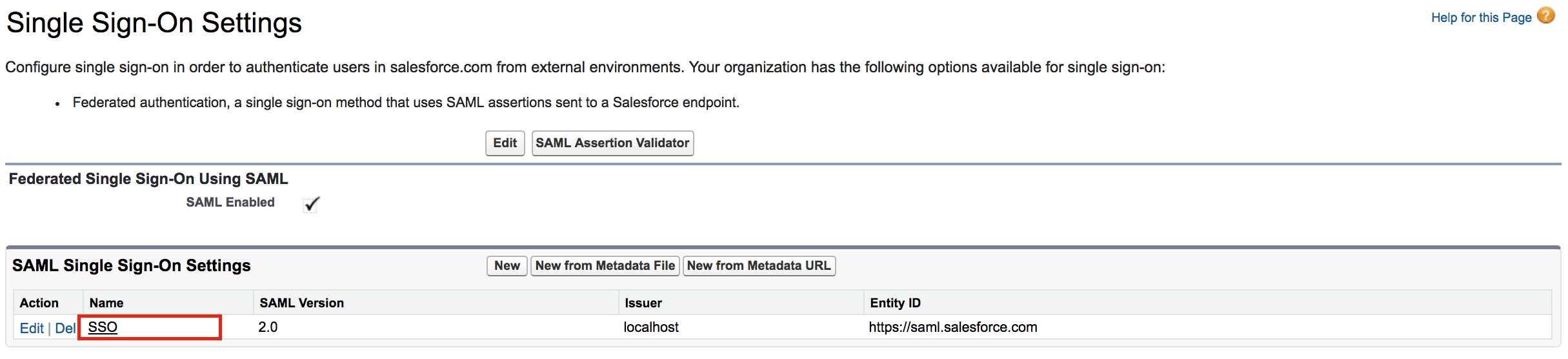
-
Copy the URL that is defined for Login URL to access Salesforce.
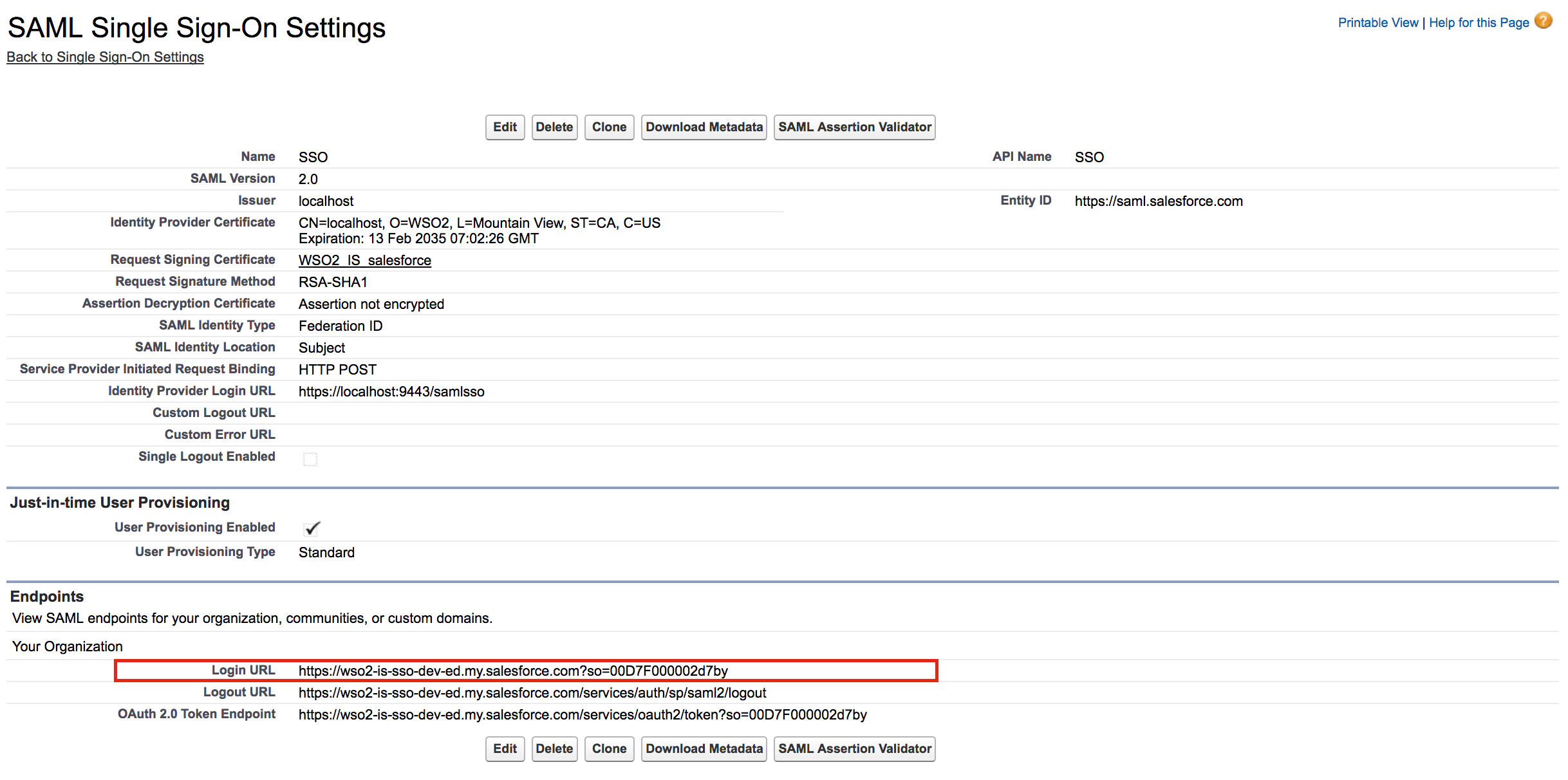
-
-
Log in using the new credentials of the user you just created. You are then redirected back to Salesforce.
Troubleshooting guidelines¶
Additional troubleshooting information regarding any Salesforce side SSO failures can be retrieved by using Salesforce SAML Assertion Validator. Further information regarding the steps are available here .
Top